Top 5 High-End AFAs
In-depth analysis of Dell PowerMax 8500, Hitachi Vantara Virtual Storage Platform 5600, Huawei OceanStor Dorado 18000, Infinidat InfiniBox SSA II, NetApp AFF/ASA A900
This is a Press Release edited by StorageNewsletter.com on April 30, 2024 at 2:02 pmThis market report, published on April 18, 2024, was written by Ken Clipperton and just arriving Dave Raffo, analysts at Data Center Intelligence Group LLC (DCIG).
2024-25 DCIG TOP 5 Cyber Secure High-End All Flash Arrays Report Now Available
This report provides guidance on the Top 5 cyber secure high-end AFAs that organizations should consider in their fight vs. ransomware. These high-performance primary storage arrays afford organizations the best options for serving and protecting the data associated with their most critical workloads.
Critical need fo cyber secure high-end arrays
Cyber crimes and data breaches have become an everyday threat for IT professionals. More than 330 publicly disclosed data breaches and cyber attacks occurred in just the 1st 2 months of 2024. These developments highlight the need for organizations, especially those that provide critical infrastructure services, to detect and thwart cyber attacks and ensure cyber resiliency – the ability to continue operations after falling victim to an attack. Many companies with crucial business and customer data depend on high-end storage arrays to provide uninterrupted access to their data. These high-end storage arrays require built-in cyber resilience to keep that data safe and enable quick recovery if data is compromised.
Recent advances in cyber secure storage
The cyber threat landscape calls for a multi-layered approach to securing data infrastruc?ture. The National Institute of Standards and Technology, an agency of the U.S. government, promulgated a cybersecurity framework that provides actionable guidance to help organizations manage, reduce, and communicate cybersecurity risks for systems, networks, and other assets that process data.
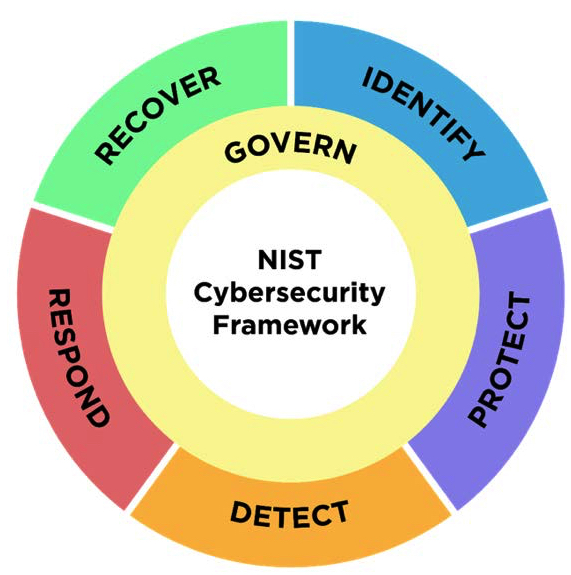
Source: The National Institute of Standards and Technology Cybersecurity Framework 2.0 document
This report looks at how various features and capabilities of high-end all flash arrays help customers address the 6 functions of the NIST Cybersecurity Framework 2.0.
Those functions are:
- Govern – how an organization establishes its cybersecurity strategy and cybersecurity supply chain risk management, along with its policies and oversight of that strategy.
- Identify – how an organization understands assets related to its data, hardware, software, and systems so it can identify, prioritize, and improve risk management strategies and practices.
- Protect – the ability to secure assets through identity management, authentication, access control, awareness and training, data and platform security, and resilient technology infrastructure.
- Detect – an organization’s ability to make timely discovery and analysis of anomalies, indicators of compromise, and other potentially adverse events that may indicate a cybersecurity attack is underway.
- Respond – the ability to contain the impact of a cybersecurity event through incident management, analysis, mitigation, reporting, and communication.
- Recover – the ability to restore assets and operations affected by a cybersecurity attack, return to normal operations, and enable effective communication during a recovery.
Critical features of cyber secure high-end AFAs
It is only a matter of time before a cyberattack successfully breaches any organization’s security defenses. Storage arrays and their providers have a role to play in preventing, mitigating, and recovering from cybersecurity incidents.
Every enterprise storage vendor is addressing customer concerns around data security and cyber resilience, especially the threat of ransomware. Most high-end storage arrays have improved their security posture by implementing multiple technologies, including FIPS 140, T10 PI, and multi-factor authentication.
Common features across high-end AFAs
- Immutable snapshots. All the Top 5 Cyber Secure High-end AFAs support immutable snapshots, which are read-only copies of data that cannot be changed or altered. Because snapshots are a fundamental part of the backup and recovery process, they have become a prime target of cybercriminals. Immutable snapshots have become common in storage systems, as 13 of the 14 arrays DCIG looked at support them. They address the Protect and Recover functions of the NIST Cybersecurity Framework.
- Encryption. All 14 arrays here looked at support encryption, either array-based or through self-encrypted drives. Encryption addresses the Protect function of the NIST Cybersecurity Framework.
- Non-disruptive upgrade features. The Top 5 Cyber Secure High-end AFAs all support non-disruptive upgrades for adding and replacing controllers, upgrading controller code, migrating data, adding storage nodes or shelves, and upgrading firmware for storage media and network ports. Non-disruptive upgrade features address the Protect function of the NIST Cybersecurity Framework, by enabling organizations to keep array software and firmware up-to-date without having to schedule a downtime maintenance window.
In preparing this report, DCIG evaluated over 50 different storage systems based on multiple different features and capabilities. Fourteen of these solutions met DCIG’s criteria for a cyber secure high-end all flash array.
For this report, DCIG examined 14 high-end storage arrays.
The primary cyber security features DCIG looked at included:
- Encryption
- Replication/snapshots
- Security technologies (FIPS 140, hardware root of trust, multi-factor authentication, multiple roles, multiple approvals)
- Security information and event management (SIEM) Integration
- Storage analytics and proactive support
- Vendor management of arrays (STaaS)
Based on these criteria, DCIG awarded the following products a Top 5 award for Cyber Secure High-End AFAs (in alphabetical order):
- Dell PowerMax 8500
- Hitachi Vantara Virtual Storage Platform 5600
- Huawei OceanStor Dorado 18000
- •nfinidat InfiniBox SSA II
- NetApp AFF/ASA A900
Solutions evaluated:
- Dell Technologies PowerMax 2500
- Dell Technologies PowerMax 8500
- Hitachi Vantara Virtual Storage Platform 5600
- HPE Alletra 9000 (9080 4N)
- HPE XP8 Gen2
- Huawei OceanStor Dorado 18000
- Huawei OceanStor Dorado 8000
- IBM DS8900F (DS8980F)
- Infinidat InfiniBox SSA II
- NetApp AFF A900
- NetApp AFF A800
- NetApp ASA A900
- NetApp ASA A800
- Pure Storage FlashArray//XL
All Flash Array Profiles
Dell PowerMax 8500
It is the highest end model of the PowerMax family. PowerMax is one of the most successful high-end storage array platforms in firm’s history. It supports block and file workloads and is 1 of 2 arrays in this report that provide FICON connectivity for mainframe storage.
Some of the features that helped the PowerMax 8500 earn a spot in the 2024-25 Top 5 Cyber Secure High-End AFAs report include:
• Designed for zero trust security environments.
The PowerMax offers:
• Follows secure development lifecycle practices to ensure a shift left approach to security.
• Secure boot.
• Digitally signed software and firmware updates.
• Ransomware anomaly detection, including for both open systems and mainframe hosts.
• Automated compliance monitoring/alerting.
• Granular cyber recovery at scale with up to 65 million policy-driven automated snaps per array, including immutable and secure snaps.
• Applies data encryption through self-encrypting drives (SEDs) to maintain protection when a drive is removed from the system.
• Allows external key managers for data at rest encryption. Supports ignition key with HashiCorp.
• Multi-factor authentication for Unisphere management
• Provides secure access controls and tamper-proof audit logs.
• Detects unauthorized access through secure logs of all events on PowerMax.
• Provides 2-factor authentication to management access using SecureID.
• Role-based access controls.
• Immutable hardware root of trust.
• Remote syslog integration.
DoDIN Approved Product List/STIG hardening. Dell has applied the most stringent cybersecurity requirements as specified by the U.S. government Department of Defense (DoD) and NIST guidelines for reducing the attack surface.
CloudIQ. Dell’s arrays also include CloudIQ (for products with ProSupport or higher contracts) for tracking system health through pattern recognition and analytics. Cloud-IQ’s cyber security features include anomaly detection for unusual access patterns and data reduction rates to detect ransomware or malware, this can also be accessed natively in PowerMax.
Cyber vault. PowerMax cyber vault isolates open systems data from the production network in a secure vault by implementing an SRDF airgap solution with secure snapshots.
Dell’s cyber security features also include:
• Active-active data center replication and (through SRDF software) remote replication
over distances or across sites.
• PowerMax supports periodic and continuous asynchronous replication, synchronous replication across Metro Clusters, and replication across three data centers.
Dell has applied the most stringent cybersecurity requirements as specified by the U.S. Department of Defense (DoD) and NIST guidelines for reducing the attack surface.C
Hitachi Vantara Virtual Storage Platform 5600
It is the high-end of the Hitachi VSP storage product line. It is an all-flash model with NVMe drives and SAS SSDs. Hitachi Vantara guarantees 100% data availability and a 4:1 “sight unseen” data reduction guarantee with de-dupe and compression.
It is one of two Top 5 Cyber Secure High-End AFAs with FICON connectivity for mainframe storage.
Features that earned VSP 5600 a spot in the 2024-25 Top 5 Cyber Secure High-End AFAs report include:
- Hitachi Vantara VSP supports role-based access control, including security auditor and storage administrator roles, security information and event management (SIEM) software, and requires multiple approvals for some actions. Hitachi also sells VSP as a full storage- as-a-service on the customer’s premises or in a Hitachi-managed data center.
- Hitachi Ops Center Suite. This integrated AIOps management software suite provides many VSP security and data protection features, including near-instant ransomware recovery. These features include cloud-based system observability, real-time monitoring and performance tuning of VSP arrays.
- Hitachi Ops Center Protector creates policy-based copy data management workflows for both primary and secondary storage.
It supports:
• Data protection for 2- and 3-data center topologies to ensure business continuity.
• Immutable snapshots and creates new versions of data rather than overwriting when changes occur.
• Anomaly detection.
• Air gap that isolates primary storage and backup systems.
• Array-based encryption for data-at-rest and data-in-flight encryption, including integration with key management systems on VSP arrays.
Other Hitachi data replication software that runs on VSP arrays provide:
• Synchronous replication (TrueCopy).
• Asynchronous replication (Universal Replicator).
• Mainframe cybersecurity.
Hitachi also has mainframe-specific security features:
• Ability to make multiple copies of the whole set of production data without impacting production.
• Isolation from the mainframe storage to avoid unwanted access to data and any modification to production images.
• Possibility to recover data to a different storage than the main one used to create fortress images.
• Immutable production images with no possibility to access, modify or delete the fortress data within the specified retention period.
• Management of the solution outside of the mainframe.
• Capability to protect mainframe storage locally or remotely.
• Critical management actions protected with dual acknowledgment.
Hitachi Vantara VSP supports multiple roles, requires multiple approvals for some actions, integrates with SIEM solutions, and offers mainframe-specific security features.
Huawei OceanStor Dorado 18000
It is an end-to-end NVMe storage system that provides comprehensive data protection and disaster recovery capabilities to ensure data services run securely.
Some of the features that helped the product earn a spot in the 2024-25 Top 5 Cyber Secure High-End AFAs report include:
- Multilayer Ransomware Protection (MRP). It builds a 6-layer in-depth defense system covering network intrusion prevention, network spread prevention, ransomware detection, secure snapshots, backup protection, and isolation zone protection. Huawei claims a ransomware detection rate of 99.9%. OceanStor Dorado can also recover in seconds with secure snapshots, mitigating the impact of ransomware attacks.
- Air gap. OceanStor Dorado can build an isolated replication zone. During non-replication periods, the replication link is disconnected, so backups stay offline and invisible to ransomware.
- Proactive honey file defense. The honey file algorithm intelligently generates honey files based on the types of files in the target file system and monitors these files for malicious behavior so that it can promptly alert users and minimize or prevent data loss.
- Huawei HyperDetect. This anti-ransomware software deployed on Huawei storage systems helps detect ransomware attacks:
• Ransomware file interception intercepts the writes of files infected by known ransomware. When launching attacks, ransomware usually generates encrypted files with special file name extensions. HyperDetect intercepts the writes to files with specific file name extensions, protecting file systems on the array.
• Real-time ransomware detection analyzes file I/O logs and creates a secure snapshot
when ransomware is detected. Many ransomware attacks have similar I/O behavior characteristics. By analyzing file I/O behavior characteristics, HyperDetect quickly filters out abnormal files and performs deep content analysis on the abnormal files to detect if they have been infected. It then creates secure snapshots of attacked files for file systems and sends alerts to the data protection administrator to limit the impact of ransomware.
• Intelligent ransomware detection leverages ML algorithms to compare a new snapshot with a known good secure snapshot, and marks the new snapshot as abnormal if an infection is detected. The system detects known ransomware attack features to identify any attacked file systems.
- Security technologies/certifications. Huawei supports hardware root of trust, multi-factor authentication, and multiple approvals for some actions.
Other cyber security features for OceanStor Dorado AFAs:
• HyperLock – WORM file format
• HyperReplication – synchronous replication across 3 or 4 data centers; asynchronous replication
• Encryption – array-based and self-encrypted drives; encrypts data at rest in the data center and in flight.
• Supports security auditor as well as storage admin role.
• Storage-as-a-service and methods for remote management.
OceanStor Dorado 18000 provides an in-depth, multilayer, intelligent defense system to mitigate the impact of ransomware attacks.
Infinidat InfiniBox SSA II
This AFA is aimed at mission-critical workloads that demand greater performance than its hybrid InfiniBox arrays. It is highly focused on cyber storage resilience and recovery capabilities.
Features that helped the device earn a spot in the 2024-25 Top 5 Cyber Secure High-End AFAs report include:
- InfiniSafe cyber resilience. InfiniSafe is available with all InfiniBox arrays (including hybrid) at no extra cost, bringing cyber resilience to the product family.
InfiniSafe’s features:
• Guaranteed recovery from the InfiniSafe repository in less than 1mn, ensuring enterprises and service providers recover and restore data at near-instantaneous speed after a cyberattack.
• Immutable Snapshots.
• Logical Air Gap, which logically separates immutable data copies from network access either locally, remotely, or both.
• Fenced Forensic Network Environment allows customers to create a private network that is isolated for data validation, testing, and recovery.
• InfiniSafe Cyber Detection (purchasable option) adds deep content scanning.
Infinidat also protects and restores data through:
• Low-RPO Asynchronous replication – Infinidat claims it can deliver a 4s replication interval while using IP infrastructure to reduce complexity. It can asynchronously replicate to a 3rd or 4th site at a distance with an RPO of less than 10s.
• Synchronous replication for zero RPO and less than 400 microseconds of storage latency.
• Active-Active replication allowing simultaneous reads and writes to consistency groups over metro distances. Providing simultaneous access to data on each InfiniBox enables non-disruptive data migration.
• Encryption. Infinidat includes array-based encryption and self-encrypting drives. It encrypts data at rest in the data center and supports local or external key management systems such as Thales CipherTrust.
• Documented backdoor for debugging, emergency access, or to help investigate attacks.
• Storage administrator and storage auditor support.
• Security Information and Event Management (SIEM) software integration.
Other cyber security features:
Infinidat’s InfiniVerse leverages InfiniMetrics telemetry for cloud-based monitoring, AI-based predictive analytics, and AIOps support software. This allows firm’s support engineers to take preventative actions before the customer is impacted.
The firm also provides and is well known for its white glove service for all consumers of their products, assigning a technical advisor, at no additional charge, to each customer for the duration of the support contract. The technical advisor is an experienced storage systems engineer who provides a full spectrum of services, including non-disruptive in-family data migrations, and acts as a customer advisor. Company’s comprehensive service and support include its AIOps-based support software, and 24x7x365 technical support with rapid SLA response times.
InfiniSafe is available with all vendor’s arrays at no extra cost, bringing cyber resilience to the product family.
NetApp AFF/ASA A900
It supports end-to-end NVMe via NVMe/FC to accelerate applications. It supports the full range of connectivity options, including 16/32Gb FC and 10/25/40/100GbE. The AFF 900 supports block and file storage, while the ASA 900 is block-only.
Features that helped AFF A900 earn a spot in the 2024-25 Top 5 Cyber Secure High-End AFAs report include:
- Ontap and BlueXP’s roles in cyber security. Ontap OS that runs on its arrays includes data protection features such as snapshots, replication, mirroring, and cloud backup. Customers can manage ransomware protection, backup and recovery, and DR for all firm’s systems through its BlueXP unified hybrid multi-cloud management control plane. BlueXP backup and recovery protects Ontap data, applications, databases, Kubernetes persistent volumes, and virtual machines on-premises and in the cloud.
- Ransomware guarantee. The company offers this guarantee on new purchases of all its AFF-A
- Series arrays, as well as other Ontap-based storage systems. If it can’t help restore its snapshot data after a ransomware attack, it pledges to compensate the customer. It also triggers rapid recovery by responding to threats in real-time by creating immutable recovery points or blocking user access to storage, applying forensics to identify the source of the threat, and determining which files to recover. NetApp promises to restore petabytes of data in minutes, either locally or remotely.
Other NetApp cyber security features:
• Storage-based anomaly and ML file system monitoring. Sends customer alerts when suspicious activity is found, and automatically triggers the creation of a recovery point.
• Identifies user behavior anomalies to detect compromised user accounts or insider threats.
• Automatic data discovery and classification to identify vulnerable, sensitive, or critical data.
• Multi-admin verification, multi-factor authentication, and role-based access.
• Zero Trust architecture with logical air gap, WORM retention, and detailed logging.
• In-flight and at-rest encryption, both array-based and self-encrypted drives.
• Immutable snapshots.
• SnapLock feature prevents encryption and deletion of data with indestructible and efficient data copies.
• Intelligent forensics to help identify the source of the threat and which files to recover.
• Ontap can block known malicious file extensions before they can be written to disk.












 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter
