Druva Curated Recovery Technology for Accelerated Ransomware Recovery
Bounce back from ransomware attacks with automated recovery of clean, complete data sets, eliminating time intensive recovery efforts
This is a Press Release edited by StorageNewsletter.com on September 29, 2021 at 2:02 pmDruva Inc. introduced a Curated Recovery technology, leveraging intelligent automation, for accelerated ransomware recovery.
Adding to the company’s accelerated ransomware recovery module, Curated Recovery mitigates the impact of a ransomware attack, building an uncorrupted, unencrypted and malware-free recovery point to ensure a recovery before one is ever initiated. Combining this ransomware recovery module with Druva’s built-in security framework, businesses can now better protect critical data and recover faster with confidence.
Ransomware is one of the most popular methods used by hackers and malicious actors, and the average ransomware payment has surpassed $240,000 according to a new survey from IDC. Its lucrative nature has incentivized bad actors to expand the scope of their attacks, including the introduction of new variants designed specifically to encrypt or delete backup data, destroying organizations’ last line of defense and further incentivizing payment.
Traditional recovery from such an attack requires identifying a single point in time prior to the infection. However, because ransomware often enters a system months before it is detected, administrators are often forced to manually search for the most recent, unaffected versions of individual files or data sets. Now, by reviewing a comprehensive set of recovery points, the company’s Curated Recovery can help identify the latest clean version of each file through recent changes, replacing a weeks-long, resource-intensive process with a simplified recovery workflow. Using the firm’s intelligent automation platform, IT teams can find the most recent clean version of all their data and return operations to normal faster.
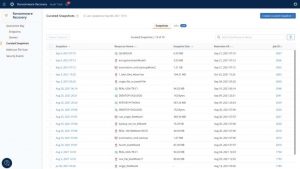
Ransonware Recovery snapshot list
Click to enlarge
“Being the victim of a ransomware attack doesn’t need to be a choice between paying an exorbitant ransom or halting operations while IT teams go through an intensive, manual recovery process,” said Jaspreet Singh, founder and CEO. “There’s no compelling reason to be held hostage by ineffective data protection technology. With our newest capabilities, every customer can gain the peace of mind of restoring their data with confidence.“
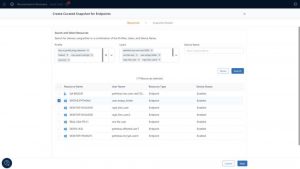
Resources for curated recovery endpoints
Click to enlarge
In addition to Accelerated Ransomware Recovery, the Druva Cloud Platform offers a built-in security framework and multi-layer approach which is designed to be resilient vs. ransomware. The platform’s zero trust architecture ensures only customers have access to their data, while features such as excess deletion prevention stops ransomware from permanently deleting backups.
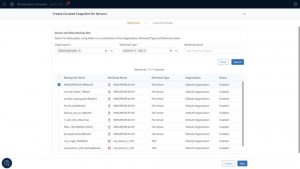
Selecting resources for curated recovery endpoints
Click to enlarge
Learn about Curated Recovery at the firm’s Cyber Resilience Virtual Summit on October 13, where attendees will have the opportunity to hear from leaders and peers about how organizations are fighting back vs. increasingly sophisticated cyberattacks. Attendees will leave with actionable information on emerging best practices that span data protection and recovery and how to integrate security and backup technologies.
From customers and partners on front lines of protecting organizational data:
Technologent is a ‘Global Edge-to-Edge IT Services’ company that delivers agile solutions for accelerating digital transformation.
“The threat of ransomware is not something we, or our customers can afford to ignore, thus we continue to evaluate technologies to ensure we have the best solutions to offer our clients,” said Juan Gomez, director, data management and protection, Technologent. “Data protection and security are converging, and in our evaluations, Druva’s architecture clearly sets it apart, and its ransomware recovery capabilities are outstanding. The Druva Curated Recovery is innovative, and we are eager to help our clients take advantage of this new capability.“
CDL Electric, founded in 1964, operates in the trades, railroad, and manufacturing sectors serving over 50,000 customers in over 40 states.
“Many years ago, we fell victim to a ransomware attack, which disrupted our operations, but more importantly served as a pivotal moment in the rethinking of our security and operations,” said Hugo Flores, director, IT and special projects, CDL Electric. “In that first instance, without any insights, we restored the data and also brought back the ransomware, forcing us to restart the whole process. At our current size, such an event would have a catastrophic impact on our organization. With technologies like Druva, with its ability to rapidly recover, we are confident we can minimize such disruptions and get back to business quickly.“
Build Group, Inc. is a San Francisco, CA-based general contracting company that takes on all aspects of construction from structural design and foundations to interiors and finish work.
“Ransomware can sit in systems undetected for weeks or months at a time, making it incredibly difficult to recover with clean, uninfected files,” said Adam Kailian, IT systems administrator, Build Group. “Druva Curated Recovery gives us the peace of mind that we have clean backups readily available if we ever need to restore from a ransomware attack. Combined with the fact that Druva can also help us quickly identify anomalies in our backups, brings a lot of value to our organization.“
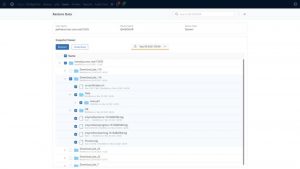
Restore data via Curated Recovery
Click to enlarge
About Accelerated Ransomware Recovery
The company‘s Accelerated Ransomware Recovery brings Druva Cloud Platform customers capabilities to reduce data loss via intelligent automation and orchestration, as well as integrations with security information and event management (SIEM) and security orchestration, automation and response (SOAR) tools:
-
Access insights: Understand location and identity for all access attempts to gain situational awareness
-
Anomaly detection: Gain data-level insights on file changes, creation, recovery, and deletion. Users can create alerts for anomalous activity and use anomaly information to identify the time frame of an attack
-
Quarantine: Quickly quarantine infected systems and snapshots
-
Recovery scans: Scan snapshots for known malware and customer-provided indicators of compromise before restoring to avoid reinfection
-
Curated snapshots: Automatically recover the most recent clean version of every file within a specified time frame, dramatically reducing recovery time
Resources:
Blog: Simplify your ransomware recovery with Curated Recovery from Druva
Infographic: About the state of ransomware and how Druva helps businesses recover with confidence
Register: Druva Cyber Resilience Summit 2021 (North America, EMEA, APAC) and view the session details and speaker biographies.













 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter
