Pivot3 Unveils Policy-Based Security Management Capabilities in Core Intelligence Engine
To streamline security and regulatory compliance across edge, core and cloud
This is a Press Release edited by StorageNewsletter.com on December 19, 2018 at 2:24 pmPivot3, Inc. announced policy-based security management capabilities in its core Intelligence Engine.
These expanded capabilities allow organizations to automate and simplify the process of protecting sensitive data with standards-based security for encryption and key management. The company’s platform enhancements facilitate regulatory compliance as customers acquire and manage data across the edge, core and cloud.
“With security threats on the rise and regulations around data security increasing, CIOs and CISOs face new challenges as they seek to protect sensitive, mission-critical data without compromising performance,” said John Spiers, VP, strategy, Pivot3. “Customers rely on us every day to simplify management at scale. This extension of Pivot3’s Intelligence Engine brings new confidence to IT in knowing that data can be secured and protected as it moves across the entire hybrid cloud infrastructure.“
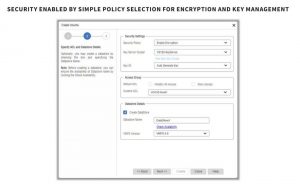
Intelligence Engine enhances application performance, data placement, data protection, and monitoring and analytics, enabling customers to confidently consolidate multiple, mixed-application workloads on HCI while reducing time, cost and complexity. The addition of automated, policy-based security management capabilities to the firm’s engine enables customers to implement to use policies to integrate data encryption and key management into the same workflow for managing applications and storage.
Click to enlarge
To address the increased regulation and compliance requirements, the new capability includes flexible, secure multi-tenancy and data-at-rest encryption at a system, volume or VM level, compliant with Federal Information Processing Standards (FIPS) 140-2. The company designed its data encryption algorithms to leverage Xeon CPUs AES New Instructions (AES NI) to ensure minimal performance impact and low overhead. Key management is integrated into the security policies and supports the Key Management Interoperability Protocol (KMIP) standards to provide broad support of key managers.
As part of its security portfolio, the firm offers HyTrust KeyControl, which is integrated with the company’s policy-based security management. This enables enterprises to easily manage all encryption keys at scale, including how often keys are rotated and how they are shared securely.
“With the growth of hyperconverged infrastructure and the expectation that enterprises will increasingly have mixed workload environments, it is essential to employ key management as an integral part of securing the infrastructure,” said Eric Chiu, co-founder and president, HyTrust, Inc. “Pivot3’s Intelligence Engine will further simplify security management for enterprises and extend the industry preference for HyTrust KeyControl in a world where data must be secured no matter where it resides.“
“As organizations evolve to address emerging security threats and changing regulations, automation and intelligence become key ingredients in maintaining a secure infrastructure across the edge, core and cloud,” said Tim Stammers, senior analyst, 451 Group. “By adding policy-based security management features to its Intelligence Engine, Pivot3 is simplifying the process of protecting sensitive and mission-critical data and enabling customers to progress toward a software-defined datacenter.“
The company’s policy-based security management will be available in Acuity version 10.6 before the end of the year.
Resource:
Blog: Why Organizations Need Intelligent, Policy-Based Security Management









 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter

