Cross-Region and Cross-Account Backups for Amazon FSx Using AWS Backup
Customers can copy FSx backups to other AWS regions to meet cross-region business continuity goals or copy them across accounts to meet backup compliance needs.
This is a Press Release edited by StorageNewsletter.com on April 22, 2021 at 2:00 pmBy Adam Hunter, senior enterprise solutions architect, Amazon Web Services
![]() and Fathima Kamal, Sr. solutions architect, AWS, specializing in storage
and Fathima Kamal, Sr. solutions architect, AWS, specializing in storage
Cross-region and cross-account backups for Amazon FSx using AWS Backup
AWS Backup is announcing cross-region and cross-account backup (CRAB) support for Amazon FSx. It offers a cost-effective, fully managed, policy-based service that further simplifies data protection at scale. It also helps you support your regulatory compliance obligations and meets your business continuity goals. It makes it easy and cost-effective to run feature-rich and highly performant file systems. With this launch, storage and application administrators can copy backups across AWS Regions to implement cross-region business continuity. Administrators can now also copy backups across AWS accounts to protect their backups from accidental user activity, account compromises, and ransomware.
Organizations of all sizes are moving their file datasets to Amazon FSx to benefit from the agility, scalability, and cost-effectiveness of using fully managed file storage in AWS. FSx provides 2 file systems to choose from: Amazon FSx for Windows File Server, which provides shared file storage accessible over the industry-standard Server Message Block (SMB) protocol, and Amazon FSx for Lustre, which provides high-performance shared file storage for fast processing of compute workloads. It enables customers to create secure, highly durable backups of their file systems. However, before today’s launch, these backups could only reside in the same AWS Region and account as those of the file system.
Customers can now copy Amazon FSx backups to other AWS Regions to meet their cross-region business continuity goals or copy them across accounts to meet their backup compliance needs. These features enable customers to recover data in the event of accidental or malicious user activity, thus preventing the loss of backups or encryption keys in their primary account. They also remove the undifferentiated heavy lifting of managing backups across applications, allowing organizations to more easily meet their compliance requirements. Organizations can now easily access and share data for quality assurance and testing, without running any risk of affecting production data.
Customers can create an automatic backup plan with just a few clicks in the AWS Backup console to periodically create and copy backups of their Amazon FSx file systems, along with backups of other AWS resources, to additional AWS Regions or accounts.
In this blog, we demonstrate creating an AWS Backup plan that automatically performs a cross-account backup (CRAB) copy. First, we discuss the prerequisites needed to deploy both solutions. Next, we demonstrate how to configure a backup plan. Finally, we review how to test your backup plan by restoring a file system.
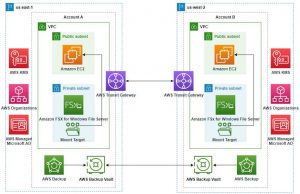
Architecture: Cross-region and cross-account backup (CRAB)
The following diagram shows the key components involved in deploying CRAB support for Amazon FSx. The architecture includes an Amazon EC2 instance attached to a FSx for Windows File Server backed up by AWS Backup. To implement CRAB, we copy the backup from the source account to a second backup vault in the destination account. In this example, we are using Transit Gateway for connectivity between regions, but you can also use VPC peering. After doing the aforementioned copying, we can then restore our FSx for Windows File Server in the destination account.
Click to enlarge
Prerequisites
The following prerequisites are required before enabling CRAB support for Amazon FSx for Windows File Server.
-
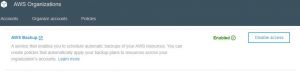
You need 2 accounts that belong to the same organization, as defined in AWS Organizations. For more information, see the documentation on creating and configuring an organization.
-
From the AWS Organizations console, select settings and ensure that you have AWS Backup enabled.
Click to enlarge
-
Set up an Amazon FSx for Windows File Server file system. For more information, visit the documentation on getting started with FSx. FSx provides you with 2 options for integrating your Amazon FSx for Windows File Server file system with Active Directory. You can use Amazon FSx with AWS Directory Service for Microsoft Active Directory or use Amazon FSx with your self-managed Microsoft Active Directory.
Set up cross-region and cross account (CRAB) copy
Here are the instructions to enable CRAB for FSx for Windows File Server using AWS Backup.
