Cyber Connection Between Enterprise Storage and NIST Cybersecurity Framework
By Eric Herzog, CMO, Infinidat
This is a Press Release edited by StorageNewsletter.com on February 14, 2024 at 2:01 pm![]() By Eric Herzog, CMO, Infinidat Ltd.
By Eric Herzog, CMO, Infinidat Ltd.
If you’re looking for a cybersecurity model that can be used for enterprise storage, the NIST Cybersecurity Framework (CSF) is a comprehensive approach that is approachable, practical, and solid. It’s not tied to any one vendor, but rather is a rich set of best practices and a set of standards for cost-effective security. Another way of thinking about it is as a far-reaching set of security recommendations that address cyber threats – with one area of focus being storage infrastructure, including data protection and cyber recovery. Cyber threats are on the minds of Fortune 500 CEOs, who have ranked cybersecurity as their #2 concern.
Without a doubt, storage is one of the 3 most fundamental building blocks of any enterprise infrastructure. Therefore, there needs to be security controls that are specific to storage technologies. CISOs, CSOs and CTOs not only have to formulate data center-wide policies for networking and computing, but also for enterprise storage, which can no longer be an after-thought. The NIST framework, which originated out of a need to more easily and effectively manage cyber risk, has proven to be a trustworthy path for information technology leaders and their teams to incorporate storage into an enterprise’s overall cybersecurity strategy for such controls.
While the U.S. government was the first to use it, a variety of industries have, since 2014, adopted the NIST Cybersecurity Framework, which basically emphasizes the use of business drivers to guide an enterprise’s overall cybersecurity strategy. Because storage technologies have become ingrained in many business drivers for modern organizations, this NIST framework has emerged as highly relevant for enterprise storage. Storage admins have a gold mine in this independent framework, whether they realize it or not.
Notably, NIST developed NIST Special Publication (SP) 800-209 (2020) Security Guidelines for storage infrastructure. It smartly examines security threats vs. storage infrastructure and sets forth a set of security recommendations to address these cyber threats against data being accessible, usable, uncorrupted, and available. These threats against the data infrastructure of any given enterprise get more sophisticated, more worrisome, and more serious every day.
NIST SP 800-209 Security Guidelines for storage covers data protection, backup, data reduction, authentication, credentials, and a number of other important aspects of storage. But the most compelling may be the section on malware and ransomware.
Malware is any program that is designed to damage, compromise, or disrupt a system or a device. By breaching security, malware can be used to steal data or control a system. Without the proper level of cyber resilience in place, malware can be installed on a storage management host without the admin or others on the IT team knowing. As a result, this subtle cyberattack causes great harm. It can facilitate credential theft. It can cause corruption or loss of sensitive data. It can also cause a backup system or backup software to be compromised. The list of damage goes on.
Ransomware is a form of malware. It encrypts stored data. The cybercriminal makes the data unusable and then demands a ransom to restore access to the data. To increase the fear of senior management teams within enterprises, the attacker sometimes publishes part of the sensitive data that was collected from – guess where? – the storage system that does not have enough cyber resilience built into it.
Ransomware can scrape passwords from data sets that it has captured. Just imagine the havoc that cybercriminals wreak when they can gain such easy access to the network and then, via the networked connection, access into either primary storage or secondary storage – and all that data. The confidentiality, integrity, and availability of data is on the line. So, the NIST Cybersecurity Framework is dealing with a formidable foe, which is neither traditional nor easy to pin down.
Storage management needs to be secured. Because most of storage is configured and managed through management hosts, the attack surface is broad. Attackers can exploit operating system vulnerabilities when the cyber resilience is weak in the storage infrastructure. Through the storage management, attackers can do everything from corrupt the data to tamper with log and audit data.
When log and audit data is altered nefariously, an attacker can hide their presence in the infrastructure, which is why an attacker can be in an enterprise infrastructure for a year without anyone knowing it yet. Cyber detection built into a storage platform is needed to sniff them out and put into motion the cyber resilient actions to make the infrastructure ‘safe’ again.
But we all have to face reality. With cyberattacks expected to cost more than $9.5 trillion in 2024, it is no wonder that cybersecurity is the #2 concern of Fortune 500 CEOs. Granted, this is a scary thought, but when a cybercriminal gains access to storage management – due to weak levels of cyber resilience – the criminal has near-unlimited potential to harm the entire domain.
A cyber attacker could even impersonate a management host or software through an API, since a storage system is connected with external networked services. The threat is real, and it comes in many forms, shapes, and sizes. This is why security guidelines for storage deployments are so important and cannot be emphasized enough.
NIST Cybersecurity Framework to the rescue
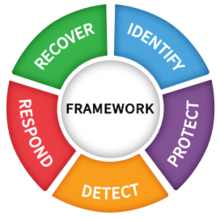
The NIST framework consists of 3 parts: core, implementation tiers, and profile. The core functions involve identifying, detecting, protecting, responding, and recovering. This points to cyber resiliency functions, such as detecting malware or ransomware, as well as rapid recovery of a clean copy of data. It suggests that processes, policies, and technological tools need to be in place to deal with cyberattacks.
The implementation tier structure considers an enterprise’s threat environment, risk assessment, and requirements for compliance. The lowest tier is when a company’s cybersecurity strategies are not formalized, while risk management is, at best, ad hoc. A higher tier is where an enterprise-wide security framework is in place, and it heads into a sophisticated approach with predictive indicators.
Last, but not least, the profile matches the threat environment and business goals with cybersecurity requirements and controls. Understanding your current profile is needed in order to figure out what else needs to be done to boost cyber resilience within your storage infrastructure.
Storage tools and capabilities already exist today to improve the cyber resilience of any enterprise’s storage infrastructure – on-premises or a mix of private cloud and public cloud. The following is a core list of the things to incorporate into your data infrastructure as soon as possible. You probably don’t want to play ‘hide and seek’ with cybercriminals anymore. With these cyber resilience tools, you can neutralize and eliminate the effects of a cyberattack – and I swear this with my hand on the NIST guidelines.
-
Immutable snapshots – You absolutely need to take snapshots of data that cannot be altered in any way. Indeed, you want a capability that delivers secure and unchangeable, point-in-time copies. Taking snapshots or simply relying on backup is not enough. The immutability of the snapshots is vital.
-
Cyber detection – You need to be able to diagnose what data has been compromised and the nature of the compromise. ML algorithms can tell you the type of variant that was used to corrupt the data. You want to be sure to choose a cyber detection tool already built into the storage platform to inspect the content of files and data with full-content-based analytics.
-
Logical/remote air-gapping – It’s important to have a simple way to logically separate the immutable snapshots from network access. You may have to do it locally or remotely, or both.
-
Fenced forensic environment – Isolation is highlighted in the NIST framework. The best practice in storage is a fenced forensic network, a completely private network, which is isolated. Why is this needed? It’s because it’s needed for data testing, validation and, ultimately, recovery.
-
Near-instantaneous recovery from cyberattacks – If you look for the right solution, you can recover a known good copy of clean, validated data within minutes after a cyberattack – regardless of the size of data. You don’t have to pay the ransom when you have all of these cyber resilient storage capabilities protecting your infrastructure. When an enterprise IT team ignores such a best practice, they sadly increase the security risk against their business and handcuff themselves from leveraging a rapid cyber recovery that would otherwise negate the impact of the cyberattack.
Data protection in the storage infrastructure – safeguarding data at rest, data in transit, data in use, data traveling outside the security perimeter – must be comprehensive. The NIST framework gives you the security recommendations, precise guidelines, and best practices to wrap your IT operation with cyber resilience end to end. Reach out to your IT solution provider and/or enterprise storage solution vendor for additional training and knowledge-sharing on how to optimize the adoption of the NIST security guidelines for storage infrastructure.
Equipped with the NIST framework, you don’t need to allow a data breach through storage to define your future. Make storage ‘bullet-proof’ with cyber resilience.












 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter
