Enterprise Storage Security Significantly Lagging Behind Compute and Network Security
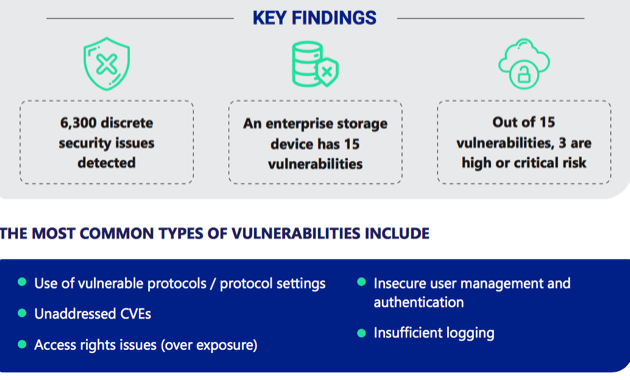
More than 400 enterprise storage devices detecting 6,300 discrete security issues
This is a Press Release edited by StorageNewsletter.com on October 14, 2021 at 1:32 pmContinuity Software, Inc. issued The State of Storage Security Report.
The first research to examine the security of storage systems, this report provides an analysis of the vulnerabilities and misconfigurations of enterprise storage systems. The findings revealed that storage systems have a significantly weaker security posture than the other 2 layers of IT infrastructure: compute or network.
These findings are alarming given the fact that, unlike an attack on individual endpoints or servers, which can cause problems, an attack that targets storage systems can be truly devastating. A compromise of a single storage array can bring down thousands of servers – and wipe out petabytes of data, a frightening prospect given the rise in ransomware attacks over the past three years that target corporate data.
For report, Continuity’s automated risk detection engines analyzed data from more than 400 enterprise storage devices from vendors including Brocade, Cisco, Dell EMC, IBM, Hitachi Data Systems, NetApp.
Key research findings include:
- More than 6,300 discrete security issues, such as vulnerabilities and misconfigurations, were detected;
- More than 170 security principles were not adequately followed;
- On average, enterprise storage devices had 15 security vulnerabilities. Approximately 3 of those were considered a high or critical risk rating – meaning they could present a significant compromise if exploited.
- The 5 most common types of vulnerabilities included: use of vulnerable protocols/protocol settings, unaddressed common vulnerabilities and exposures (CVEs), access rights issues (over exposure), insecure user management and authentication, and insufficient logging.
“Of the 3 main IT infrastructure categories – compute, network, and storage – the latter often holds the greatest value, from both security and business perspectives,” said Gil Hecht, founder and CEO. “Security vulnerabilities and misconfigurations of storage devices present a significant threat, especially as ransomware attacks have taken hold of businesses over the past few years. Yet based on our analysis, the security posture of most enterprise storage systems is strikingly weak. Organizations must act immediately to better protect their storage – as well as backup systems – to ensure their data is secure against ransomware and other cyberattacks.“
To help organizations gain the visibility they need to understand their storage vulnerability risk and avoid blind spots, Continuity recommends that they evaluate existing security processes and ensure that the storage layer be secured and hardened to a similar – if not greater – extent as compute and network assets.
Continuity’s StorageGuard is a solution that checks for thousands of possible misconfigurations and vulnerabilities at the storage system level that pose a security threat to organizations’ data.
Methodology
Continuity compiled anonymized inputs from more than 20 customer environments across North America and EMEA, covering the banking and financial services, transportation, healthcare, telecom and other industry sectors. A total of 423 enterprise storage devices were analyzed from vendors including Brocade, Cisco, Dell EMC, IBM, Hitachi Data Systems, NetApp. The analysis covered the configuration of block, object and IP storage systems, SAN/NAS, storage management servers, storage appliances, virtual SAN, storage network switches, data protection appliances, storage virtualization systems and other storage devices. Continuity’s automated risk detection engines checked for thousands of possible misconfigurations and vulnerabilities at the storage system level that posed a security threat, of which was tagged with a security index (1-5) and tracked so as to allow for detailed assessment, aggregation and drill down.
Resources
- NIST Guide for Storage Security – co-authored by Continuity
- Storage Security Handbook for an overview of the evolution of the storage technology landscape, and a set of practical recommendations on avoiding emerging threats.
- Blog for storage security insights and advice from company executives and experts.














 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter

