Forces Driving Organizations to Implement Data Immutability
New gold standard for data protection
This is a Press Release edited by StorageNewsletter.com on June 22, 2023 at 2:02 pm This article, published on June 15, 2023 , was written by Jerome M. Wendt, president and founder, DCIG, LLC.
This article, published on June 15, 2023 , was written by Jerome M. Wendt, president and founder, DCIG, LLC.
The Forces Driving Organizations to Implement Data Immutability
As recently as only a few years ago most organizations only stored data in an immutable format in rare circumstances. Suddenly, in 2023, organizations get told by analysts, the media, and technology providers that they must store their backup data in an immutable format. What changed and why so rapidly?
On June 15, 2023, Wendt, along with AvTek Solution, Inc.‘s CEO Wayne Hunter will present and answer these questions in a webinar (registration link).
It’s the inevitability of a ransomware attack
Let me provide two insights from this forthcoming webinar as to why organizations increasingly implement data immutability.
First, no existing perimeter cybersecurity defenses will fully protect organizations against ransomware.
One should in no way interpret this statement to demean or devalue the importance or need to implement cybersecurity technologies. These remain an absolute requirement as a first line defense vs. ransomware as prevention is always better than recovery. These defenses should minimally include firewalls and antivirus software with data loss prevention (DLP) software also becoming a necessity.
Yet implementing these cyber defenses no longer guarantees that organizations will not experience an attack. Hackers have already compromised infrastructures of multiple publicly traded companies in 2023 alone who have defenses like these in place. These companies include CommScope, Dole, Western Digital, and Yum Brands.
Unfortunately, these attacks do not represent the ones that should concern organizations. Cyber technology and software providers likely already know how bad actors compromised these corporate infrastructures. As a result, these providers have subsequently implemented the appropriate countermeasures into their solutions.
Rather, sites like Bleepingcomputer contain the latest news on new ransomware variants and attack vectors. In these cases, technology providers may not yet have countermeasures in their solutions for these new variants. Or if they do, organizations may not have yet implemented them or updated their internal processes to counter them.
Second, more than 90% of ransomware attacks begin with phishing emails.
Many organizations use Microsoft 365’s Exchange Online for their corporate email. DCIG counts itself among those organizations. As part of this service, Microsoft implements numerous features that catch and screen out junk and spam emails. Frankly, it probably catches far more of them than I realize or for which I give it credit.
However, as the 2 screen shots of phishing emails below reveal, Microsoft does not catch them all. These 2 phishing emails showed up not in my Junk Email folder nor my “Other Inbox” folder. These appeared in my “Focused Inbox” folder. Further, I get 1 or 2 like this every day.

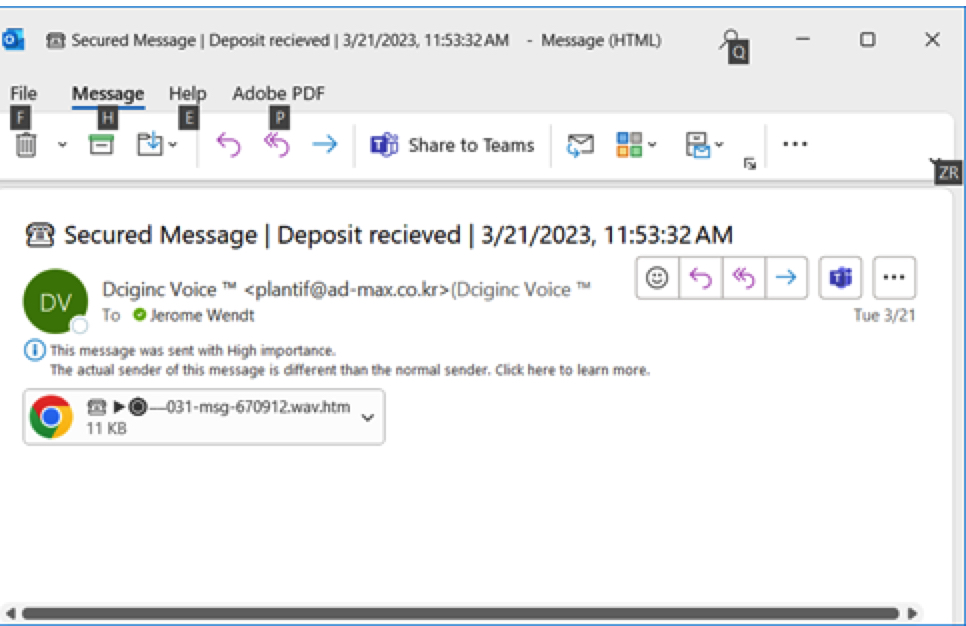
Thankfully, in these 2 cases, I recognized the phishing emails for what they were and quarantined them. However, in any organization, it only takes one person accidentally clicking on an attachment or link to initiate a ransomware attack. Organizations who believe this can never happen are kidding themselves.
Data Immutability Represents Last Line of Defense
These 2 examples highlight why organizations must assume that they will eventually experience a ransomware attack. Further, as ransomware attacks become more sophisticated, it may not launch immediately.
Attacks may sit dormant for days, weeks, even months, silently infiltrating the organization’s infrastructure. Further, some may even compromise the backup solutions organizations have in place.
All these often-hard-to-predict variables make data immutability the new gold standard for data protection. Properly implemented, immutability technology ensures ransomware does not change, delete, or encrypt organizational data.













 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter

