F-Secure Unveils USB Armory Mk II Computer on USB Stick With Security Features
For applications such as custom hardware security modules, cryptocurrency wallets, secure authentication, and licensing tokens
This is a Press Release edited by StorageNewsletter.com on February 14, 2020 at 2:03 pmF-Secure Corp., at its foundry, have created a version of the USB Armory – a computer on a USB stick built from the ground up to be secure.
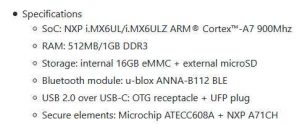
The USB armory Mk II entrenches security in its lowest levels and is suitable for a range of applications – such as custom hardware security modules, cryptocurrency wallets, secure authentication and licensing tokens, and more – that need the efficiency and flexibility of an embedded computer without sacrificing security.
The team at the firm’s foundry designed the device in response to security problems encountered when hardware begins to overlap with firmware. As a result, the device represents state-of-the-art orchestration between software, firmware and hardware, while offering security features and high computational power in the smallest of form factors.
“We routinely provide our customers with security reviews and security engineering services, which makes us both breakers and makers of technology. This gives us the ability to provide state-of-the-art security in our consulting practice. The USB Armory’s hardware and software implementation clearly demonstrates this,” says Andrea Barisani, head, hardware security, F-Secure. “Our continuous research into systems and methods to advance the state of embedded computing security has driven the development of the USB Armory, which in turn allows us to build all kinds of secure systems for our customers.“
The USB Armory Mk II’s security features include internal and external cryptographic coprocessors, a random number generator, secure boot capabilities, and more. These features harden the device vs. a variety of attacks, including physical tampering techniques that can compromise low-level processes like boot protocols. It’s the extra attention paid to these security issues that make the USB Armory suitable for processing information critical to the integrity of a system.
“The USB Armory’s emphasis on using hardware and software to protect data critical to a system’s foundation, such as authentication keys for boot processes, is why it’s ideal for use as a cryptocurrency wallet, storage unit, hardware security module, or other application where security and system integrity are the most important considerations,” says Barisani. “We’re seeing more embedded computers with unpatchable, exploitable hardware issues. I feel very strongly that the capabilities the USB armory gives companies address a very real, and potentially very serious, security problem.“
Furthermore, he says the USB Armory’s open source ecosystem ensures that the platform can evolve and grow to support an ever-expanding range of uses, and cites his recently announced TamaGo project as an example of how the platform is evolving.
“Our new TamaGo project enables the USB Armory, and in the future more platforms, to run bare metal applications written entirely in Go, therefore without the burden of an underlying OS. We’re hoping this supports the creation of pure Go firmware for all kinds of system-on-chips, dramatically reducing the attack surface and eliminating the need for any C code,” Barisani explains.
The USB Armory Mk II is available for order.
F-Secure Foundry is a part of F-Secure Consulting, which provides cyber security services tailored to fit the needs of banking, financial services, aviation, shipping, retail, insurance, and other organizations working in highly targeted sectors.














 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter
