Deep Analysis on Cloud Backup for Ransomware Protection
Overall leaders Arcserve, Cohesity, Commvault, Druva, OpenText, Veeam, and Veritas
This is a Press Release edited by StorageNewsletter.com on May 8, 2023 at 2:02 pm This market report, published on March 30, 2023, was written by Mike Small, distinguished analyst, KuppingerCole Analysts AG.
This market report, published on March 30, 2023, was written by Mike Small, distinguished analyst, KuppingerCole Analysts AG.
Cloud Backup for Ransomware Protection
This report provides an overview of the cloud backup for ransomware protection market and a compass to help you find a solution that best meets your needs. It examines solutions that provide backup, restore, and DR of the data held in today’s hybrid IT services into the cloud. It provides an assessment of the capabilities of these solutions to meet the backup and DR needs of all organizations with a particular focus on ransomware protection.
1 Introduction / Executive Summary
The KuppingerCole Leadership Compass provides an overview of a market segment and the vendors in that segment. It covers the trends that are influencing that market segment, how it is further divided, and the essential capabilities required of solutions. It also provides ratings of how well these solutions meet our expectations.
This Leadership Compass covers solutions that …
Provide backup, restore, and DR of all data held in today’s hybrid IT services into the cloud. It provides an assessment of the capabilities of these solutions to meet the backup and DR needs of organizations with a particular focus on ransomware protection.
There is a mature market with many existing backup and DR solutions that support the protection of data in IT services delivered on-premises by backing up data to physical media. However, the way in which IT services are delivered is changing as organizations move to a hybrid delivery model. This is leading to emerging markets for solutions that protect data in SaaS and IaaS as well as for solutions that use cloud services to secure the backed-up data. There is also a growing market offering enterprise BaaS and DRaaS.
A major threat to BC is ransomware. This is because organizations are now very dependent upon their IT services and the data they contain. Working from home has increased the risks of ransomware because of the lack of data protection for unmanaged end user devices. In addition, cyber adversaries have made ransomware protection more difficult by attacking the backup processes as well as the backed-up data itself.
Most of the existing vendors are adapting their solutions to this hybrid service delivery model, but there is still some way to go, especially around SaaS platforms. In addition, new vendors, including the cloud service providers themselves, now offer solutions to protect data in their cloud and to store backup data from other sources. For SaaS, most vendors now offer solutions for customers to backup the data held in Microsoft Office 365. Some offer solutions that also cover Google Workspace and Salesforce, however, there is a lack of comprehensive coverage for data in other SaaS platforms. This is likely to become more of a problem with the increase in the variety of business solutions delivered as SaaS.
Customers should look for solutions that provide capabilities that align with their business requirements for service continuity. Organizations must identify their business-critical systems and data and use this to define the BC protection needed. This sets the recovery objectives for backup and DR processes and tools.
In general, where an organization is already using an existing solution for on-premises protection, this will be preferred over adding other solutions, providing it meets their evolving business needs. Adding new solutions increases not only costs but also adds to the complexity of use and maintenance. However, in our research we see that some existing solutions on the market do not yet provide comprehensive coverage for the hybrid IT model. Where an existing solution does not meet the business requirements, the organization should consider the new-to-market solutions, if only as a stop gap.
1.1 Highlights
- Data is the most important business asset of the modern organization, and it needs to be protected vs. unauthorized access as well as ransomware and loss.
Today’s e-commerce, financial services, and critical infrastructure demand continuous availability where evens of downtime could lead to severe damage and disruption. - Ransomware is a major threat to BC. Cyber adversaries use various techniques to infiltrate an organization’s IT systems and make changes that prevent the organization from accessing their data and using their IT services.
- Backup and DR tools provide important controls that are needed to recover data and restore services following cyber-attacks. They are an essential part of a complete information lifecycle protection approach.
- Today’s hybrid IT environment creates additional challenges for backup and DR because of its complexity and heterogeneity.
- Traditional backup tools deployed as a combination of software, agents and appliances are complex to use, difficult to manage, hard to secure, and are often compromised as part of a ransomware attack.
- Cloud services create new backup and DR challenges. Organizations can misunderstand the shared responsibility model and believe data protection is the sole responsibility of the cloud provider. In addition, big data and massive data lakes held in cloud services create additional data resilience challenges.
Cloud services also provide a way to overcome these challenges. Software as a Service removes many of the management and security tasks from the end user. They provide highly resilient and immutable storage capabilities to protect backup data. They also enable highly scalable backup solutions using modern architectures. - The overall leaders (in alphabetical order) are Arcserve, Cohesity, Commvault, Druva, OpenText (Micro Focus), Veeam and Veritas.
- The product leaders (in alphabetical order) are 11.11 Systems, Arcserve, Cobalt Iron, Cohesity, Commvault, Druva, OpenText (Micro Focus), Veeam, and Veritas.
The innovation leaders (in alphabetical order) are Clumio, Cobalt Iron, Cohesity, Commvault, Druva, HYCU, and Veeam. - The market leaders (in alphabetical order) are Arcserve, Commvault, OpenText (Micro Focus), Veeam, and Veritas.
- The market disrupters (in alphabetical order) are Cobalt Iron, Clumio, Druva, and HYCU. These innovators are setting new standards for cloud backup solutions in this market by providing easy to use, lightweight and highly scalable SaaS based solutions.
1.2 Market segment
Data is the most important business asset of the modern organization, and it needs to be protected vs. unauthorized access as well as ransomware and loss. Organizations are using cloud services to improve flexibility, to create new products and to reduce costs through digital transformation. This is creating a tension between the benefits that cloud services provide and the risks that using a 3rd party, often in another country, to process data create.
It is important to remember that information protection must cover the whole of the information lifecycle and requires a wide range of different types of controls. Backup and DR tools provide some but not all of the controls that are needed. The KuppingerCole Information Protection Life Cycle (IPLC) and Framework[^1] describes the phases, methods, and controls associated with the protection of information. Though other IT and cybersecurity frameworks exist, none specifically focus on the protection of information across its use life. The IPLC documents 3 stages in the life of information and 6 categories of controls which can be applied to secure information.
Figure 1: The Role of Backup and DR tools in the Information Protection Lifecyle
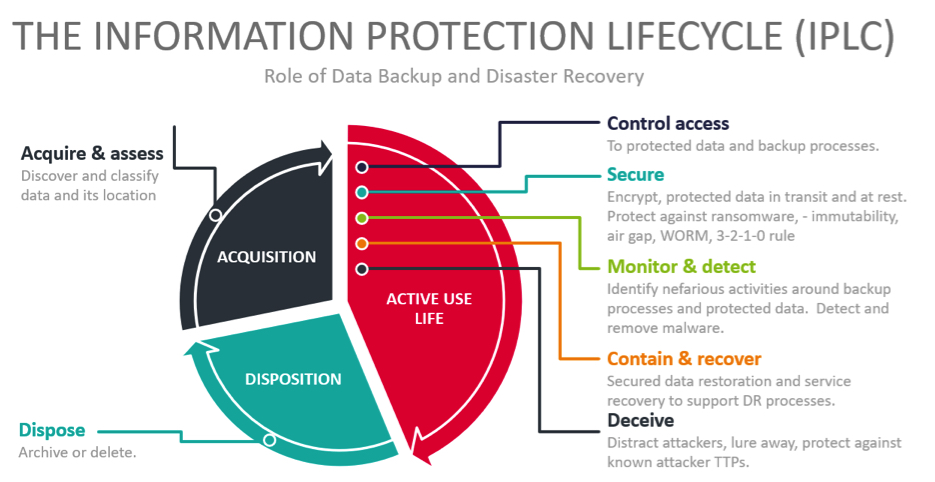
The term “Cloud Backup” stands for a comprehensive set of software, and services that protect business critical data held by organizations on-premises and in cloud services vs. ransomware and other risks by taking copies of that data and providing capabilities to restore it and the services.
Ensuring the continuity of IT services is an essential part of the security triad of confidentiality, integrity, and availability. This requires, amongst other things, ensuring that data related to these services are backed up in a way that allows them to be restored following unwanted events such as ransomware attacks as well as physical and logical damage to the storage devices or to the IT installation.
Today, ransomware is a major threat to BC. Cyber adversaries use various techniques to infiltrate an organization’s IT systems and make changes that prevent the organization from accessing their data and using their IT services. The organization then faces the choice of either paying a ransom to regain access or restoring the affected services and data from backups. Cyber adversaries attempt to make restoration and recovery more difficult by attacking the backup processes as well as the backed-up data.
Making backup copies of data is necessary but not sufficient, and organizations need to be able to use the backed-up data to recover their services. This can be a complex process and the backup processes must take account of the need to recover. Cloud backup solutions must include the capabilities and services needed to recover data and rapidly restore services.
Two parameters specify the objectives for BC supported by cloud backup solutions. RPO – this defines how frequently data must be backed up. RTO – this defines how long it should take to recover from an incident.
The time criticality of digitized business services increases the need for an always on IT service architecture. Today’s e-commerce, financial services, and critical infrastructure demand continuous availability where evens of downtime could lead to severe damage and disruption. An always on architecture depends upon replicated service components with automated failover to ensure BC when individual elements fail.
All organizations need to consider the risks related to the availability of their business data and respond appropriately to mitigate these risks. This means investing in backup products and DR services and immutable storage solutions to ensure data resilience. It is vital that the chosen approach is adequate for the modern digitally transformed hybrid IT environment.
1.3 Delivery models
When IT services were delivered exclusively on-premises, backup solutions made copies of the data to physical storage media (typically tape and disk) which were then held in separate locations with additional safeguards vs. fire and theft. The physical transfer of these media added delays and additional risks into the backup and recovery processes. However, IT services are now delivered through a hybrid model which introduces new challenges and provides new opportunities.
Figure 2: Evolution of Backup and DR
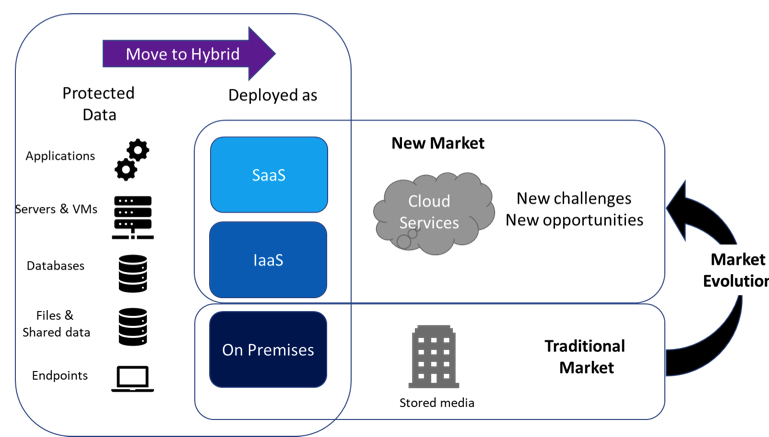
Most organizations now have a hybrid IT environment with IT services delivered in multiple ways, some remaining on-premises and others delivered as cloud services. This adds to the complexity of backup, restoration, and recovery processes.
The cloud also provides an alternative location for backup data since major cloud services are delivered from highly secured datacenters in multiple geographic locations. Organizations can therefore use the cloud to store their backup data with a high degree of resilience and this also reduces the delays and risks previously involved in the physical transfer of media to secure locations.
There is a temptation to believe that the use of a cloud service removes the need for the customer to consider the resilience of their data. The responsibility for data held in cloud services is shared between the tenant and the service provider and there are many situations where the tenant is responsible for the resilience of their data. In addition, where multiple data protection solutions are used this increases the management burden. To avoid this, organizations should look to implement a single solution that covers all the different use cases.
The cloud also provides an opportunity to simplify the delivery of backup and DR as SaaS. This eliminates the many tasks involved in managing, administering, and securing the backup services, software, and appliances. Modern architectures such as containerization and serverless also provide increased scalability and flexibility in the solutions.
These processes and tools can be complex, and, because of this, solutions should provide organizations with options to choose the level of managed service that is appropriate for their needs. The services on the market range from a full “white glove” managed service covering everything to self-service DRaaS providing only the tools needed.
Deployment models for cloud backup and DR include:
- As a physical appliance – that can be deployed on premises or in a data center.
- As a virtual appliance that can be deployed on-premises or in a cloud service.
- As-a-service from multi-tenant public cloud services where updates and patches are deployed by the service provider across all tenants with full automation. This is a growing market because of ease of adoption combined with the scalability offered by public clouds.
- As single-tenant services that can operate in various deployment models, i.e., in private or public clouds or even on-premises, where they are operated in a full as-a-service model, i.e., services where updates, patches, etc. are deployed by the service provider across all tenants with full automation.
1.4 Required capabilities
This Leadership Compass analyses the main attributes and functions of cloud backup for ransomware protection solutions.
These capabilities should include:
- Basic capabilities – including backup, data replication, data recovery, system restoration, and CDP. The storage systems and data types protected by the solution. The cloud services in which user organizations can hold their protected data. How the solution supports realistic RPO and RTO targets. How the solution protects the backup data vs. deterioration. The way in which the solution minimizes the size of backed up data – for example through de-dupe that removes multiple copies within the protected data.
- Extended capabilities – including support for near zero RTO and continuous replication for zero RPO. Support to automatically migrate data and applications between different environments to facilitate failover and failback. Support to non-destructively test data restoration and service recovery as well as capabilities for data archive / long-term retention.
- Deployment – how quickly, easily, and repeatably can the solution be deployed. The deployment options that the solution offers. Whether the solution requires agents installed on the protected systems.
- Administration – how easy it is to administer the solution. For example, GUI/Wizard provided for ease of use, CLI/APIs for automation. Capabilities to securely delegate administration to line-of-business managers and application owners.
- Data Security – the capabilities to protect backed-up data vs. theft, unauthorized access, and corruption. How the solution protects data in transit (for example, support for the latest versions of TLS 1.3). How the solution protects data at rest – the type of encryption the solution supports and how the solution secures the encryption keys. How the customer can manage the encryption keys.
- Cyber Security – How the solution is secured. Controls over administrative access including multi-factor authentication and granular authorization methods such as role-based and policy-based access control. Support for secure delegation of administration. How API and CLI access is secured vs. unauthorized access.
- Ransomware Protection – additional capabilities to protect vs. and recover from ransomware. For example, detection and control over abnormal administrative activities, additional protection for backed-up data (air gap, object lock, write once). Protection vs. malware, ransomware, and other forms of cyber-attack including proactive scanning of backups. Scanning of backed-up data to find and remove malware.
- DR – how the solution supports data recovery and service restoration – for example: run books, workflows, and process automation. Full stack restoration capabilities – (i.e., the coordinated restoration of multiple service components). DRaaS capabilities and guaranteed SLAs for RPO/RTO.
- On-premises Protection – out-of-the-box protection for storage and data types. Volumes, databases, file systems, file shares, OS images, hypervisor images, email servers and other applications. The out-of-the-box capabilities to protect DBMS including MS SQL, MySQL, Oracle, SAP HANA, others. Automated capabilities to discover and snapshot environments and applications.
- IaaS Services Protection – out-of-the-box coverage of the IaaS services. For example, major services such as AWS, Google, IBM Cloud, and Microsoft Azure. The capabilities to protect cloud DBMS including MS SQL, MySQL, Oracle, and SAP HANA. Capabilities to protect data held in the types of storage found in IaaS services e.g., files, file systems, object storage, etc. Capabilities to snapshot and restore the native cloud service VMs. Support for replicating applications to other regions for added DR readiness.
- SaaS Protection – the SaaS services covered out-of-the-box. These should include major services such as Microsoft Office 365, Google Workspace, Salesforce and cover the types of data that are found in these services.
- Regulatory Compliance – the capabilities provided by the solution for the customer to use it in a way that complies with laws and regulations across the world. These include customer control over the geographic jurisdiction in which the protected data is held as well as over encryption and the encryption keys. Capabilities to identify and classify sensitive data within the protected data and to add extra protection for this data. Audit capabilities provided as well as independent certifications for compliance with laws and regulations across the world. Up to date certification/attestation vs. relevant cloud hosting and security standards such as CSA Star, ISO 27001, SOC 2 Type 2, etc. Compliance with export control regulations where applicable.
2 Leadership
Selecting a vendor of a product or service must not only be based on the information provided in a KuppingerCole Leadership Compass. It provides a comparison based on standardized criteria and can help identify vendors that shall be further evaluated. However, a thorough selection includes a subsequent detailed analysis and a PoC of pilot phase, based on the specific criteria of the customer.
Based on our rating, we created the various leadership ratings.
The overall leadership rating provides a combined view of the ratings for:
- Product leadership
- Innovation leadership
- Market leadership
The overall leadership rating provides a consolidated view of all-around functionality, innovation, market presence, and financial position. However, these vendors may differ from each other in terms of product features, platform support, and integrations. Therefore, we strongly recommend looking at all the leadership categories as well as each entry in chapter 5 to get a comprehensive understanding of the players in this market and what use-cases they support best.
2.1 Overall leadership
The Overall leadership chart is linear, with followers appearing on the left side, challengers in the centre, and leaders on the right.
Figure 3: Overall Leadership in Leadership Compass Cloud Backup for Ransomware Protection
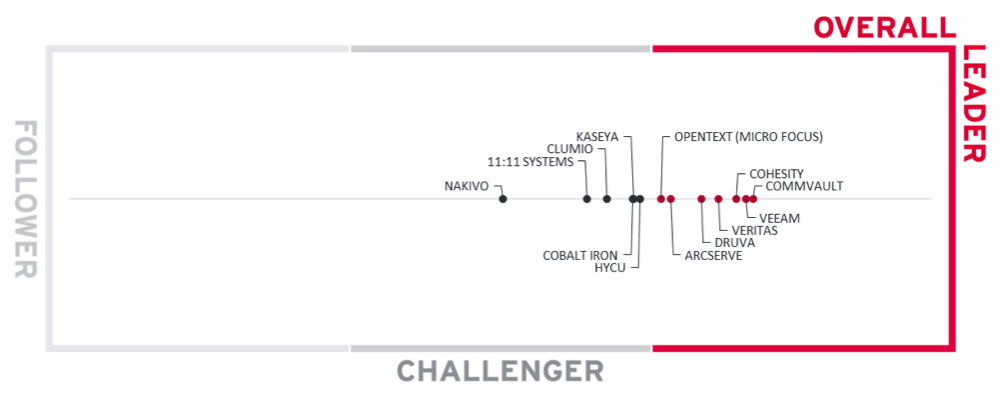
The overall leaders are (in alphabetical order):
- Arcserve
- Cohesity
- Commvault
- Druva
- OpenText (Micro Focus)
- Veeam
- Veritas
The overall challengers are (in alphabetical order): 11.11 Systems, Cobalt Iron, Clumio, HYCU, Kaseya, and Nakivo.
2.2 Product leadership
Product leadership is the first specific category examined below. This view is mainly based on the presence and completeness of required features as defined in the required capabilities section above. The vertical axis shows the product strength plotted vs. the combined/overall strength on the horizontal axis. The product leadership chart is rectangular and divided into thirds. Product leaders occupy the top section. Challengers are in the centre. Followers are in the lower section.
Figure 4: Product Leadership in tLeadership Compass Cloud Backup for Ransomware Protection
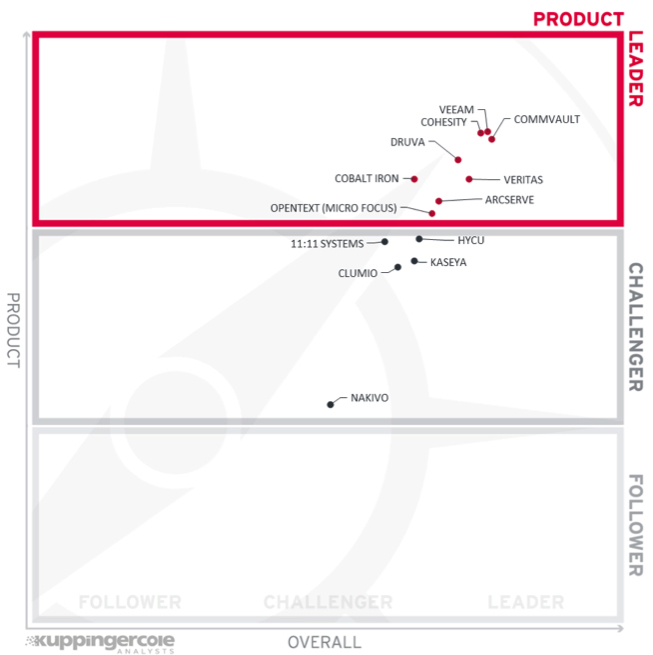
All vendors in the product leadership deliver capabilities across the depth and breadth of the cloud backup for ransomware protection capability spectrum evaluated for the vendors in this Leadership Compass. However, we can also observe some much smaller vendors among the leaders, which nevertheless are able to offer their solutions with comprehensive capabilities, flexible deployment options and lower operational complexity than the market giants.
Product Leaders (in alphabetical order):
- Arcserve
- Cobalt Iron
- Cohesity
- Commvault
- Druva
- OpenText (Micro Focus)
- Veeam
- Veritas
The product challengers are (in alphabetical order): 11:11 Systems, Clumio, HYCU, Kaseya, and Nakivo. All these vendors have good offerings but lack certain advanced capabilities that we expect to see, either in the depth or breadth of functionalities seen in the Leadership segment offerings. There are no followers in the product leadership rating.
2.3 Innovation leadership
Next, we examine innovation in the marketplace. Innovation is, from our perspective, a key capability in all IT market segments. Customers require innovation to meet evolving and even emerging business requirements. Innovation is not about delivering a constant flow of new releases. Rather, innovative companies take a customer-oriented upgrade approach, delivering customer-requested and other cutting-edge features, while maintaining compatibility with previous versions.
This view is mainly based on the evaluation of innovative features, services, and/or technical approaches as defined in the required capabilities section. The vertical axis shows the degree of innovation plotted vs. the combined/overall strength on the horizontal axis. The innovation leadership chart is rectangular and divided into thirds. Innovation leaders occupy the top section. Challengers are in the centre. Followers are in the lower section.
Figure 5: Innovation Leadership in Leadership Compass Cloud Backup for Ransomware Protection
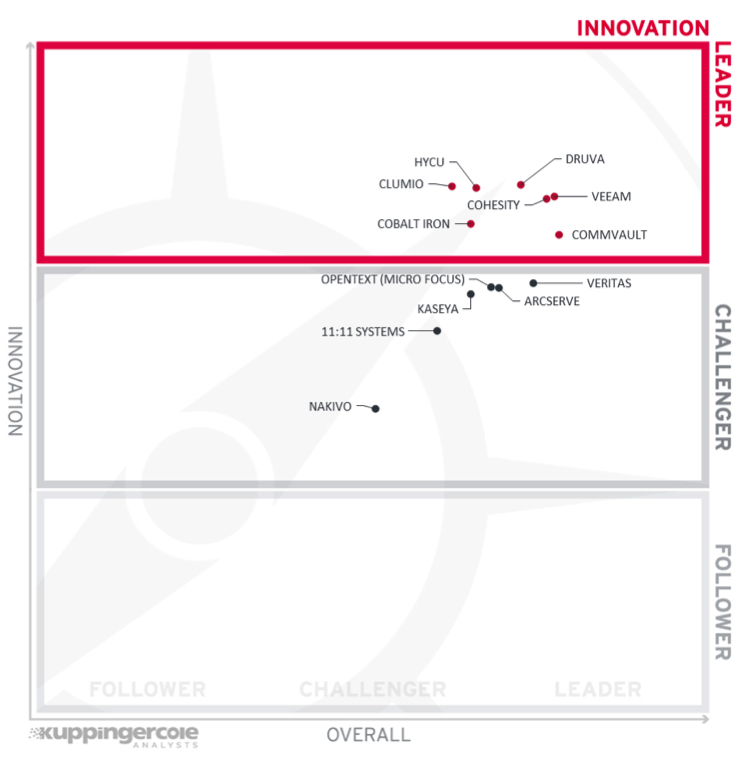
Innovation leaders are those vendors that are delivering cutting edge products, not only in response to customers’ requests but also because they are driving the technical changes in the market by anticipating what will be needed in the months and years ahead. There is a correlation between the overall, product, and innovation leaders, which demonstrates that leadership requires feature-rich products that are looking over the horizon to bring advancements to help their customers. There are also some newer vendors that we have identified in the leadership category because of their vision and how this is implemented in their solutions.
Innovation leaders (in alphabetical order):
- Clumio
- Cobalt Iron
- Cohesity
- Commvault
- Druva
- HYCU
- Veeam
The innovation challengers are (in alphabetical order): 11.11 Systems, Arcserve, Kaseya, Nakivo, Inc., OpenText (Micro Focus), and Veritas. These companies also have some specific innovations that make their offerings attractive to their customers but lack the breadth of innovation that other vendors demonstrate.
2.4 Market leadership
Lastly, we analyze market leadership. This is an amalgamation of the number of customers, in this market sector, their geographic distribution, the size of deployments and services, the size and geographic distribution of the partner ecosystem, and financial health of the participating companies. Market leadership, from our point of view, requires global reach.
In this chart, the vertical axis shows the market strength plotted vs. the combined/overall strength on the horizontal axis. The market leadership chart is rectangular and divided into thirds. Market leaders occupy the top section. Challengers are in the centre. Followers are in the lower section.
Figure 6: Market Leadership in Leadership Compass Cloud Backup for Ransomware Protection
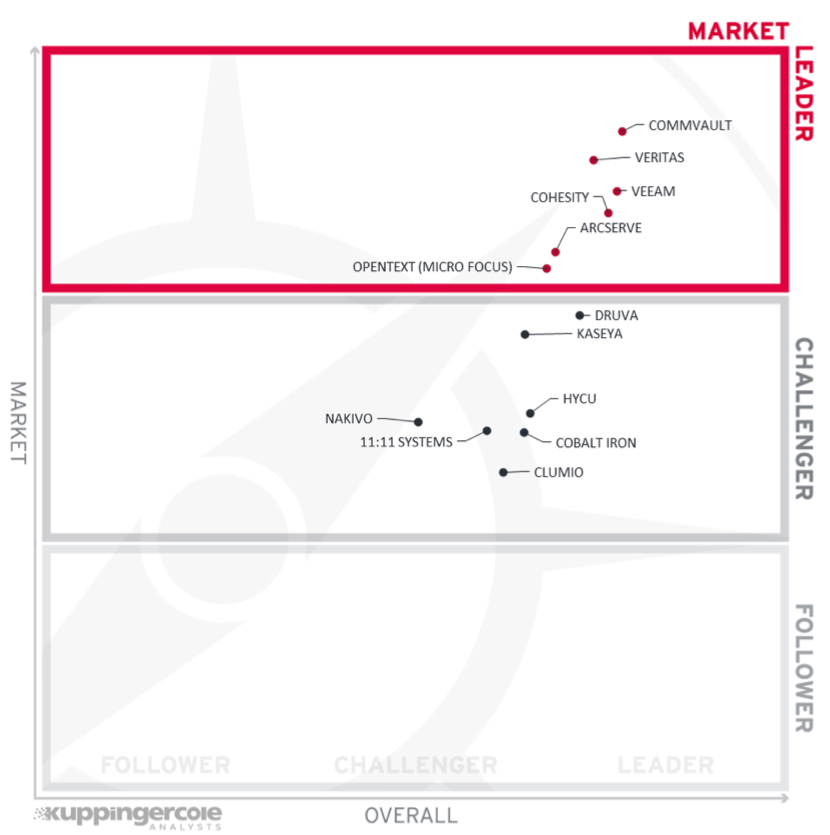
Market leadership is a combined measure of customers, managed users, partners, the geographic distribution of customers, support, and partners, and overall financial position. These vendors have financial strength, geographic distribution of customers and partner, and extensive ecosystems of system integrators.
Market leaders (in alphabetical order):
- Arcserve
- Cohesity
- Commvault
- OpenText (Micro Focus)
- Veeam
- Veritas
The market challengers are (in alphabetical order): 11.11 Systems, Clumio, Cobalt Iron, Druva, HYCU, Kaseya, and Nakivo. Some of these vendors are relatively young, lack a comprehensive global presence, focus mainly on their home markets, or are still in their growth phase. The large vendors that are challengers, while having a large overall market, tend to have a limited presence in this market.
3 Correlated view
While the leadership charts identify leading vendors in certain categories, many customers are looking not only for a product leader, but for a vendor that is delivering a solution that is both feature-rich and continuously improved, which would be indicated by a strong position in both the product leadership ranking and the Innovation Leadership ranking. Therefore, we provide the following analysis that correlates various leadership categories and deliver additional levels of information and insight.
The first of these correlated views contrasts product leadership and market leadership.
3.1 Market/product matrix
The first of these correlated views contrasts product leadership and market leadership.
The vertical axis represents the market position plotted vs. product strength rating on the horizontal axis.
Figure 7 The Market/Product Matrix for Leadership Compass Cloud Backup for Ransomware Protection
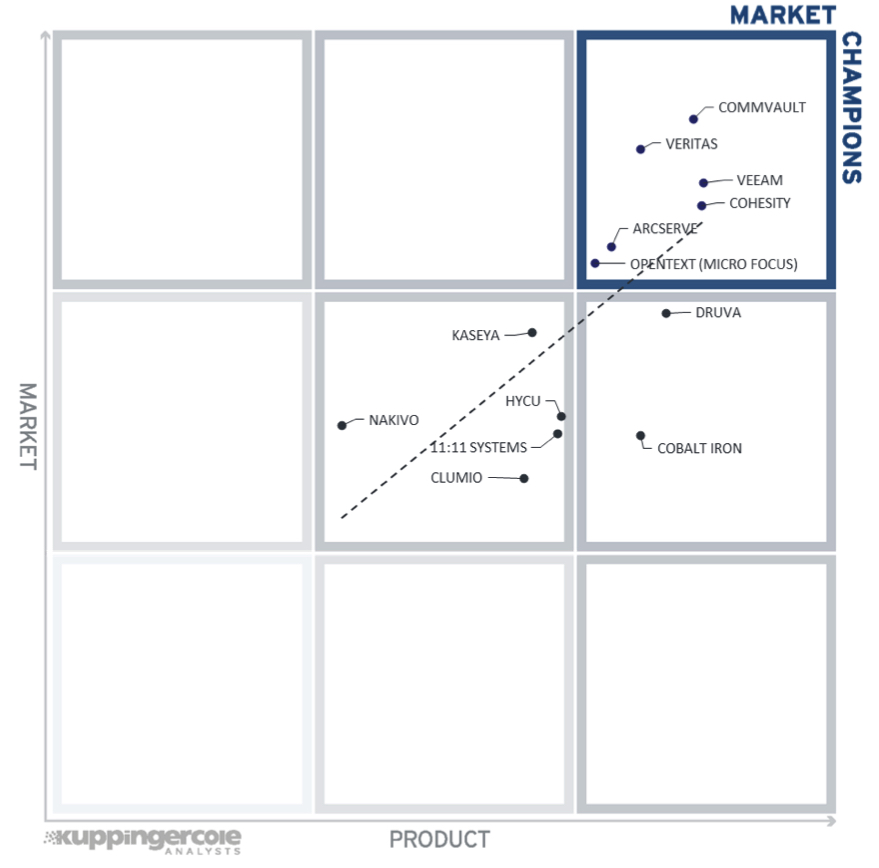
This comparison shows which vendors are better positioned in our Product Leadership analysis than their position in the market leadership analysis. Vendors above the line are somewhat “overperforming” in the market. It comes as no surprise that these are often very large vendors, while vendors below the line may more often be innovative but focused on specific regions as an example.
In the upper right segment, we find “Market Champions”. Given that the backup market is mature, we see Cohesity, Commvault, Veritas, OpenText (Micro Focus), Veeam, and Arcserve as market champions positioned in the top right-hand box.
Market disrupters – In the middle right-hand box, we see 2 vendors that deliver strong product capabilities for cloud backup for ransomware protection but are not yet considered market champions. Cobalt Iron and Druva have a strong potential to disrupt the market and improve their market position due to the strong product capabilities they are already delivering.
In the middle of the chart, we see the vendors that provide good but not capabilities and therefore are not market leaders. These vendors include 11:11 Systems, Clumio, HYCU, Kaseya, and Nakivo. Clumio has a visionary approach to the emerging market for big data, others focus on the needs of specific markets.
3.2 Product/innovation matrix
This view shows how product leadership and innovation leadership are correlated. It is not surprising that there is a pretty good correlation between the two views with a few exceptions. The distribution and correlation are tightly constrained to the line, with a significant number of established vendors plus some smaller vendors.
The vertical axis represents the product strength rating plotted vs. innovation on the horizontal axis.
Figure 8: Product/Innovation Matrix for Leadership Compass Cloud Backup for Ransomware Protection
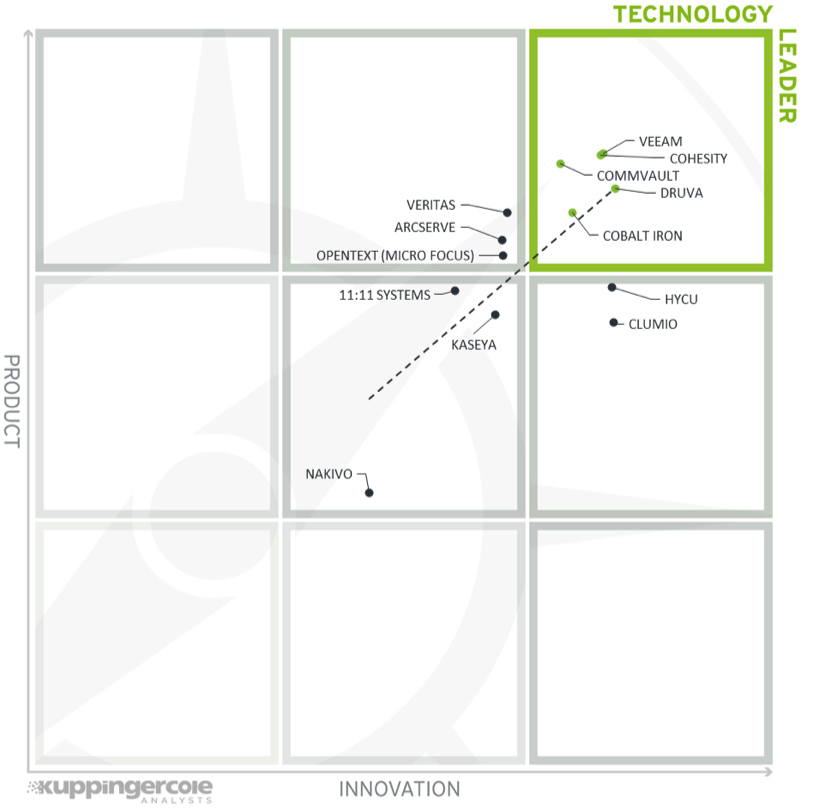
Vendors below the line are more innovative, vendors above the line are, compared to the current Product Leadership positioning, less innovative.
Here, we see a good correlation between the product and innovation rating. Many vendors placed close to the dotted line, indicating a healthy mix of product and innovation leadership in the market. Looking at the technology Leaders segment, we find most leading vendors scattered throughout the box in the upper right corner. The leading vendors are (in alphabetical order) Cobalt Iron, Cohesity, Commvault, Druva, and Veeam.
Cobalt Iron, Cohesity and Druva are positioned closest to the line indicating a good balance of product features and innovation. While all the vendors in this box take different approaches to delivering a cloud backup platform, all perform well in both the current product offering and the level of innovation they demonstrate.
Four vendors appear in the top middle box with excellent products but less innovation than the leaders, these are Arcserve, OpenText (Micro Focus), and Veritas.
In the middle right-hand box, there are 2 vendors with a high degree of innovation which will enhance their product offerings in the future. These are Clumio and HYCU.
Three vendors appear in the middle box, showing both good innovation and product capabilities. However, they remain at a challenger level in both product and innovation ratings. These vendors include (in alphabetical order) 11:11 Systems, Kaseya, and Nakivo. They have a strong potential to further increase their position in the cloud backup for ransomware protection market.
3.3 Innovation/market matrix
The 3rd matrix shows how innovation leadership and market leadership are related. Some vendors might perform well in the market without being innovation leaders. This might impose a risk for their future position in the market, depending on how they improve their innovation leadership position. On the other hand, vendors which are highly innovative have a good chance for improving their market position. However, there is always a possibility that they might also fail, especially in the case of smaller vendors.
Figure 9: Innovation/Market Matrix for Leadership Compass Cloud Backup for Ransomware protection
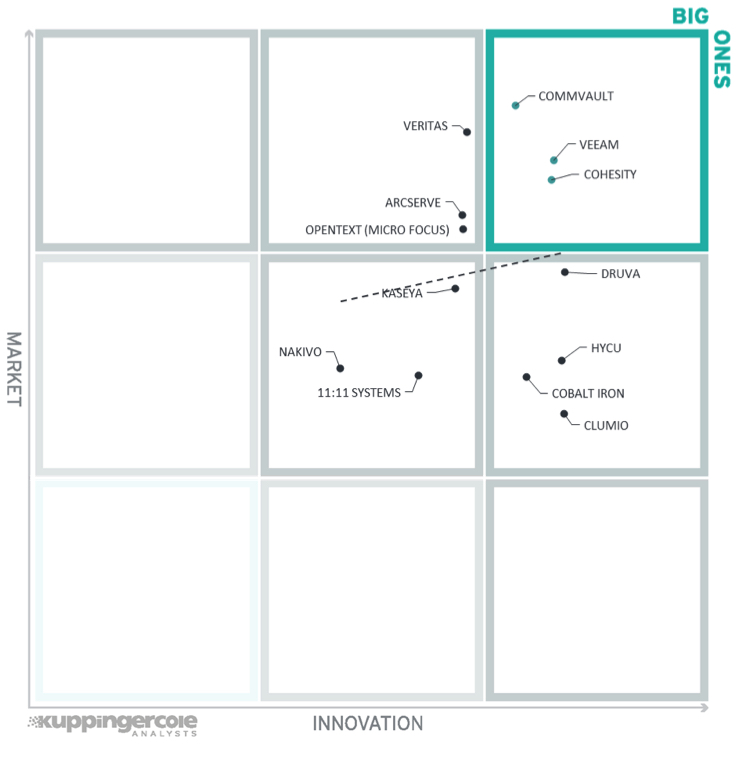
The vertical axis represents the market position rating plotted vs. innovation in this market on the horizontal axis. Note that some vendors may have a different rating for innovation in different markets.
Vendors above the line are performing well in the market as well as showing innovation leadership; while vendors below the line show an ability to innovate though having less market share, and thus the biggest potential for improving their market position.
In the upper right-hand corner box, we find the “Big Ones” in the cloud backup market. We see (in alphabetical order) Cohesity, Commvault, and Veeam. These companies are being rewarded by the market for the level of innovation they provide in their products and services.
In the top middle box, there are three vendors each with a strong market presence and good innovation. These are (in alphabetical order) Arcserve, OpenText (Micro Focus), and Veritas.
Market disruptors – Several vendors appear in the middle right box showing good level of innovation but with less market presence than the vendors in the “Big Ones” category. These include (in alphabetical order) Cobalt Iron, Clumio, Druva, and HYCU. These innovators are setting new standards for cloud backup solutions in this market by providing easy to use, lightweight and highly scalable SaaS based solutions. These vendors and their solutions have the potential to change the market landscape.
The segment in the middle of the chart contains the vendors which are challengers in both innovation and market presence. These are (in alphabetical order) 11:11 Systems, Kaseya, and Nakivo.
4 Products and vendors at a glance
This section provides an overview of the vendors’ various products we have analyzed within this KuppingerCole Leadership Compass on cloud backup for ransomware protection. Aside from the rating overview, we provide additional comparisons that put product leadership, innovation leadership, and market leadership in relation to each other. These allow identifying, for instance, highly innovative but specialized vendors or local players that provide strong product features but do not have a global presence and large customer base yet.
Based on our evaluation, a comparative overview of the ratings of all the products covered in this document is shown in Table 1. Since some vendors may have multiple products, these are listed according to the vendor’s name.
Table 1: Comparative overview of atings for product capabilities
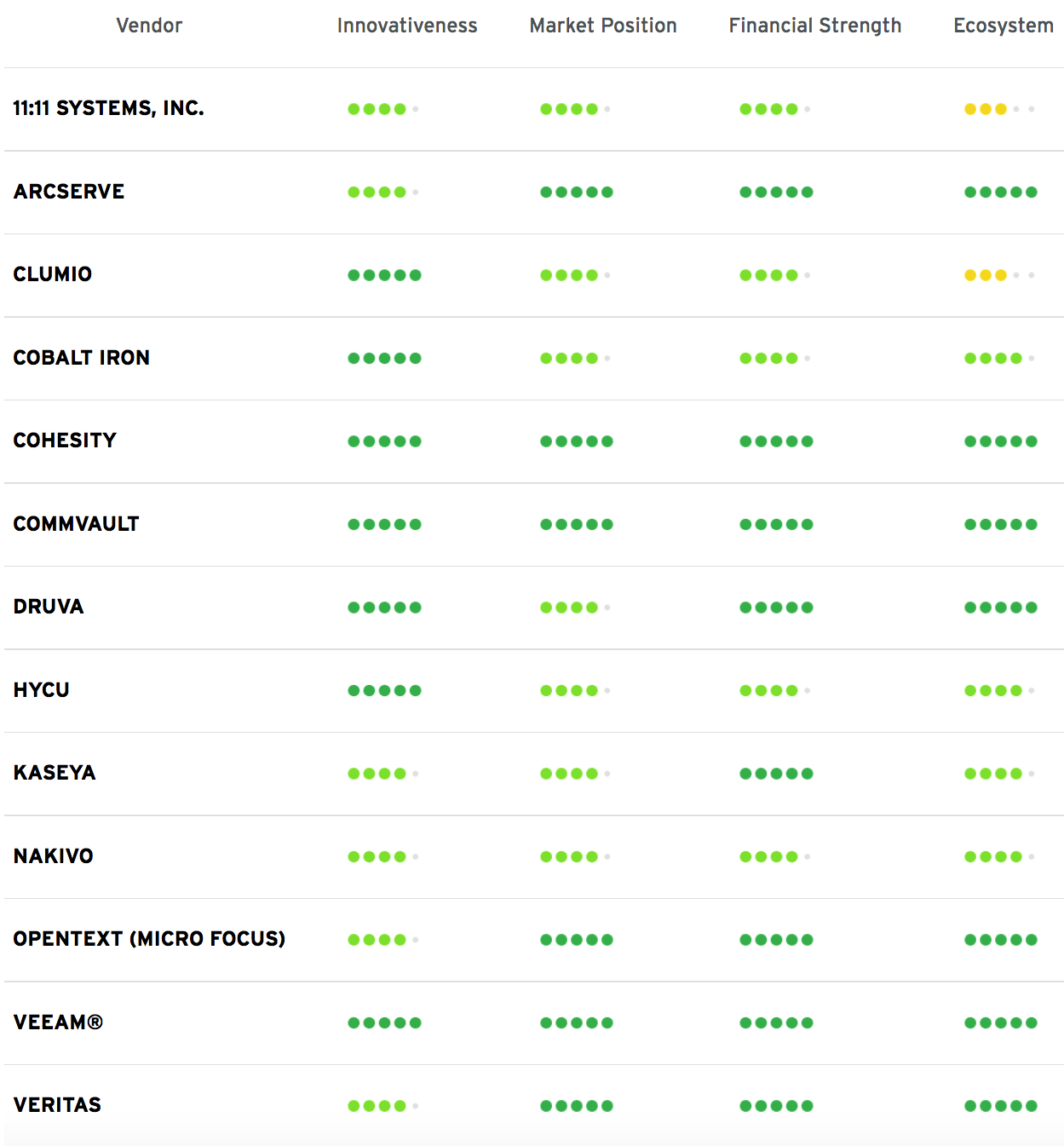
In addition, we provide in Table 2 an overview which also contains 4 additional ratings for the vendor, going beyond the product view provided in the previous section. While the rating for financial strength applies to the vendor, the other ratings apply to the product.
5 Product/vendor evaluation
This section contains a quick rating for every product/service we’ve included in this KuppingerCole Leadership Compass document. For many of the products there are additional KuppingerCole product reports and executive views available, providing more detailed information.
Spider graphs
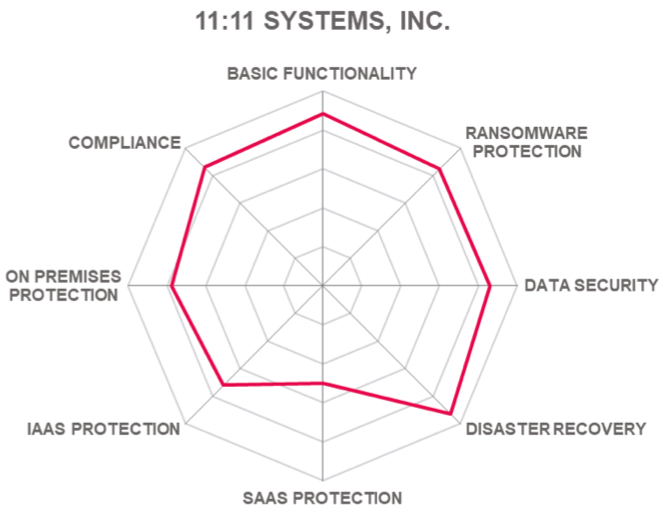
In addition to the ratings for our standard categories such as product leadership and innovation leadership, we add a spider chart for every vendor we rate, looking at specific capabilities for the market segment researched in the respective leadership Compass.
For this leadership compass, we look at the following 8 categories:
- Basic functionality – this category measures the basic backup and DR capabilities provided by the solution. These include backup, data replication, data recovery, system restoration, and CDP. The range of storage systems and data types protected by the solution. The range of cloud services in which user organizations can hold their protected data. How well the solution supports realistic RPO and RTO targets. How well the solution protects the backup data vs. deterioration. How well the solution minimizes the size of backed up data.
- Ransomware protection – this category measures the additional capabilities the solution provides to protect vs. and to recover from ransomware. For example, detection and control over abnormal administrative activities, additional protection for backed-up data (air gap, object lock, write once). Protection vs. malware, ransomware, and other forms of cyber-attack including proactive scanning of backups Scanning of backed-up data to find and remove malware.
- Data security – this category measures the capabilities the solution provides to protect backed-up data vs. theft, unauthorized access, and corruption. It includes the capabilities to protect data in transit (for example, support for the latest versions of TLS 1.3) and to protect data at rest (for example, the type of encryption the solution supports and how the solution secures the encryption keys.)
- DR – this category measures the capabilities the solution provides to recover data and to restore service, for example, run books, workflows, and process automation. It includes the capabilities provided for restoration of the full-service stack (i.e., the coordinated restoration of multiple service components). It also considers the capabilities provided for DRaaS and the guaranteed SLAs for RPO/RTO.
- SaaS protection – this category measures the capabilities the solution provides to protect data held in SaaS. It considers the range of services covered out-of-the-box. These include major services such as Microsoft Office 365, Google Workspace, Salesforce, and the types of data that are found in these services.
- IaaS protection – this category measures the capabilities the solution provides out-of-the-box for IaaS services. These include the major IaaS services such as AWS, Google, IBM Cloud, and Microsoft Azure. It considers the capabilities provided to protect cloud DBMS including MS SQL, MySQL, Oracle, and SAP HANA as well as data held in the types of storage found in these IaaS services e.g., files, file systems, object storage, etc. It also includes the capabilities provided to snapshot and restore native cloud service VMs as well as support for replicating applications to other cloud regions.
- On-premises protection – this category measures the capabilities the solution provides to protect services and data on-premises and at the edge. It covers the types of storage and applications the solution supports including volumes, databases, file systems, file shares, OS Images, and hypervisor images. Applications and databases include email servers and business applications; DBMS include MS SQL, MySQL, Oracle, SAP HANA, and others. It considers the capabilities provided by the solution to automatically discover and protect these environments and applications.
- Compliance – this category measures the capabilities the solution provides for the customer to use it in a way that complies with laws and regulations across the world. These capabilities include the control the customer has over the geographic jurisdiction in which the protected data is held as well as over encryption and the encryption keys. It looks at the capabilities it provides to identify and classify sensitive data within the protected data and to add extra protection for this data. It considers the range of independent certifications for the solution covering compliance with laws and regulations across the world. These include up to date certification/attestation vs. relevant cloud hosting and security standards such as CSA Star, ISO 27001, SOC 2 Type 2, etc. It also considers compliance with export control regulations where applicable.
5.1 11:11 Systems, Inc. – Backup and DRaaS
It is a privately held company with HQs in Fairfield, NJ. It has offices across USA, in the UK and in Australia. It is a managed infrastructure solutions provider that addresses the cloud, connectivity, and security challenges of businesses. In January 2022, it announced the completion of the acquisition of iland, a global cloud service provider hosting for IaaS, DRaaS, and BaaS. In November 2022, it announced the completion of the acquisition of SunGard Availability Services’ Recovery Business and Cloud Managed Services Business.
Its data protection and DR services are based on products from partners using the 11:11 Cloud Platform. This is based on technology from vendors including VMware, HPE Nimble, Cisco, and Trend Micro, and is delivered from a WW network of data centres. The customer manages all 11:11 solutions through a single unified console. The following services are built on the technology and cloud services acquired from iland.
11:11 Cloud Backup for Veeam Cloud Connect provides secure cloud storage for protection vs. internal and external threats using Insider Protection, as well as cost-effective retention of long-term backups. 11:11 DRaaS for Veeam integrates the customer’s on-premises Veeam environment with an extension to 11:11’s cloud infrastructure, giving secure replication and failover in the 11:11 cloud.
11:11 DRaaS for Zerto offers flexibility, customized runbook functionality, optimized RPOs and near-zero RTOs, providing control the customer’s DR with rapid, automated failover and failback. 11:11 Drive for Azure, also based on Zerto, supports protection for Hyper-V and VMware environments with Azure-based DR capabilities.
11:11 Managed Backup for Cohesity is a managed service that covers all the on premises Cohesity components and removes the complexity associated with this legacy backup infrastructure.
11:11 Cloud Backup for Microsoft 365 covers the retention and compliance gaps inherent with Microsoft 365 and protects critical productivity data, including Exchange, SharePoint, and OneDrive files, contacts, and emails.
11:11 Autopilot Managed Recovery for DRaaS combines people, process, and firm’s DRaaS platform to deliver a fully managed DRaaS solution to meet specific business recovery needs.
The company offer a combination of security, backup, and recovery solutions that work together to provide a multi-layered approach to address ransomware and other forms of cybercrime. These include automated vulnerability scanning with malware and antivirus detection. All data is encrypted, and backup data is protected in immutable storage.
The services provided allow the customer to control the data centres in which the protected data is held. The services are independently attested/certified to over 20 geographic compliance and industry security standards including HIPAA, ISAE 18 SOC2, ISO27001, PCI-DSS, as well as NIST800-57 Key Management.
Organizations looking for a cloud based managed BaaS and DRaaS should consider 11.11 Systems cloud backup and DRaaS.
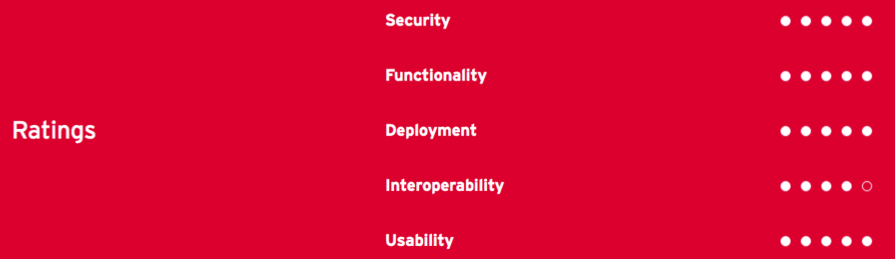
Table 3: 11.11 System’s rating
Strengths
- Full service DRaaS with options and tooling.
- Single console for on-premises VMware environment and Microsoft Office 365.
- Comprehensive functionality that covers multiple use cases.
- Control over the geographic location of backup data.
- Built on proven technology from VMware giving strong capabilities for VMware environments.
- Unified protection for on-premises and cloud VMware environments through partnership with Veeam.
- Comprehensive coverage of Microsoft Office 365 apps and data types.
- Office 365 backup includes unlimited encrypted storage and retention.
- Includes S3 compatible object storage with encryption by default.
- Optimized RPOs and near zero RTOs.
- Integrated encryption and de-dupe.
- Attested security and compliance of services provided.
- Additional services included with all 11.11 solutions.
Challenges
- Integrating and rationalizing the technology and services from the SunGard acquisition.
- SaaS protection is limited to Microsoft Office 365.
- Does not support customer retention of their encryption keys on-premises.
5.2 Arcserve – Unified Data Protection
It is a company with HQs in Minneapolis, MN. It was founded in 1983 as Cheyenne Software, Inc., and launched Cheyenne NetBack in 1988. The original Arcserve product was release 2 years later in 1990. It was then acquired by CA Technologies in 1996 and in 2014 became a private company under the ownership of Marlin Equity Partners. In March 2021, it announced the completion of its merger with StorageCraft. Its solutions include software products, hardware appliances, and cloud-based services.
Arcserve Unified Data Protection (UDP) 9, which was released in January 2023, supports hybrid BC topologies, including local backup and multiple sites, as well as cloud services and backup to cloud. It enables backup to either a local machine or a central recovery point server (RPS) with global, source-side de-dupe. It features inbuilt integration with Sophos Intercept- X Advanced for Server, providing protection vs. ransomware and a wide range of cyber threats. This solution targets midmarket and enterprise customers.
UDP 9 features a range of usability enhancements. These include the option of a cloud-based console for the user to manage all their company’s assets, new features for MSPs, support to use any S3 compatible cloud datastore as the backup destination as well as SQL Server and Oracle database improvements.
Arcserve OneXafe, is an object-based NAS appliance that features immutable snapshots to defend vs. ransomware, inline de-dupe, encryption at rest, and DR with WAN optimised replication as well as energy efficiency.
Arcserve data protection solutions protect a range of environments. These include Nutanix Hyperconverged Infrastructure with Nutanix AHV, Files and Objects integration, as well as VMware, Hyper-V, RHEV, KVM, Citrix, and Xen VMs with a selection of agentless and agent-based backups.
For IaaS, Arcserve UDP agent for Windows can be deployed on Amazon EC2 VMs. It provides protection for all the OS/Applications supported by physical machines that are supported as VMs on AWS EC2. It can also be deployed on Azure with the same capabilities.
For SaaS, the firm has 2 offerings. Arcserve SaaS Backup offers complete cloud-to-cloud backup for data stored in Microsoft 365, Microsoft 365 Azure AD, Microsoft Dynamics 365, Salesforce, and Google Workspace. Arcserve Unified Data Protection and Appliances deliver comprehensive on-premises protection for Microsoft Office 365, including Exchange Online, SharePoint Online and OneDrive for Business.
Arcserve offers a mature set of data protection solutions and has a strong user base. The solutions provide capabilities that can satisfy many use cases across organizations of different sizes from SMBs to large enterprises. The enhancements offered by UDP 9 further improve these capabilities.
Organizations looking for a mature data resiliency solution with a wide range of deployment options should consider Arcserve.
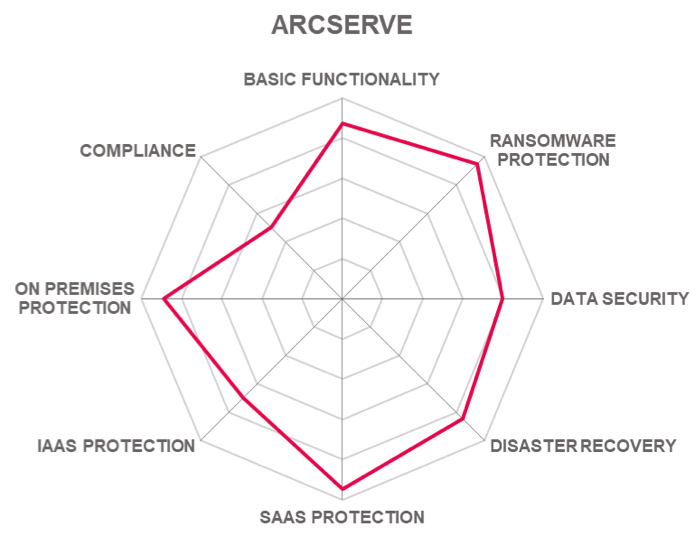
Table 4: Arcserve’s rating

Strengths
- Mature product with strong user base.
- Comprehensive functionalty covers multiple use cases.
- Supports physical, virtual, hyperconverged, and cloud environments.
- Out-of-the box protection for a wide range of databases and applications.
- Agentless VMware, Hyper-V, and Nutanix protection.
- Integrated source side global de-dupe.
- Arcserve Live Migration automatically synchronizes files, databases, and applications on Windows and Linux systems on-premises, at a remote location, or in the cloud.
- OneXafe provides an energy efficient, distributed, immutable object-store using standard storage protocols.
- Support for any S3 compatible datastore as the backup destination.
- Cloud console for integrated management from anywhere.
- Wide choice of cloud service providers for backup storage and DR.
- Provides failover capabilities for on-premises servers by transferring images to the Arcserve Cloud Hybrid datacentres.
- Arcserve UDP and Appliances protect Microsoft 365 data on-premises, in addition to other workloads.
Challenges
- UDP Backup to cloud requires an on-premises server. However, Arcserve offer Cloud Direct option if that is an issue for a customer.
- Limited integration with snapshot capabilities for major cloud services.
- Does not provide out-of-the-box support for Kubernetes backup.
- No inbuilt functionality to detect sensitive data in backups.
- No independent certification of appliances or software.
- Does not support personal data requests or eDiscovery.
- Does not support tiered long-term retention capabilities.

5.3 Clumio – Protect
It is a company backed by venture capital that was founded in 2017 and has its HQs in Santa Clara, CA. It is focused on “taking the complexity out of cloud backup and delivering an experience that is easy, flexible, and secure“. It offers Clumio Protect and Clumio Discover which are BaaS based on AWS.
Clumio Protect is a BaaS for data protection in AWS. This service protects native AWS services such as Amazon S3, Amazon DynamoDB, Amazon RDS, Amazon EC2, Amazon EBS, SQL Server on Amazon EC2 as well as VMware cloud on AWS. This is based on a highly scalable serverless architecture that is designed to cater for the data protection needs of big data. For example, Clumio Protect for Amazon S3 can scale to 30 billion objects per customer bucket, measuring exabytes. This architecture also enables rapid restoration by running I/O operations across restore blocks. Clumio Protect provides an “instant access” capability to access backed up S3 buckets while rehydrating.
Clumio Protect for Microsoft 365 enables secure cloud Backup for Microsoft 365 covering Microsoft 365 Exchange, OneDrive, SharePoint, Contacts, and Calendars.
Data is continuously backed up and the backup data is secured in Clumio SecureVault. This stores the backups outside of the customer’s AWS security sphere so that they cannot be changed or deleted by cyber adversaries that have gained access to the customer’s account. Data in flight and at rest is encrypted using FIPS-140 certified AES. The keys are held in the cloud under the control of the customer. It also provides longer term retention capabilities at reduced cost.
The service provides the customer with role-based access control and strong (MFA) authentication capabilities. It features inbuilt detection of abnormal administrator activity that could indicate a cyber-attack.
To support compliance and audit needs around data protection Clumio Discover provides enhanced reporting and deeper visibility into AWS. It helps the customer to find anomalies such as missed backups and get recommendations, get an overall view of AWS assets, identify assets at risk to ensure that all data is protected and assess the risk of ransomware.
Clumio provides an innovative backup and restore solution that should be considered by organizations using AWS for big data.
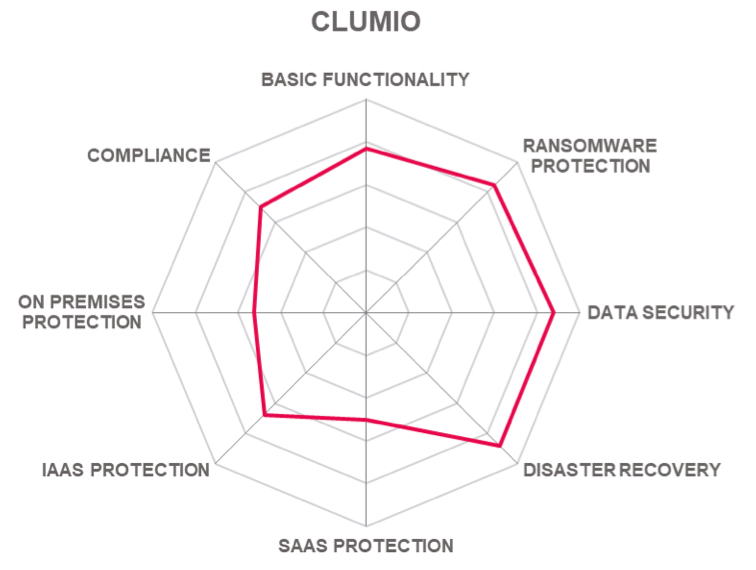 Table 5: Clumio’s rating
Table 5: Clumio’s rating
Strengths
- Native AWS protection for AWS workloads.
- Unique capabilities to protect big data.
- Massively scalable innovative serverless architecture.
- Exabyte scale data protection for AWS data lakes.
- Scalable data protection capabilities for massive Amazon S3 buckets.
- Zero-RTO recovery alongside continuous backup, in addition to parallel data rehydration in/out of the region.
- Rapid deployment – no need to deploy anything on the customer’s AWS account.
- Protection for data held in a wide range of AWS services.
- Simplicity of use through and agentless SaaS solution.
- Protection groups simplify protection of S3 objects, buckets, and prefixes across all AWS accounts.
- S3 “Instant Access” provides access to backed up S3 buckets while rehydrating.
Policy based control over backup processes. - Secure encrypted storage of backup data in AWS.
- Customers can bring their own keys and allow their customers to bring their keys.
- “Air gap” immutable storage protects vs. attack on customer’s accounts.
- Protection for data held in Microsoft Office 365 environments.
- Protection for VMware environments in AWS and at the edge.
- Support for long-term reduced cost storage of data within AWS.
- Good capabilities to support regulatory compliance activities related to data protection.
Challenges
- Backups can only be stored in AWS.
- No support for workloads outside of AWS except for VMware.
- No support for other common SaaS such as Google Workspace or CRM such as Salesforce.
- No inbuilt scanning of backup data for malware.
5.4 Cobalt Iron – Compass
It is a private company founded in 2013 with HQs in Lawrence, KS. Its focus is on smart, secure, and automated backup and DR. This report covers Cobalt Iron Compass, which provides enterprise backup functionality as a SaaS solution.
The Compass architecture comprises 3 major components – Commander, Analytics Engine and Accelerator. Commander provides a single pane of glass web dashboard, while the Analytics Engine delivers the intelligence and insight. The Accelerator is a converged, integrated, and scalable enterprise data protection system that is constantly maintained and updated. The Accelerator is delivered as software and can be hosted in the data centre or in cloud depending upon the customer’s requirements. The Analytics Engine analyses the metadata from data protection operation and provides this to the Accelerators to automate operations, avoid problems and increase efficiency.
Compass enables protection of a broad range of platforms including on-premises, remote sites, as well as cloud services and cloud to cloud backup. Cloud services supported include Alibaba, Microsoft Azure, AWS, Google Cloud Platform, and IBM Cloud and wherever VMware is supported. It provides protection for Windows, Linux, Exchange and Domino Mail, file servers, and a wide range of databases as well including SQL, Oracle, and SAP HANA, as well as VMware. Compass also has a VTL interface that emulates tape libraries, tape drives, and tape cartridges.
Protection for major SaaS services can be provided on demand through partner plug-ins.
To protect vs. ransomware and to ensure regulatory compliance, Compass Cyber Shield provides a high level of security around the protected data. Customer security access zones provide full isolation and separation for operational independence. These ensure that the backup components and data are secured vs. a wide range of attack vectors. Data is encrypted in flight and at rest. The integrity of protected data is checked at every step with monitoring to detect abnormal access and ransomware attacks with cyber-attack recovery and validation. The solution features support data governance and auditing as well as customer control over where protected data is stored.
Cobalt Iron Compass is listed as a solution meeting the US Sheltered Harbor data vaulting standards.
It should be considered by organizations looking for a SaaS based solution providing a high degree of automation and security to simplify their backup processes.
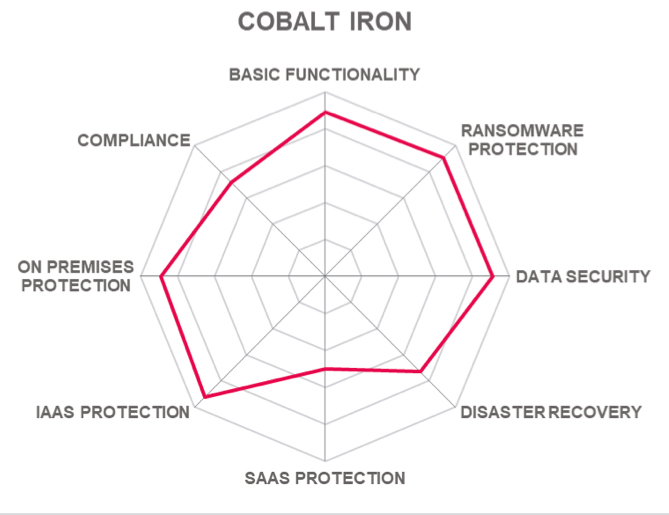
Table 6: Cobalt Iron’s rating

Strengths
- Provides a consolidated view for large organizations with complex structures. Built-in multi-tenancy capabilities.
- Actively monitors, maintains, and optimizes backup infrastructure and operations.
- Performs continual predictive failure analysis of backup infrastructure and operations.
- Identifies, analyses, and when possible, automatically remediates issues.
- Hybrid multi-cloud protection covering on-premises, Alibaba, AWS, Azure, Google, and IBM.
- Accelerator appliances are fully and automatically managed by the service with zero direct access to eliminate attack vectors.
- Data integrity is ensured through block- and object-level checksums and CRCs.
- Immutable backup storage for additional ransomware protection.
- Automated reporting of SLA achievement and security posture for audit/compliance.
- Comprehensive functionality covers multiple use cases and workloads including all the common hypervisors.
- Integrated with systems management, software distribution, ticketing, reporting, or other tools in common use including Ansible, Chef, Puppet, ServiceNow, vRealize and more.
Challenges
- Major SaaS such as Office 365, Google Workspaces, and Salesforce are not available out-of-the-box. However, they are available through tailored services for individual customers.
- No inbuilt capabilities to detect and personal / sensitive data during the backup process.
- No out-of-the box support for privacy personal data disclosure requests.
- Restore automation is provided via customization and scripts rather than full automation.

5.5 Cohesity – Cohesity Data Cloud
It is an American privately held information technology company that was founded in 2013 and has its HQs in San Jose, CA. It develops self-managed or Cohesity-managed (via SaaS) software to protect and recover their data from disasters, including ransomware, and gain insights from data, across multiple systems or cloud providers. This report focuses on the Cohesity Data Cloud.
Cohesity Data Protect Cloud is the foundation for firm’s vision for a Data Management as-a-Service Platform. This platform currently supports the following solutions:
- DataProtect and DataProtect as-a-Service that provide backup and recovery, and data protection.
- SiteContinuity and SiteContinuity as-a-Service which supports automated DR failover and orchestration.
- DataHawk is a SaaS data security solution providing threat scanning, data classification, data isolation and user data access monitoring.
Cohesity DataProtect is a software-defined solution for on-premises, public cloud, backup as a service, and edge sites. It can run in public clouds and on-premises across a range of platforms. These include virtual platforms such as VMware and Nutanix, as well as cloud – AWS, Azure, Google Cloud, and Oracle Cloud Infrastructure. It is delivered as-a-service from the AWS Public Cloud.
The same solution also offers backup and data management for SaaS applications including Microsoft Office 365 and Salesforce. It protects Exchange Online, SharePoint Online, OneDrive, Teams, and Groups. The protected data can be held on-premises, in Microsoft Azure, or as-a-service with Cohesity’s BaaS offering.
For security, data is encrypted in-flight and at-rest using software-defined AES-256, FIPS 140-2 compliant encryption. The solution features immutable backups, DataLock (WORM), encryption, and ML-based anomaly detection. Administration and management are secured through Single Sign-On, Role-Based Access Control, Multi-Factor authentication and Quorum (multi-person approval rule).
Cohesity FortKnox is a SaaS data isolation and recovery solution that improves cyber resiliency with an immutable copy of data in a Cohesity-managed cloud vault. It provides an additional layer of protection vs. ransomware based on virtual airgap enforced using the security features mentioned above.
Cohesity SiteContinuity provides automated DR failover and failback orchestration from on-prem to on-prem or cloud. It is also available as-a-service for DRaaS to the AWS public cloud. Independent of deployment mode, it includes a DR Plan builder and features automated DR Orchestration with Failover and Failback. It supports non-disruptive DR testing, asynchronous replication, and automated VMware to AWS EC2 conversion.
Cohesity DataHawk, provides multiple cloud service offerings designed to deliver data security and recovery capabilities to withstand and recover from cyber incidents. It leverages AI/ML to detect user and data anomalies that could indicate an emerging attack, utilizes threat intelligence to ensure recovery data is malware free, and with data classification enables organizations to determine the exposure of sensitive and private information when an attack occurs. It also provides data isolation as a service with FortKnox that provides an offsite SaaS solution to provide physical, network and management isolation of backup data.
Organizations looking for a modern data management platform supporting backup and recovery should consider Cohesity.
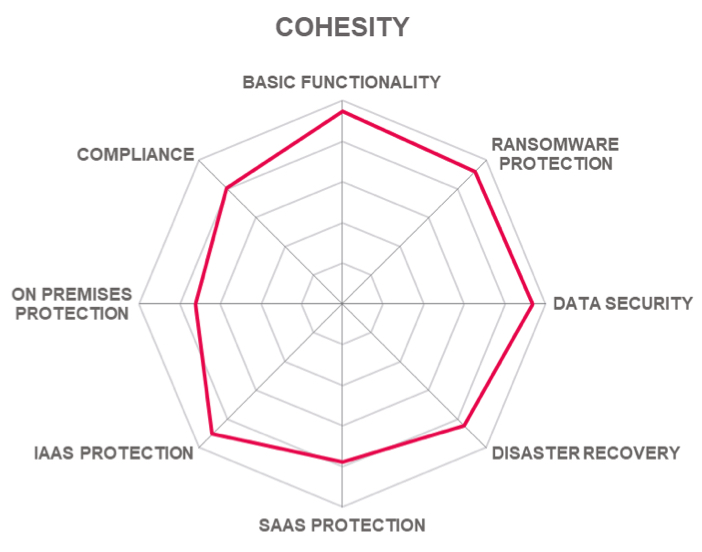
Table 7: Cohesity’s rating

Strengths
- Provides a visionary approach to a comprehensive DMaaS.
- Comprehensive functionality that covers multiple use cases.
- Software defined and can be deployed flexibly in multiple ways.
- On-premises to cloud as well as cloud to cloud backup and DR.
- Coverage of wide range of virtualization platforms, databases, NAS, & physical servers.
- Supports both VM and container-based workloads.
- Protection for big data apps like NoSQL & Hadoop.
- Protects Microsoft Office 365.
- Continuous data replication enables sub-minute RPOs and near-zero RTOs.
- Strong security features.
- Control plane is separated from the data plane.
- Cohesity FortKnox provides resilience vs. ransomware.
- Cohesity SiteContinuity supports BC planning and DR.
- Cohesity DataHawk for data intelligence and threat detection.
- Strong inbuilt data security capabilities.
- Good integration with a wide range of partner solutions.
- Extensive search capabilities to find specific instances of data.
- Challenges
- Only supports backing up M365 and SFDC business SaaS apps.
- SiteContinuity only supports VMware workloads.
- Limited independent compliance certification for the solution.
- Only delivered as a service from AWS.
- Limited inbuilt features to support privacy requests.

5.6 Commvault – Metallic Backup as-a-service
It is a publicly traded data protection and data management software company headquartered in Tinton Falls, NJ. It was formed in 1988 as a group within Bell Labs, and in 1996, it was incorporated as an independent company. It offers a range of data protection solutions. This report focusses on Commvault Metallic BaaS. This is a cloud-native solution built on and delivered from Microsoft Azure Cloud. It provides BaaS for hybrid cloud workloads as well as SaaS.
Metallic VM & Kubernetes Backup covers workloads in on-premises and cloud VMs as well as containers including VMware, Hyper-V, Azure VMs, AVS, OCI VMs, Amazon EC2, VMC, and Oracle Container Engine for Kubernetes (OKE).
Metallic Database Backup covers structured data including MySQL, Azure MariaDB, Azure PostgreSQL, Azure Cosmos DB, Oracle and Oracle RAC databases, Oracle Database Cloud Service (DBCS), Oracle Exadata Database Service on OCI, Oracle Exadata Database Service on-premises, SAP HANA, Amazon RDS, Amazon DynamoDB, Amazon DocumentDB, and Amazon Redshift.
Metallic File & Object Backup covers unstructured providing backup and recovery of servers, files, or objects including Windows Server, OCI Object Storage, Linux/Unix, Azure Blob & Files, and Amazon S3.
Metallic BaaS for SaaS offers cloud-to-cloud data protection for the Microsoft Cloud, including coverage for Dynamics 365 CRM data – production and sandbox environments – as well as Microsoft 365, including: Exchange Online, SharePoint, OneDrive, Teams, Groups, and Project Online. Free Azure AD backup is included with every paid Metallic subscription. Metallic also offers Salesforce coverage for sales cloud; service cloud; financial cloud; and health cloud, while Commvault Complete Data Protection additionally offers coverage for Google Workspace.
For security and ransomware protection Metallic delivers a multi-layered, zero-trust security to safeguard endpoints, SaaS applications, and hybrid cloud environments. Metallic Security IQ helps to spot risks and reduce threats from a single view. Metallic ThreatWise helps to defend data with fully integrated cyber deception.
For rapid recovery from incidents, Metallic features built-in de-dupe, recommended recovery points, and flexible restore controls to eliminate redundancies, ensure that data is highly available, and enable roll data back to pre-suspect states.
Metallic should be considered by organizations looking for BaaS as part of a comprehensive solution with ransomware protection for their hybrid IT environment.
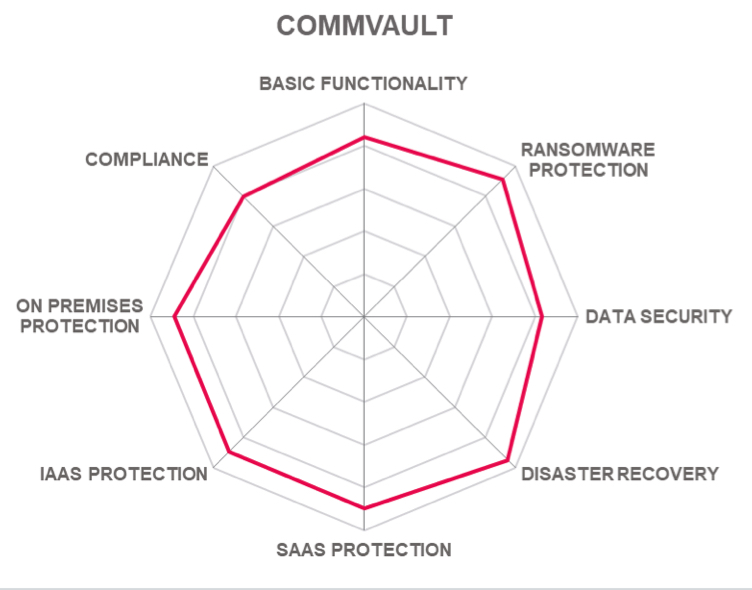
Table 8: Commvault’s rating

Strengths
- Metallic offers a BaaS for protecting data across a wide range of environments.
Metallic supports both Microsoft Active Directory and Azure Directory backup. - Metallic supports protection for a wide range of SaaS including Microsoft Dynamics 365.
- Comprehensive functionality covers multiple use cases.
- Range of solution delivery options.
- On-premises to cloud as well as cloud to cloud backup.
- Coverage of range of virtualization platforms.
- Supports both VM and container-based workloads.
- Protection for big data apps like Hadoop
.
Continuous data replication enables sub-minute RPOs and near-zero RTOs. - Strong security features such as multi-layered zero trust.
- Control plane is separated from the data plane.
- Support for SAML and MFA authentication as well as RBAC.
- With Metallic, encryption keys can be stored externally including support for AWS and Azure Key vaults.
- Customer choice over the geolocation of their backed-up data.
- Metallic offers a broad range of preconfigured and off-the-shelf reports across workloads.
- It recently introduced archive as-a-service for archival of unstructured data.
- It offers eDiscovery add-ons for M365 and endpoint solutions.
- Metallic security certifications include ISO 27001, SOC 2 Type II, PCI, FIPS 140-2, CJIS, and FedRAMP High.
Challenges
- Does not provide automated workload migration between virtualization environments.
- Does not include out-of-the-box anti-malware scanning of protected data.

5.7 Druva – Data Resiliency Cloud
Druva Inc. is a privately-held software company with HQs in Sunnyvale, CA. It provides SaaS-based data protection and management platform for organizations of all sizes. It provides “Data Resilience as-a-Service” delivered from the AWS cloud. This features capabilities to backup and restore application, workloads, and data across a range of use cases. Druva Data Resiliency Cloud is also sold as Dell Apex Backup Services.
The Druva Cloud, which is built on AWS, delivers cloud data protection and DR across endpoints, data centres, and cloud workloads. The Druva Data Resiliency Cloud provides a consolidated data repository for all backup data.
The company provides data protection for enterprise workloads including file servers, databases, NAS (on-premises and in the cloud), and virtual and hybrid environments including Hyper-V, vSphere, Nutanix AHV, as well as VMware Cloud on Nutanix, AWS, Azure and Google. It supports the recovery of server data down to the file level, failover/failback of VMware VMs, and cloud archiving of data for compliance, as well as the replication of VM workloads across regions and accounts for test/dev purposes.
The firm supports data protection for AWS workloads at enterprise scale across multiple regions and AWS accounts through a single control panel. This central dashboard gives global visibility into the entire AWS footprint. It includes capabilities for centralized snapshot policy orchestration, DR, and VPC cloning capabilities across the organization’s AWS environment, with support for Amazon Elastic Compute Cloud (EC2), Amazon Elastic Block Store (EBS), Amazon Relations Database Service (RDS), Amazon DynamoDB, Amazon Redshift, Amazon EKS, Amazon Document DB, and Amazon Neptune.
It supports SaaS backup and protection for Microsoft OneDrive, Exchange Online, SharePoint, and Microsoft Teams. It also offers a solution to protect Google Workspaces as well as Salesforce data.
For ransomware its cloud-native architecture protects data and speeds up recovery. Backups are stored off-site in a different account not connected to your network. Immutable object storage protects backups vs. change. Built-in malware scanning prevents reinfection from contaminated snapshots.
Druva secures backup data using encryption both in-flight (TLS) and at-rest (AES-256). Backup data is stored offsite in the Druva Cloud, accessible only by the Druva cloud, creating an “air gap” from customer networks. It exploits several security technologies to prevent unauthorized access to or modification of the backup data. These include IAM and bastion hosts, RBAC, and MFA, and it does not allow SSH access to Druva’s production system. The vendor exploits ML-based anomaly detection to further protect customer data.
It also supports DR for AWS based and on-premises workloads.
Organizations looking for a modern cloud-based Data Resilience as-a-Service solution with strong support for AWS and SaaS coverage should consider Druva.
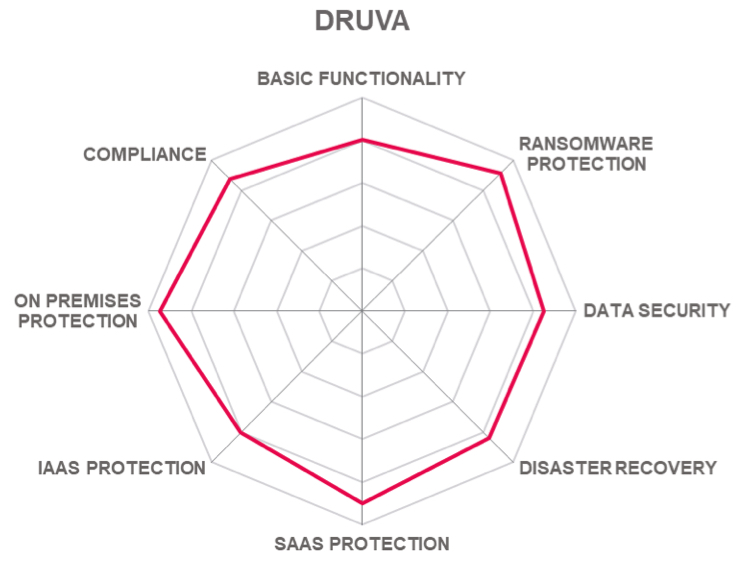
Table: X’s rating
Strengths
- Delivered as a SaaS solution.
- Built on AWS which offers a range of geographic locations and HA.
- Offers protection for services deployed in cloud, on-premises, and edge.
- Global source side de-dupe of data.
- Support for VMware and Hyper-V, and Nutanix AHV VMs.
- Protection for Microsoft Office 365, Google Workplaces, and Salesforce SaaS.
- Comprehensive AWS workload support.
- Comprehensive legal and compliance capabilities.
- AWS S3 provides triple redundancy and durability of protected data.
- Multiple layers of security to protect the backed-up data.
- Archive storage tier for ultra-low cost, long-term retention for compliance needs.
- One-click failover and failback, no AMI conversion for VMs.
- Automated recovery orchestration and runbook execution.
- Capabilities to DR into customer VPC and clone VPC across regions or accounts.
- Accelerated Ransomware Recovery which includes anomaly detection, quarantine, malware scanning, and curated snapshots (for select workloads).
Challenges
- Managing the partnership with Dell.
- Only delivered from AWS.
- Only supports AWS for storing backup data.
- Depends upon AWS for many security capabilities.
- Does not support cloud native VM snapshots and recovery.
- Limited range of DBaaS protected.
- Does not support TLS 1.3.

5.8 HYCU – Protégé
It is a privately-held company with HQs in Boston MAA. It provides SaaS-based backup and recovery to on-premises, cloud-native and SaaS environments, enabling data protection, migration, DR, and ransomware protection.
Protégé provides backup, data mobility and DR across multiple clouds. It features application aware and consistent backup, recovery and migration for on-premises and public cloud environments. It is built using modern application architectures that ensure the scalability needed to support the massive amounts of data found today’s organizations.
Protégé is delivered as a virtual appliance for on-premises and Backup as-a-Service for public cloud. Firm’s user interface is tailored to each platform’s native terminology and interface. HYCU features integrations with Nutanix, VMware, Google Cloud, Azure, and AWS which leverage each platform’s native functionality. It is agentless by design and its intelligent communications exploits the APIs provided by the protected environments.
The firm does not store or control the customers data – the customer has complete control over what data is protected and where it is stored. As well as providing capabilities to migrate on-premises workloads to the cloud it features policy-based backup and ransomware protection. It exploits the access control capabilities provided by the protected environments and partners with Okta for IDaaS. The customer has control over how their data is encrypted and the encryption keys.
Supported applications and files services include SQL Server, Exchange Server, Microsoft Active Directory, Oracle Database, Nutanix Files, SQL Failover Cluster and SAP HANA. The backup data can be held in a range of storage including on-premises: NAS (NFS/SMB), Nutanix Files, ExaGrid, DataDomain, Quantum, Azure Blob, AWS S3, GCS, Nutanix AOS Services, Cloudian, Scality, S3 Compliant storage, iSCSI – Nutanix Volumes, and Nutanix Mine Cloud: Cloud native Object.
To protect the increasing number of SaaS environments, the vendor recently announced their R-Cloud. This is a low-code development platform that provides an easy way for SaaS providers and ISVs to deliver data protection for their platforms as-a-service. This is now in preview and the first SaaS-based applications, databases, and services supported in R-Cloud will include: Amazon RDS, Google Cloud SQL, Google Workspace, Google BigQuery, Salesforce, Confluence, Jira, Jira Service Management, and Microsoft 365. New application integrations will be available through the Protégé Marketplace.
Organizations looking for a SaaS-based backup and DR solution covering a wide range of business applications including those delivered as SaaS should consider Protégé with R-Cloud.
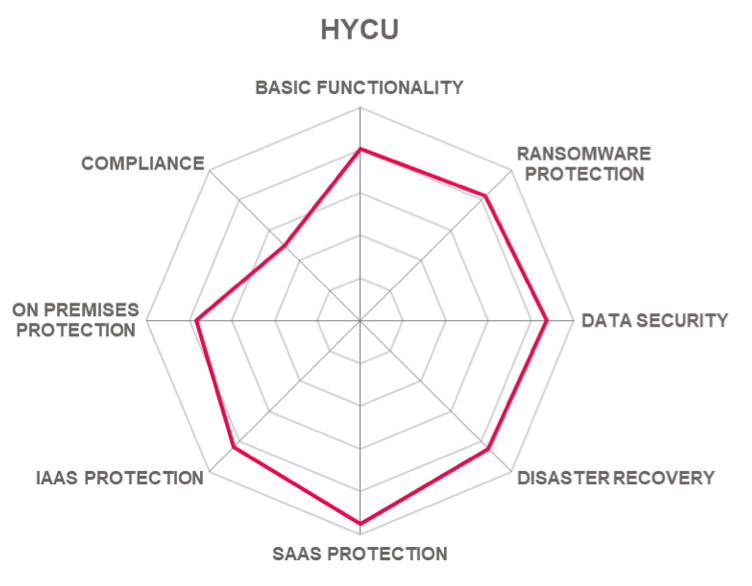
Table 10: HYCU’s rating
Strengths
- A visionary approach to reduce the burden of backup and DR.
- Delivered as a SaaS service.
- Built with a highly scalable architecture.
- Provides protection for a wide range of environments.
- integrations with Nutanix, VMware, Google Cloud, Azure, and AWS.
- Native integration with major cloud VM types and storage.
- Out-of-the-box support for Kubernetes environments.
- Wide range of application and databases supported.
- Customer data is never stored by HYCU: the customer is always in control of their data.
- No data egress costs when backing up data to same cloud.
- Agentless approach reduces deployment and management effort.
Uses UI styles or protected environments to reduce training needs. - Backup validation to protect vs. ransomware.
- Automated detection of insecure backup targets.
- R-Cloud capabilities to extend the range of SaaS, DBaaS and data lake coverage.
- R-Cloud opportunities to increase HYCU ecosystems.
- Challenges
Not well known in Europe.
- Limited independent certification of the services provided.
- No inbuilt integration with data management tools (e.g., to add protection to specific baked up data).
- No out-of-the-box capabilities for compliance needs such as PII data subject requests.

5.9 Kaseya – IT Complete and BCDR
It is a privately-held company with its HQs in Miami, FL. It provides unified IT management and security software for MSPs and SMBs. These are delivered through its IT Complete platform which features a single console and workflow integrating the range of IT management and security capabilities needed by customers.
IT Complete Backup and BCDR is a fusion of products and technologies acquired from several companies. These are accessed from a common console and are integrated with other related company’s solutions through workflows.
It provides 2 solutions for different target markets which have differing needs. For SMBs the solution is based on what was previously Unitrends Backup and DRaaS. For MSPs the solution is based on what was known as DAtto Unified Continuity.
For SMBs the solution provides one-screen management for multiple types of backups (servers, endpoints, and SaaS) across multiple locations, customer sites, and tenants. From a single user interface with 2-factor authentication, users also benefit from BackupIQ, which tailors alerts so that IT gets only the notifications they need. It provides virtual and physical protection of over 250 versions of OSs, hypervisors, and applications. This includes host and guest level protection for vSphere, Hyper-V, Nutanix AHV, and Xenserver. It also includes SaaS backup for Microsoft 365, Google Workspace (formerly G Suite), and Salesforce.
For MSPs, the solution comprises a number of components that are intended to meet the BC and DR needs of their clients of various sizes. These include SIRIS, an all-in-one BC and DR solution; ALTO, a small BC and DR solution; SaaS Defence – cloud-to-cloud backup for Microsoft 365 and Google Workspace; Continuity for MS Azure – backup and recovery for workloads in Azure; Cloud Continuity for PCs – a cloud backup for Windows-based computers; File Protection – file and folder backup service for devices such as workstations and laptops. It also supports DAtto Inverse Chain Technology to ensure rapid and reliable backup and data recovery since every snapshot represents a point-in-time recovery.
To secure the backed-up data, the solutions support AES 256 encryption as well as 2-Factor Authentication and immutable backup storage. AI is used in every backup, to analyse and detect the file changes that characterise a ransomware attack. Upon detection, alerts are immediately sent to administrators and all suspected backups are flagged with a warning icon.
Small businesses and MSPs looking for a Backup and DR solution that is tailored to their needs and forms part of a complete IT management and security platform should consider this offer.
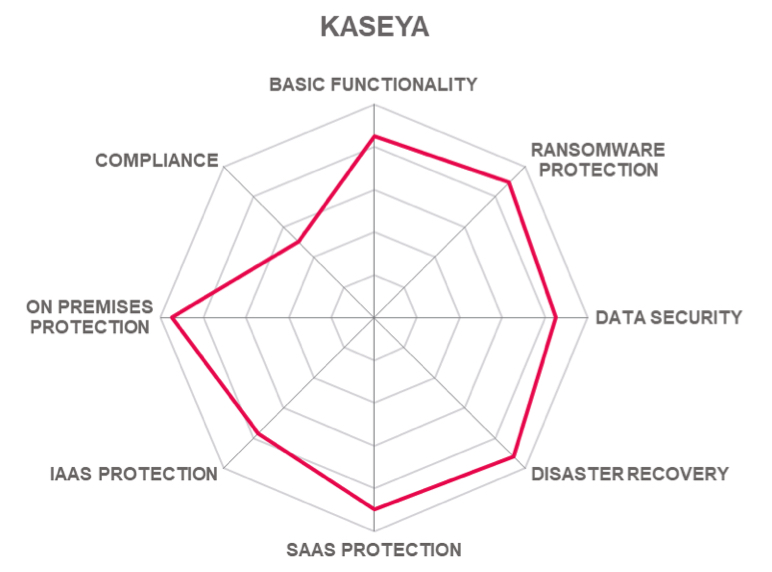
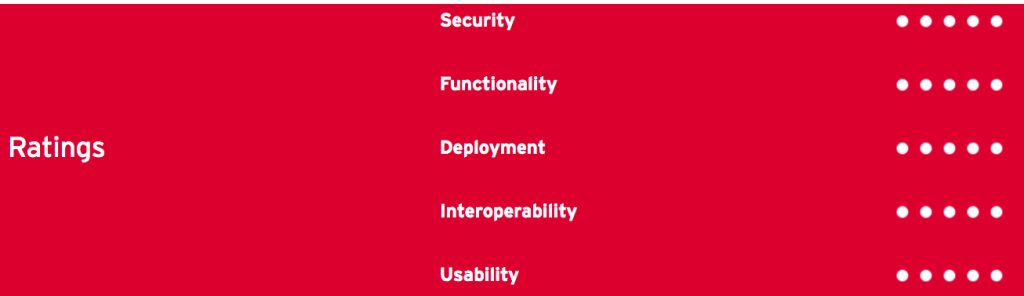
Table 11: Kaseya’s rating

Strengths
- Part of a complete IT management and security platform.
- Tailored to the needs of SMBs and MSPs.
- Single console with integrated capabilities.
- Flexible deployment options cloud, software, and appliance.
- Provides protection for a range of environments.
- Complete system image backup and file or image level restore.
- Granular backup down to 5mn increments.
- Application and database support includes SQL Server, Exchange Server, and Microsoft AD.
- Backup protection for Microsoft 365, Google Workspace, and Salesforce.
- Inverse Chain Technology backup with patented Fast Failback to revert to the original system.
- 2-factor authentication to console logon.
- Cloud Deletion Defense to “undelete” malicious or accidental agent or backup snapshot deletion.
- Multiple recovery options including file or folder restore, rapid rollback to quickly undo widespread changes such as ransomware infection.
- Image Export for full virtual server restore and Bare Metal Recovery to re-image a server to new hardware.
- Challenges
Does not support continuous backup.
- Limited clouds supported for backup storage.
- End customer control over where their data is stored in the cloud.
- No out-of-the box support for Kubernetes workloads.
- No out-of-the-box support for cloud data lakes and big data.
- Regulatory compliance capabilities provided through an additional solution.
- Limited independent certification of the services provided.
Table 12: NAVIKO’S rating

5.10 NAKIVO – Backup & Replication
Founded in 2012, it is a US-based privately funded company that delivers a backup and recovery solution to meet the data protection needs of SMBs and enterprises across a wide range of industries.
NAKIVO Backup & Replication can protect virtual, physical, cloud, and SaaS environments. It can create incremental backups to protect vSphere, Hyper-V, and Nutanix AHV VMs as well as create image-based, incremental backups of Amazon EC2 instances. It can also protect Windows-based and Linux-based physical servers and workstations as well as data held in SQL Server databases and in Exchange Server. In addition, it can protect Microsoft 365 data through incremental backup of data in Exchange Online, Teams, OneDrive for Business, and SharePoint Online.
For protection vs. ransomware, Backup & Replication supports air-gapped backups to physical media. It features ransomware-resilient backups through enabling immutability for backups sent to local Linux-based repositories as well as repositories deployed as part of a preconfigured hardened virtual appliance or an Amazon Machine Image. In addition, it can create immutable backups in Amazon S3, Wasabi, Backblaze B2, and Azure Blob Storage to protect backup data vs. changes and encryption by malicious actors.
Backup & Replication makes it possible to recover VMs, files, and application objects directly from backups. The recovery capabilities include boot of vSphere and Hyper-V VMs directly from backups. P2V (Physical to Virtual) allows recovery of physical machines from backups as vSphere VMs. It supports granular recovery of objects in Exchange Server, Microsoft Active Directory and SQL Server as well as Cross-Platform Recovery to export VM disks across platforms to recover VMware VMs to a Hyper-V environment and vice versa.
For DR, Backup & Replication can perform VM replication and orchestrate the DR process with the built-in Site Recovery functionality. This includes VM Replication to create and maintain vSphere and Hyper-V VM replicas as well as Amazon EC2 instance replicas. It supports one-click site recovery for DR workflows and scheduled non-disruptive recovery testing, planned failover, emergency failover, failback, and datacentre migration.
Organizations looking for an affordable and reliable backup and recovery solution should consider this ofering.
Strengths
- Mature solution with wide user base.
- Protection for vSphere, Hyper-V, and Nutanix AHV VMs.
- Tiny footprint, OS independent can be installed on NAS.
- Protection for Windows-based and Linux-based physical servers.
- Coverage for Oracle and SQL Server databases.
- Supports protection for Microsoft 365 data in Exchange Online, Teams, OneDrive for Business, and SharePoint Online.
- Support for VMware Cloud Director backup.
- Send backups to public clouds, including Amazon S3, Wasabi, Backblaze B2, and Azure Blob Storage as well as other S3-compatible platforms.
- Ransomware protection through air gap, immutable backups to public/private cloud and local hardened Linux-based repositories.
- Recovery of VMs, files, and application objects directly from backups.
- Built-in Site Recovery functionality to orchestrate the DR process.
- Range of deployment options include a- virtual appliance/AMI, on Linux, on Windows OS, or on a NAS to create an all-in-one backup appliance.
- Supports de-dupe of backup data.
- Security features include support for RBAC and 2-Factor Authentication.
Integration with Microsoft Active Directory. - APIs to integrate with monitoring, automation, and orchestration solutions.
Challenges
- SaaS support limited to Microsoft Office 365.
- Limited set of database types with out-of-the-box native support.
- Limited out-of-the-box support for cloud-based DBaaS (database as-a-service).
- No out-of-the-box integration with malware scanners.
- Proprietary encryption of data in flight.
- No out-of-the-box support for Kubernetes.
- No certification/attestations vs. common security standards, laws, and regulations.
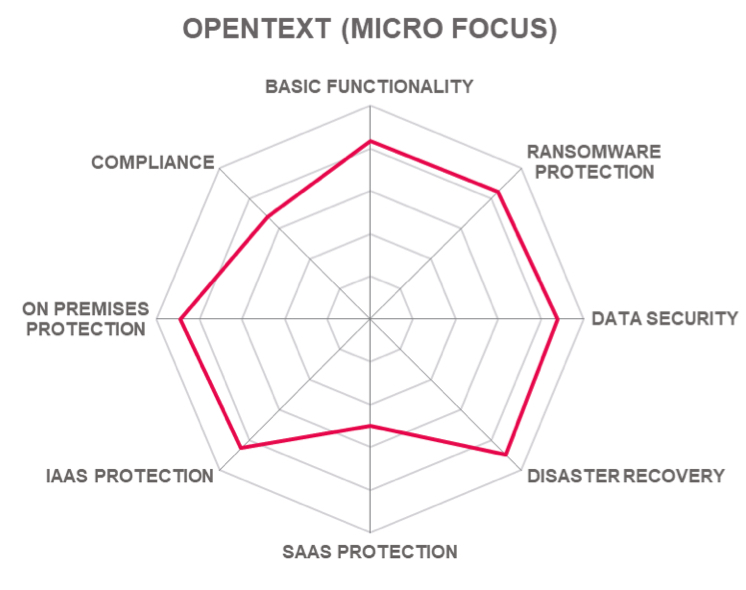
Table 13: OpenText’s rating

5.11 OpenText (Micro Focus) – Data Protector and Cloud Data Protector
Micro Focus is a global infrastructure software business that was founded in 1976 and headquartered in Newbury, UK. In January 2023, OpenText completed its acquisition of Micro Focus through its wholly-owned subsidiary, OpenText UK Holding Limited.
OpenText-Micro Focus Data Protector is a backup and DR solution for large, complex, and heterogeneous IT environments. It is offered in 2 editions: Data Protector Premium which supports hybrid environments (virtual and physical), and Data Protector Express designed for backup and restore of virtual environments. Data Protector enables data protection across a range of locations, applications, formats, storage platforms, OSs, and hypervisors to a range of backup targets, including disk, tape, and cloud.
It provides application consistent recovery for a range of business applications with backup, automated point-in-time recovery, and granular restores.
Applications protected include Exchange, SharePoint, SQL, Oracle, SAP, SAP HANA, DB2, Sybase ASE, PostgreSQL, and MySQL.
Data Protector for Cloud Workloads is a Data Protector extension that provides wider backup protection in cloud, virtual, container, and online application environments. It gives multiple options in the choice of hypervisors that can be deployed and enables flexibility in the choice of cloud provider backup targets. Online application data protection is provided for Microsoft 365 suite of products including Exchange Online, SharePoint Online, OneDrive for Business, and Teams.
For security, network traffic and data are encrypted using AES 256-bit encryption before these are transferred over the network and written to media. The customer has the manual control over encryption keys via the command-line interface (CLI). Common Criteria Certification provides assurance of the application of rigorous processes, implementation, and evaluation of software security.
For protection vs. and recovery from ransomware, Data Protector supports the 3-2-1 rule allowing to keep multiple backups in different locations. Backup data can be protected in WORM storage and physical copies of backups provide an addition layer of protection. It integrates with the customers’ malware scanning tools to protect vs. restoring infected data.
It provides automated DR with centralized bare-metal recovery from or to physical and virtual systems from any backup set at no additional cost. DR images can be created from any existing file system or image backup including object copies, without needing to create a separate special backup for system recovery.
Organizations with legacy and hybrid IT protection requirements including Microsoft Office 356 Exchange should include this on their shortlist of products for consideration.
Strengths
- Mature product with strong user base.
- Comprehensive functionality covers multiple use cases.
- Flexible deployment options.
- Integration with VMware and Hyper-V for virtual server protection.
- Integration with leading DBMS and business applications for consistent protection.
- Protection for AWS, Azure, and Google Cloud native VMs.
- Protection for Microsoft 365 applications data.
- Integration with storage arrays for rapid recovery and efficiency.
- Choice of cloud as a backup storage tier.
- Automated bare-metal recovery.
- VM restore and migration capabilities.
- Strong security features.
- WORM storage and air gapped protection of backup data.
- Common Criteria Certification.
Challenges
- Managing the integration between Micro Focus and OpenText.
- The solution does not provide native protection for Azure and GCP workloads.
No protection for common enterprise SaaS such as CRM. - Although it can be deployed in the cloud, there is no SaaS offering.
- No out-of-the-box protection for cloud-based NoSQL databases and data lakes.
- Requires integration with other DLP tools to manage sensitive data in backups.
- No support for DR runbooks, workflows, or orchestration.

5.12 Veeam – Backup & Replication
Veeam Software is a privately-held company that was founded in 2006 and was acquired in 2020 by Insight Partners. It develops and sells backup, DR, and intelligent data management software for virtual, physical, and multi-cloud infrastructures. This report focuses on its Backup & Replication v11. A new version v12 has recently been released, that provides additional features including direct to object storage backups, a much simplified and secured Veeam Hardened Repository setup wizard and additional immutability options.
Backup & Replication is a data protection solution for data on-premises, in the cloud or through BaaS or DRaaS via Veeam Partners. It is a single data management and protection platform for cloud, virtual, physical, SaaS, and Kubernetes environments. It covers AWS, Microsoft Azure, and Google Cloud Platform, vSphere, Hyper-V, and Nutanix HCI (AHV and RHV hypervisors) and physical environments including Windows, Linux, Mac, IBM AIX, and Oracle Solaris and file shares as well as Microsoft, Oracle, and SAP applications.
Veeam Backup for Microsoft 365 provides protection for Exchange Online, SharePoint Online, OneDrive for Business, and Microsoft Teams. The backed-up data can be held on-premises or in cloud object storage – including AWS S3, Azure Blob, IBM Cloud, Wasabi, and S3 compatible providers. Veeam Backup for Salesforce includes a free community edition for organizations with 50 or fewer Salesforce user licences.
To protect the confidentiality of backed-up data, Backup & Replication uses a block cypher encryption algorithm at the data source side. It reads VM or file data, encodes data blocks, transfers them to the target side in the encrypted format, and stores the encrypted data in the backup repository. The protected data is only decrypted on the source side. V11 uses FIPS-compliant encryption modules.
To defend vs. ransomware, it supports immutable backups based on the native Linux file immutability feature, which restricts modification and deletion of files with the corresponding flag set. The flag can only be removed by a user with root privileges, but the single-use credentials ensure root credentials are not stored on the backup server and are recommended for use of the Hardened Repository.
Veeam Recovery Orchestrator provides orchestration of recovery from Veeam-powered backups, replicas, CDP replicas, and storage snapshots. It supports DR planning by automatically testing, documenting, and executing DR plans from single applications to entire sites.
Organizations looking for a comprehensive data protection solution should consider Veeam Backup & Replication.
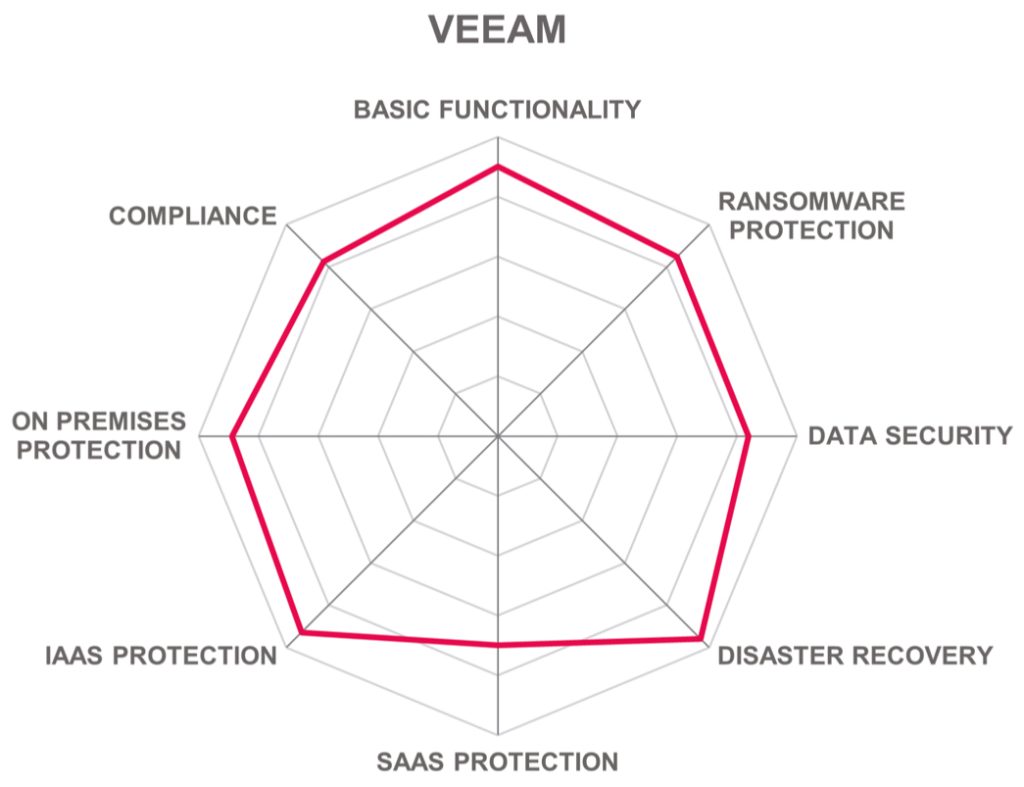
Table 14: Veeam’s rating
Strengths
- Mature product with strong user base.
- Comprehensive functionality covers multiple use cases.
- Integration VMware and Hyper-V for virtual server protection.
- Provides protection for major hyperscale IaaS environments.
- Offers a wide choice of storage options for backed up data.
- CDP captures write operations in near real time.
- Multi-VM Instant recovery.
- Immutable ransomware-proof backups.
- Industry standard FIPS certified encryption.
- Customer has control over the encryption keys.
- Integration with some DBMS and business applications.
- Includes support for Office 365 and Salesforce.
- DR Orchestrator supports self-service DRaaS.
- Strong MSP partnerships provide managed services using Veeam.
Challenges
- Depends upon cloud service capabilities for control over cloud data location.
- Additional product (Kasten K10) needed for Kubernetes backup.
- Does not provide protection for Google Workspace.
- V11 does not support MFA (although this is now included in v12).
- DRaaS provided through partners.

5.13 Veritas Technologies – NetBackup 10.1
It is a global business with HQs in Santa Clara, CA. In 2014, it was divested from Symantec and is now owned by the Carlyle Group. It has a focus on helping its customers to discover and protect their data. This report focuses on NetBackup 10.1.
This prodict is built on Veritas Cloud Scale Technology. This is a new gen of the NetBackup architecture designed to benefit from cloud environments. It leverages the scalability and flexibility of the cloud, while providing the consistency and a single interface to protect the entire IT infrastructure. It supports a range of servers, storage, hypervisors, databases, applications, and cloud platforms. It covers multiple use cases (backup to the cloud, archive to the cloud, DR to the cloud, DR in the cloud) as well as new virtualization technologies (Kubernetes, Docker, Red Hat Virtualization, OpenStack, and fully agentless VMware). An integrated SaaS based option – Veritas Alta SaaS Protection – protects SaaS applications including Microsoft Office 365, Salesforce and Google Workspace.
NetBackup supports cloud storage providers such as AWS, Microsoft Azure, and Google Cloud Platform (GCP). It de-dupes data before it is transferred and stored in the cloud and supports cloud tiering for long-term retention through Azure, Google Cloud Platform Archive, and AWS Glacier. To defend vs. ransomware, NetBackup 10.1 exploits cloud-native immutable storage for Amazon S3 Object Lock, Azure, and Seagate Lyve Cloud which prevent changes to the protected data.
It enables data security and integrity through system hardening and Immutable and Indelible Image Management and Storage, data encryption (both in-transit and at-rest). Identity and Access Management features Role-Based Access Control (RBAC) and Multi-Factor Authentication (MFA). It includes built-in anomaly detection using AI and ML to detect suspect behaviour and act when ransomware strikes. It integrates with a range of SOAR/XDR platforms.
NetBackup helps organizations to recover from a range of disaster scenarios including environmental issues, human failure, and security incidents such as ransomware. It enables the multiple RTOs and RPOs needed to support business service recovery to, in, and across clouds. It supports flexible recovery workflows and includes malware scanning of recovered data. It provides capabilities to discover, protect, and recover all application components across any Kubernetes distribution, on-premises or in the cloud.
Organizations with a hybrid IT environment (including IaaS, PaaS as well as the range of SaaS services covered) looking for a data protection solution should include this on their shortlist of products for consideration.
F44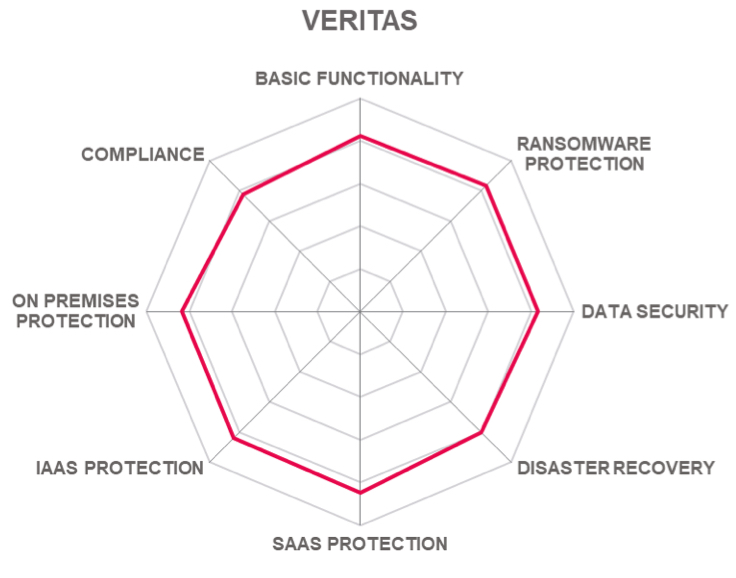
Table 15: Veritas’s rating
Strengths
- Mature product with strong user base.
- Part of a comprehensive suite of data protection and resiliency products.
- Comprehensive functionality covers multiple use cases.
- Integration with range of hypervisors for virtual server protection.
- Integration with leading DBMS and business applications.
- Supports cloud-to-cloud protection of workloads in major IaaS clouds.
- Native support for Kubernetes workloads.
- Full support for Microsoft Office 365, Salesforce, and Google Workspace.
- Support for Box and Slack and for Salesforce announced on February 16, 2023.
- Choice of cloud as a backup storage.
- Cloud autoscaling – dynamically re-sizes cloud resources as required.
- AI/ML based anomaly detection of changes to backup data.
- CDP and Instant Rollback for VMware.
- Exploits Immutable storage on AWS S3 and Azure for added protection.
Challenges
- Depends on partners to deliver managed DR.
- Limited independent compliance certification of the solution.
- F46
- Six vendors to watch
- Besides the vendors covered in detail in this document, we observe some other vendors in the market that readers should be aware of. These vendors may not fully fit the market definition but offer a significant contribution to the market space. This may be for their supportive capabilities to the solutions reviewed in this document, for their unique methods of addressing the challenges of this segment or may be a fast-growing start-up that may be a strong competitor in the future.
There is a large number of vendors that provide backup products and services. It is not practical to include them all here. This list is a selection of ones with a cloud-based backup for business focus.
Acronis
It was founded in Singapore in 2003 and incorporated in Switzerland in 2008. The company provides a range of data protection and DR solutions including Acronis Cyber Protect and Cyber DR Service using its cloud services.
Why to watch – Acronis offer a backup as part of a complete Cyber Protection package that covers the five areas of cyber security – prevention, detection, response, recovery and forensics – through a single solution.
Atempo
It is a French company with HQs in Paris, France. It provides solutions to SME and corporate organizations to “preserve data ecosystems” across endpoints, applications, servers, including big data and in the cloud.
Why to watch – It treats data as a vital organisational ecosystem that is constantly evolving and provides solutions to help to maintain the equilibrium of that ecosystem and protect it vs. threats.
AWS
It is a global provider of cloud services. AWS Elastic DR is an AWS service that enables organizations to minimize downtime and data loss with fast, reliable recovery of on-premises and cloud-based applications.
Why to watch – AWS Elastic DR is the service recommended by AWS for DR to AWS.
Claranet Group Ltd.
It provides networking, Internet hosting, and managed cloud services. It was founded in 1996 and has its HQ in London, UK. It provides a backup service for Microsoft Office 365 with unlimited storage and powerful search capabilities.
Why to watch – Microsoft Office 365 contains sensitive data that is vital to the survival of most organizations. Many SMBs do not understand the need to backup.
Code42
It is an American cybersecurity software company based in Minneapolis, MN, specializing in insider risk management. It offers Crashplan which is backup and recovery software for small businesses. The backed-up up data is encrypted to support regulations such as HIPAA.
Why to watch – the increasing ransomware attacks on SMBs and data protection regulation make this a growing market.
Databarracks
It is a UK company that offers a complete BaaS, DRaaS, and BC as-a-Service based on the use of cloud.
Why to watch – this is an organization with a reputation for offering an end-to-end service.
Dell Technologies
It is a multinational corporation with HQs in Round Rock, TX. Its solutions include servers, storage, data protection, networking, and information security.
Why to watch – It provides a range of data protection and backup products including Dell APEX Backup Services which is a rebadged version of Druva.
Ekco
It is an Irish company offering cloud backup and DR based on datacentres within the EU. It protects data on physical and virtual servers, endpoints, and in the cloud. Ekco offers a fully managed cloud backup.
Why to watch – EU-based SMBs need data protection that is fully compliant with EU data protection regulations.
Expedient
With HQs in Pittsburgh OH, it provides suite of DR solutions for both virtual and physical environments, with RPOs and RTOs.
Why to watch: Expedient’s Push Button DR offers rapid, total network failover between disparate locations at the push of a button, without IP or DNS changes.
Google Cloud Backup and DR
In December 2020 Google acquired Actifio a cloud backup solution which was already available from the Google Cloud marketplace.
Why to watch – In September 2022, Google Cloud announced Google Cloud Backup and DR: a managed backup and DR service for centralized data protection.
IBM Cloud Backup
It is a full-featured, automated, agent-based backup and recovery system managed through the IBM Cloud Backup WebCC browser utility.
Why to watch – this is part of a wide portfolio of data management hardware, software and services solutions from IBM for data resilience and ransomware protection.
Microsoft Azure Site Recovery
Microsoft offers several features to help tenants achieve BC. These include HA through availability sets and zones, Azure Site Recovery, and Azure Backup for data protection.
Why to watch – Azure Site Recovery can replicate and protect IaaS based applications running on Azure as well as on-premises which makes it attractive to Microsoft centric hybrid IT deployments.
N-able
Formerly SolarWinds MSP, it offers Cove Data Protection that reduces backup complexity and recovery uncertainty.
Why to watch – it provides an appliance-free direct-to-cloud backup solution.
Nasuni
It is a US company that has developed a cloud-native global file system, UniFS, which creates many new capabilities.
Why to watch – it delivers a file data services platform that leverages object storage delivering a simpler, lower cost, and more efficient SaaS solution that scales easily to handle rapid unstructured data growth.
OpenText (Carbonite)
It is a global organization with its corporate HQs in Waterloo ONT, Canada, and regional HQs in Munich, Germany, and Sydney, Australia. OpenText, The Information Company, enables organizations to gain insight through market leading information management solutions, powered by OpenText Cloud Editions.
Why to watch – Carbonite Server VM protection bundle combines the long-term protection of local and cloud backups with the speed of local failover for key systems in the event of an outage. Carbonite Cloud-to-Cloud Backup offers comprehensive, automatic backup and recovery for Microsoft 365, SharePoint, Google Workspace, Salesforce, Box and Dropbox.
Redstor
It is a UK company with customers around the world. It provides centralised management and on-demand access including cloud backup and recovery for servers, desktops, and laptops together with archiving and DR.
Why to watch – proprietary InstantDataä technology that enables rapid recovery of entire systems streaming what data is needed when it is needed.
Rewind Backups
It is based in Ottawa, ONT, Canada, and provides a cloud service that enables customers to backup data from a range of SaaS. The SaaS currently protected include Shopify, Jira, GitHub, BigCommerce, Confluence, QuickBooks Online, BitBucket, and Trello.
Why to watch – the increasing popularity and range of SaaS means that organizations will need a backup solution for these.
Rubrik
It is a multi-cloud data management company based in Palo Alto, CA, founded in December 2013. Its Cloud Data Management provides single platform to manage all data in the cloud, at the edge, or on-premises for backup, DR, archival, compliance, analytics, and copy data management.
Why to watch – It covers a range of physical servers, databases, and applications and IaaS workloads in Azure, AWS, GCP, and Oracle Cloud as well as Microsoft Office 365.
Zerto
Acquired by HPE in September 2021, it provides ransomware protection, DR, and data protection as a service for any app, any cloud, and any recovery SLA.
Why to watch – it offers a single, scalable platform for cloud data management and protection.













 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter

