Synology Security Advisory Revolved SA-22:16 ISC BIND
Concerning CVE-2022-2906/CVE-2022-3080, CVE-2022-38177, or CVE-2022-38178 vulnerabilities on DSM NAS OS
This is a Press Release edited by StorageNewsletter.com on September 30, 2022 at 2:00 pmSynology Inc. had published a security advisory concerning the revolved CVE-2022-2906/CVE-2022-3080, CVE-2022-38177, or CVE-2022-38178 vulnerabilities on DSM NAS OS.
Publish time: 2022-09-26 18:08:37 UTC+8
Last updated: 2022-09-26 18:08:37 UTC+8
Severity: Not affected
Status: Resolved
Abstract
None of Synology’s products are affected by CVE-2022-2906 as this vulnerability only affects ISC BIND 9.18.0 and later.
None of Synology’s products are affected by CVE-2022-3080, CVE-2022-38177, or CVE-2022-38178 as these vulnerabilities only affect when specific features are enabled.
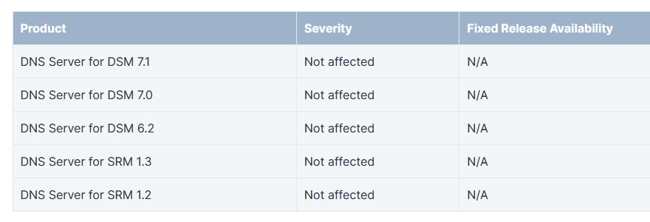
Affected products
Detail:
- CVE-2022-2906
- Severity: Not affected
- CVSS3 Base Score: 0.0
- CVSS3 Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:N
- An attacker can leverage this flaw to gradually erode available memory to the point where named crashes for lack of resources. Upon restart the attacker would have to begin again, but nevertheless there is the potential to deny service.
- CVE-2022-3080
- Severity: Not affected
- CVSS3 Base Score: 0.0
- CVSS3 Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:N
- By sending specific queries to the resolver, an attacker can cause named to crash.
- CVE-2022-38177
- Severity: Not affected
- CVSS3 Base Score: 0.0
- CVSS3 Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:N
- By spoofing the target resolver with responses that have a malformed ECDSA signature, an attacker can trigger a small memory leak. It is possible to gradually erode available memory to the point where named crashes for lack of resources.
- CVE-2022-38178
- Severity: Not affected
- CVSS3 Base Score: 0.0
- CVSS3 Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:N
- By spoofing the target resolver with responses that have a malformed EdDSA signature, an attacker can trigger a small memory leak. It is possible to gradually erode available memory to the point where named crashes for lack of resources.
References:
- ISC Releases Security Advisories for Multiple Versions of BIND 9
- CVE-2022-2906: Memory leaks in code handling Diffie-Hellman key exchange via TKEY RRs (OpenSSL 3.0.0+ only)
- CVE-2022-3080: BIND 9 resolvers configured to answer from stale cache with zero stale-answer-client-timeout may terminate unexpectedly
- CVE-2022-38177: Memory leak in ECDSA DNSSEC verification code
- CVE-2022-38178: Memory leaks in EdDSA DNSSEC verification code
- CVE-2022-2906
- CVE-2022-3080
- CVE-2022-38177
- CVE-2022-38178
Revision














 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter

