Key Management. As a Service. For Real.
DCIG reporting to StorMagic's introduction of key management-as-a-service
This is a Press Release edited by StorageNewsletter.com on July 31, 2020 at 2:26 pm This report was written on July 23, 2020 by Jerome M. Wendt, president and founder of DCIG, Inc., an independent storage analyst and consulting firm.
This report was written on July 23, 2020 by Jerome M. Wendt, president and founder of DCIG, Inc., an independent storage analyst and consulting firm.
Key Management. As a Service. For Real.
Ask anyone who works for any size enterprise if he or she thinks encrypting vulnerable data is a good idea. You will get an almost universal “Yes” answer. Then ask that same individual if their enterprise encrypts its most vulnerable data. That individual will most likely respond with a mumbled “No.” Few enterprises encrypt their vulnerable data simply because it is too hard to manage the encryption keys. That response may start to change thanks to StorMagic’s recent introduction of key management as a service (SvKMS).
Encryption Easy … Key Management Hard
On one hand, it seems almost ludicrous that enterprises worry about their vulnerable data being read should one access it. After all, almost every application, device, and OS offer some means to secure and encrypt the data they manage. Turn their encryption feature “On” and the data becomes inaccessible and unreadable to almost anyone not working for the NSA.
Unfortunately, encryption remains in its default “Off” position for one very simple reason. Few enterprises, if any, want to manage the keys that encrypt and decrypt data.
Attempting to do key management manually almost constitutes a cruel joke. Tracking which encryption keys encrypt and decrypt which data at which specific dates and times creates a labyrinth to navigate. If anything, it may only result in the enterprise becoming unable to access its own data. They find it better to do nothing than dealing with that nightmare scenario.
Even in cases where enterprises do have key management software in place, they typically restrict its use for multiple reasons. One must install and manage the key management software. It remains costly to obtain and complex to implement. It only manages and provides key management services for specific applications. Unless compelling reasons exist (national secrets, regulatory requirements, etc.,) to implement it, sensitive data remains unencrypted.
Times, They Are a Changing
One would think that with key management being so difficult, enterprises would demand a simpler solution. However, enterprises still largely still store most of their data inside of data centers that resemble bunkers. One can understand why they care less about encrypting data in these environments.
However, change the environment. Put that same data in a grocer, a convenience store, a bank branch, or a truck stop. Further, place it in a location and on a server hardware platform that someone can easily move. Then add a nefarious element to the equation. Introduce an individual who looks both ways, reaches over the counter, picks it up, and walks out the front door.
Ten years ago, maybe even 5 years ago, this latter environment rarely existed. Today, this environment exists everywhere. As more enterprises move compute and storage to these edge locations, they now store valuable data there as well.
Unencrypted data stored in these environments becomes a tempting target for knowledgeable, sophisticated thieves or perhaps even competitors. Once they have the hardware, they have all day to figure out the value of its data. Unencrypted data makes it a much more appealing target.
Time for Key Management as a Service Has Come
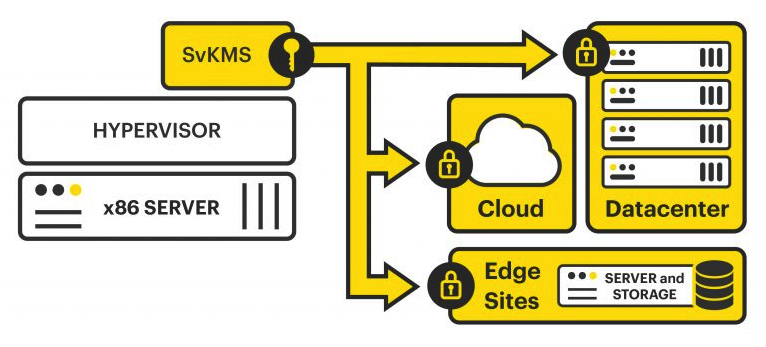
This new edge computing environment demands the similar introduction of a key management solution designed to address it. StorMagic’s Key Management as a Service (which is based on its SvKMS solution – but now hosted in the StorMagic Cloud) represents one of the first solutions, if not the only solution, that addresses this new enterprise need.
Using this cloud-based service, enterprises may obtain their encryption keys from a SaaS provider. Like other cloud-based SaaS offerings, the cloud provider (StorMagic in this case) handles all the undesirable tasks associated with key management. It maintains the underlying hardware and software. It performs the ongoing software fixes, patches, and updates.
By StorMagic performing those tasks, enterprises can focus on what they really want to run their business: encryption key management. Like other SaaS offerings, they only need to sign up to access the service. Once logged in, they identify the keys they need and the applications, devices, or systems that need them. Then they can start encrypting data.
It’s Really that Easy
Granted, some other setup details to get SvKMS up and going exist but the premise remains the same. StorMagic has made key management accessible and available for anyone who cares to encrypt their vulnerable data. Further, it makes sense that it would come from a provider who specializes in delivering solutions to remote and edge offices.
It sees the challenges described above in its customers’ environments every day. Hence, it made sense that it would take the initiative and look to provide a solution to address them.
Perhaps more impressively, StorMagic opened the gates wide for the availability of this solution. StorMagic could have limited its SvKMS offering to only work with its SvSAN solution. It did not. Any workload running in any environment – cloud, hybrid, or on-premises – can use the SvKMS solution.
This is cool stuff. But more importantly, SvKMS provides an answer to a long-standing and unresolved key management issue. Check it out at this link on StorMagic’s website.













 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter

