IBM Adds AI-Enhanced Data Resilience Capabilities to Combat Ransomware and Threats with Enhanced Storage Solutions
AI-enhanced versions of FlashCore Module technology available inside FlashSystem products and new version of Storage Defender software to help organizations improve ability to detect and respond to ransomware and other cyberattacks that threaten data.
This is a Press Release edited by StorageNewsletter.com on March 7, 2024 at 2:02 pm![]() By Sam Werner, VP, storage product management, IBM Corp.
By Sam Werner, VP, storage product management, IBM Corp.
Cyberattacks are an existential risk, with 89% of organizations ranking ransomware as one of the top five threats to their viability, according to a November 2023 report from TechTarget’s Enterprise Strategy Group, an analyst firm. [1]
And this is just one of many risks to corporate data – insider threats, data exfiltration, hardware failures, and natural disasters also pose significant danger. Moreover, as the just-released 2024 IBM X-Force Threat Intelligence Index states, as the generative AI market becomes more established, it could trigger the maturity of AI as an attack surface, mobilizing even further investment in new tools from cybercriminals. The report notes that enterprises should also recognize that their existing underlying infrastructure is a gateway to their AI models that doesn’t require novel tactics from attackers to target. [2]
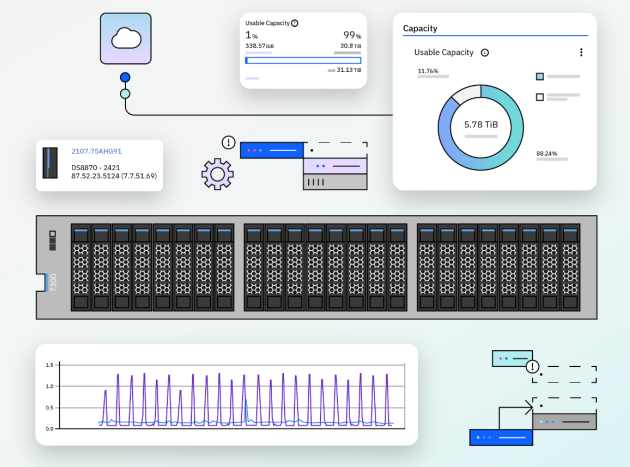
IBM Storage FlashSystem

To help clients counter these threats with earlier and more accurate detection, we’re announcing AI-enhanced versions of the IBM FlashCore Module technology available inside new IBM Storage FlashSystem products and a new version of IBM Storage Defender software to help organizations improve their ability to detect and respond to ransomware and other cyberattacks that threaten their data.
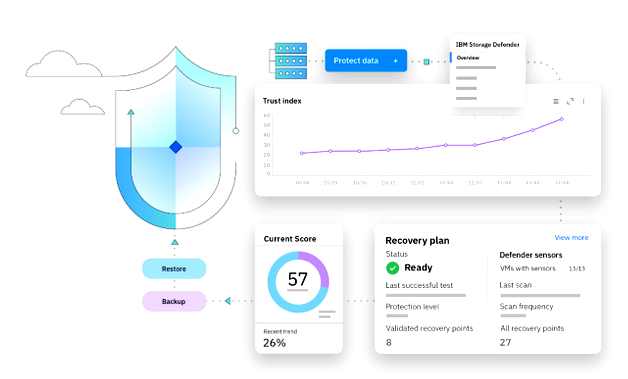
Storage Defender
The newly available 4th gen of FlashCore Module (FCM) technology enables AI capabilities within the FlashSystem family. FCM works with Storage Defender to provide end-to-end data resilience across primary and secondary workloads with AI-powered sensors designed for earlier notification of cyber threats to help enterprises recover faster. (see to experience IBM FlashSystem in a virtual demo).
Early detection of threats in data stream
Existing FlashSystem products scan all incoming data down to block level granularity without impact to performance as it’s being written, using inline data corruption detection software and cloud-based AI to help identify anomalies that might indicate the start of a cyberattack, thereby enabling the system to detect, respond, and rapidly recover with immutable copies. The new technology enabled by FCM4 is designed to continuously monitor statistics gathered from every single I/O using ML models to detect anomalies like ransomware in less than a minute. [3]
“Cyber threats evolve rapidly, making early detection a critical step when we help clients respond to attacks,” said Daneyand ‘DJ’ Singley, executive director, Mapsys. “We’ve turned to FlashSystem and FCM3 to help our clients achieve rapid recovery, and with the new FCM4 technology in new FlashSystem arrays, we anticipate the ability to take immediate action to thwart attacks.”
FlashSystem products already measure parameters such as the compressibility and randomness, or entropy of data, and pass this information to IBM Storage Insights software so that it can alert operators when a workload anomaly has been detected, such as ransomware starting to encrypt an application’s data. The FCM4 technology in new FlashSystem arrays is designed to capture and summarize detailed statistics about every I/O in real time. FlashSystem uses ML models to distinguish ransomware and malware from normal behavior, positioning organizations to take action and keep operating in the event of an attack.
“Organizations need to take a ‘defense in depth’ approach against ransomware and other cyberattacks, especially as malware becomes increasingly sophisticated,” said Dave Pearson, research VP, infrastructure, IDC. “Storage infrastructure is another layer where cyber resilience can improve, and IBM built its new FlashCore Module 4 with AI-based capabilities designed to speed ransomware detection, reduce the spread and impact, and accelerate recovery.“
Getting smarter at identifying threats across workloads
Storage Defender software offers end-to-end data resilience in modern hybrid multi-cloud IT environments that includes VMs, databases, applications, file systems, SaaS workloads, and containers. The new version of Storage Defender expands its threat detection capabilities to help build trustworthiness of copies as a baseline for teams to begin recovery from cyberattacks. Additionally, Storage Defender includes AI-powered sensors developed by IBM Research that are engineered to rapidly detect ransomware and other advanced threats with high accuracy. Defender raises high fidelity alerts to security tools to reduce the security breach blast radius and help enterprises recover from attacks.
We’ve added workload and storage inventory management capabilities to Storage Defender designed to help organizations assess the extent of their applications and data. This can help them incorporate their assets in a business continuity plan to recover a minimum viable company after a cyberattack. Defender also adds the ability to orchestrate and automate the recovery of VMware applications.
Part of Defender’s appeal is the ease with which it integrates with other IBM Storage and IBM Security solutions, including IBM QRadar, IBM Guardium, FlashSystem, IBM Storage Scale, IBM Storage Ceph , and IBM Fusion. Beyond IBM solutions, Defender integrates with Cohesity and will integrate with other 3rd-party data platforms to bring end to end data resilience across the enterprise data estate.
Better together
Individually, both FlashSystem and Defender have capabilities that can help make organizations more data resilient, but they’re even better together. For example, storage administrators can now create protection groups that include specific volumes and are automatically backed up according to user-defined policies. Immutable copies of data can now be restored or recovered to multiple target locations, including different locations when recovering from a cyberattack. Plus, immutable copies can be replicated to another Storage Defender cluster for an additional layer of protection.
We’ve also engineered settings that allow administrators to automate the creation of Safeguarded Copy snapshots, cyber-resilient point-in-time copies of data that cannot be changed or deleted through user errors, malicious actions, or cyberattacks. Isolating these backup copies from production data is designed to enable organizations to recover data more quickly after a data loss event.
News reports show that threat actors are now deploying AI-based cyberattacks, and we must fight fire with fire. The FlashCore Module hardware and Storage Defender software both leverage IBM’s AI capabilities to help them better address this challenge. The company’s product portfolio is not only helping to deliver data resilience to clients, including many of the world’s largest financial and health care organizations, to help them avoid threats in the 1st place, but also helping them accelerate the recovery process in the event that attackers have been able to get through.
[1] 2023 Ransomware Preparedness: Lighting the Way to Readiness and Mitigation, published by Enterprise Strategy Group/TechTarget, November 2023
[2] IBM Report: Identity Comes Under Attack, Straining Enterprises’ Recovery Time from Breaches, published by IBM Security, February 2024
[3] Disclaimer: Internal experimentation by IBM Research has demonstrated detection of ransomware within 1mn of the ransomware starting its encryption process. This experiment was done on a FlashSystem 5200 with 6 FCMs with the 4.1 firmware load. The 5200 had 8.6.3 GA level software loaded. The host connected to the 5200 was running Linux with XFS Filesystem. In this particular case, the IBM ransomware simulator called WannaLaugh was used. Underlying system must be compatible with FCM4.1 and version 8.6.3 GA level software loaded in order to receive results obtained.










 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter