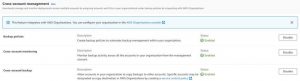
Step 1: Enable cross-account in the management account
Log in to the AWS Management Console of the source account in the us-east-1 (N. Virginia) Region and select AWS Backup. In the AWS Backup console, in the source account, select Settings and under Cross-account management, ensure that you have enabled Backup policies, Cross-account monitoring, and Cross-account backup.
Click to enlarge
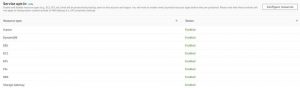
Step 2: Service opt-in for Amazon FSx
From the same page, under Service opt-in, ensure that you have enabled FSx. If is not enabled, you can enable it by selecting Configure resources.
Click to enlarge
Step 3: Create a vault in the destination account/Region
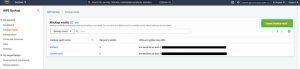
Log in to the AWS Management Console of the destination account in the us-west-2 (Oregon) Region and select AWS Backup. In the AWS Backup console, select Backup vaults, and then click Create Backup vault.
Click to enlarge
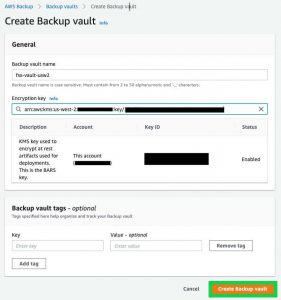
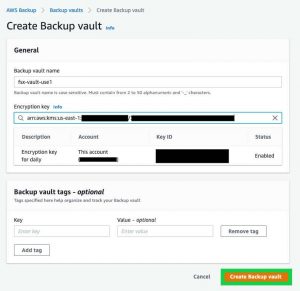
Use an easily identifiable name for the Backup vault name. For encryption, select the customer managed customer master keys (CMK) you created as part of the prerequisites, or an existing customer managed CMK. You can refer to this guide for creation of CMKs in the AWS Key Management Service (AWS KMS) console.
Click to enlarge
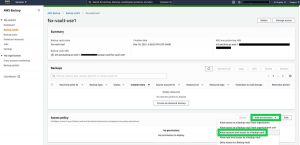
Once you’ve created the vault, make note of the Backup Vault ARN. In the Access Policy section, you can select Add permissions and select the access based on the security needs. For this solution, we select Allow account level access to a Backup vault.
Click to enlarge
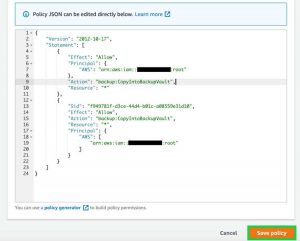
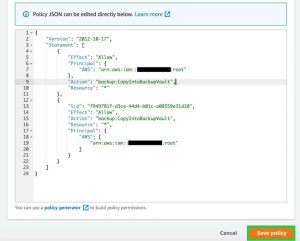
You can allow access to a backup vault from an organization, organizational unit, and account. You can also specify deny statements to deny users from accessing the vault or the resources in the backup vault. After selecting Allow account level access to a Backup vault, provide the source account number in the JSON statement. Select Save policy.
Click to enlarge
The destination vault is now ready to receive backups from the source account.
Step 4: Create a source vault in the source account/source Region
Log in to the AWS Management Console of the source account in the us-east-1 (N. Virginia) Region and select AWS Backup. In the AWS Backup console, select Backup vaults, and then click Create Backup vault.
Click to enlarge
Use an easily identifiable name for the Backup vault name. For encryption, select the customer managed customer master keys (CMK) you created as part of the prerequisites, or an existing customer managed CMK. Click Create Backup Vault.
Click to enlarge
Once you have created a vault, select Add permissions in the Access Policy section and select Allow account level access to a Backup vault.
Click to enlarge
Add in the destination account number in the JSON policy statement. This is to ensure that you can copy back the backups from the destination account back to the source account. Select Save policy.
Click to enlarge
You can automate CRAB by creating an automated backup plan via the AWS Backup console, API, or the CLI.
Step 5: Create backup plan in the source account
In the AWS Backup console, select Backup plans, and select Create Backup plan.
Click to enlarge
-
You can start from an existing plan, build a new plan from scratch, or define a plan using JSON.
-
Select Build a new plan. In the Backup plan section, provide a name for the backup plan.
-
Backup plan name: fsx-cab-backup
-
-
Click to enlarge
-
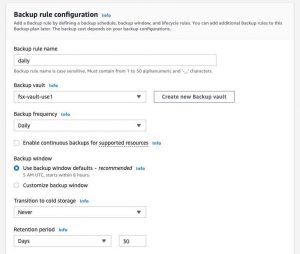
In the Backup rule configuration section, enter the following information.
-
Backup rule name: daily
-
Backup vault: fsx-vault-use1
-
Backup frequency: Daily
-
-
In the Backup window section, select backup window defaults, which initiates the backup job at 5 AM UTC (Coordinated Universal Time) and lasts 8 hours. If you would like to customize the backup frequency, refer to the documentation for more information. Keep the default for Transition to cold storage. In the Retention period section, select Days and type 30 or you can put in any number.
Click to enlarge
-
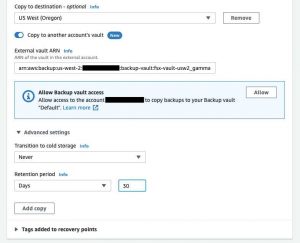
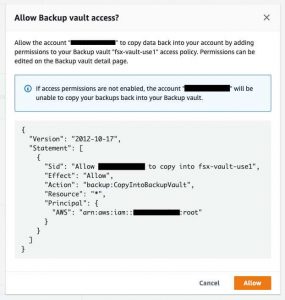
For Copy to destination, select US West (Oregon). Enable the Copy to another account’s vault and provide the External vault ARN noted in step 3. In the Advanced settings, keep the default for Transition to cold storage. In the Retention period section, select Days and enter “30” – or any number of days you desire.
Click to enlarge
Select Allow, allowing for backup vault access in the destination account.
Click to enlarge
-
In the Advanced backup settings, select the default option. Select Create plan. The daily rule applies to the backup plan upon creation.
Click to enlarge
6. Select Assign resources to assign resources.
Click to enlarge
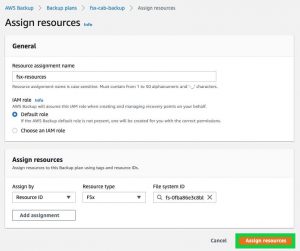
7. In the Assign resources section, provide the following. Then, select Assign resources.
-
-
Resource assignment name: fsx-resources
-
IAM role: select the default role. If you choose a role other than Default role, make sure that it has the necessary permissions to back up the Amazon FSx resources.
-
Assign resources: Select Resource ID for Assign by, FSx for Resource Type, and select the File system ID.
-
You can assign resources by Tags or Resource ID. Tags are a more simple and scalable way to back up multiple resources.
-
-
Click to enlarge
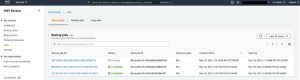
The automated backup plan is now complete. The plan runs based on the schedule defined in its rules. You can browse to Jobs in the AWS Backup console and check the backup job to get a status of the backup job. You can also use Amazon CloudWatch integration for notifications on the backup job completion.
Click to enlarge
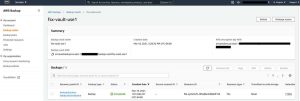
Once the backups are completed, select Backup vaults, and select the source backup vault: fsx-vault-use1.
Click to enlarge
The recovery point will appear under the backups section.
Click to enlarge
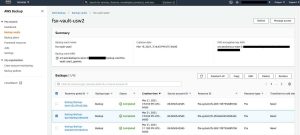
Step 6: Restoring the Amazon FSx for Windows File Server file system in the destination account
Log in to the AWS Management Console of the destination account in the us-west-2 (Oregon) Region and select AWS Backup. In the AWS Backup console, select Backup vaults, and select the destination vault – fs-vault-usw2 – created for cross-account backups.
The recovery points will start to appear in the destination vault and it shows the Source account ID that you copied the backup from. Select the latest recovery point and select Restore.
Click to enlarge
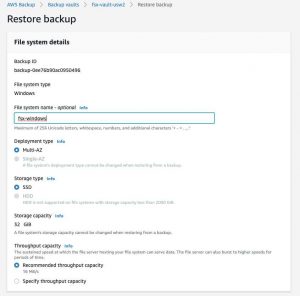
You can use a backup’s recovery point to create a new file system and restore a snapshot of another file system. When restoring Amazon FSx file systems, AWS Backup creates a new file system and populates it with the data.
-
In the file system details, you can see the ID of the backup under Backup ID, and the file system type under File system type.
-
Enter the name of the file system.
-
Choose a Deployment type and accept the default. You cannot change the deployment type of a file system during restore.
-
Choose the Storage type and accept the default. You cannot change the deployment type of a file system during restore.
-
Choose Recommended throughput capacity to use the recommended 16 MB/s, or choose Specify throughput capacity and enter a new rate.
-
Click to enlarge
-
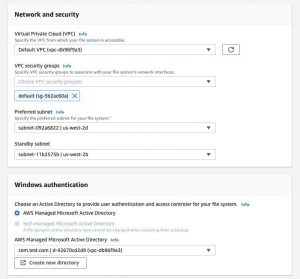
In the Network and security section, provide the Virtual Private Cloud (VPC), VPC security groups, Preferred subnet, and the Standby subnet.
-
When restoring an Amazon FSx for Windows File Server file system, it is necessary to provide the Windows authentication information used to access the file system. You also have the option of creating a new directory. You cannot change the type of Active Directory on the file system during the restore of a backup.
Click to enlarge
-
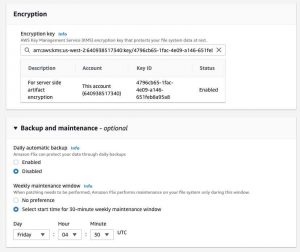
In the Encryption section, you can now choose the encryption keys that you want to use for the new Amazon FSx file system.
-
For Backup and maintenance, provide the information to set your backup preferences.
You can restore backups created by AWS Backup using the AWS Backup console, API, or AWS CLI.
Click to enlarge
-
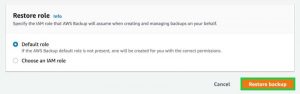
In the Restore role section, choose the default IAM role that AWS Backup will use to create and manage the backups.
-
Click Restore backup. This will perform a restore of the backup that was copied from the source account to the destination account.
Click to enlarge
Step 7: Copy the backup from the destination account to the source account
Log in to the AWS Management Console of the destination account in the us-west-2 (Oregon) Region and select AWS Backup. In the AWS Backup console, select Backup vaults, and select the destination vault – fs-vault-usw2 created for cross-account backups.
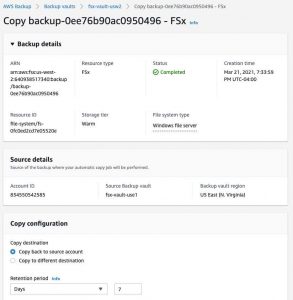
The recovery points will start to appear in the vault, and they will also show the Source account ID that the backup was copied from. Select the latest recovery point and select Copy.
Click to enlarge
In the Copy configuration section, choose Copy back to source account to copy the backups back to the source account. If you like to copy to a different destination, select copy to different destination and paste in the external vault ARN of the vault. Type in the number of days you would like to retain the backups for in the Retention period.
Click to enlarge
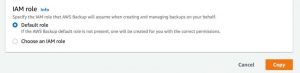
Select Choose an IAM role and choose the IAM role that has access to the resources and has a trusted relationship between the accounts to perform the cross-account copy. You can also choose to use the Default role.
Click to enlarge
Select Copy. This operation will copy the backups to the source account.
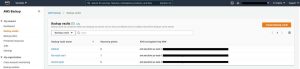
Cleaning up
To avoid incurring any future charges, follow these steps to remove resources you may have created:
-
Log in to the source account and delete the backup plans and the recovery points in the source vault by following this guide.
-
Log in to the destination account and delete the backup plans and the recovery points in the source vault by following this guide.
Conclusion
In this blog post, we detailed the steps needed to set up an automated backup plan to enable cross-region and cross-account backups (CRAB) of FSx file systems from a source account in us-east-1 to a destination account in us-west-2. Then, we validated the backups in the destination account by performing a restore of the FSx for Windows File Server file system in the destination account. Finally, we performed a cross-account copy of the recovery points in the destination account back to the source account.
Using the new features described in this post, you can now leverage AWS Backup to create a multi-region, multi-account data backup strategy for your FSx file systems. AWS Backup offers a cost-effective, fully managed, policy-based service that further simplifies data protection at scale. Having a cross-account backup strategy enables you to securely copy backups across accounts within AWS Organizations. Cross-account backup copies provide an additional layer of protection from accidental or malicious deletion and ransomware protection.













 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter

