Jetico BestCrypt Volume Encryption Enterprise Edition V4.0 Software
Delivers control over authentication for encryption with Single Sign-On and encrypted computers with Trusted Platform Module.
This is a Press Release edited by StorageNewsletter.com on March 12, 2019 at 2:41 pmJetico, Inc. Oy announced version 4 of BestCrypt Volume Encryption – Enterprise Edition.
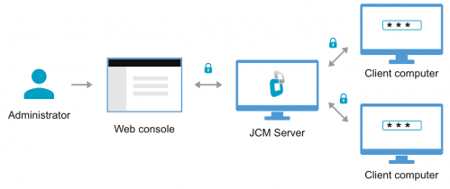
The updated central management component of the company’s disk encryption delivers control over authentication for encryption with Single Sign-On (SSO) and encrypted computers with Trusted Platform Module (TPM).
“With growing risks of data breaches and regulation enforcement, such as HIPAA and GDPR, encryption is the foundation of any information security policy or compliance program. Organizations of all sizes must deploy data encryption,” says Michael Waksman, CEO, Jetico. “BestCrypt enables Admins to remotely manage disk encryption software with speed, convenience and better authentication controls.“
Administrators can remotely allow SSO on encrypted computers, so end users automatically log in to Windows after entering their pre-boot encryption password. Encryption with SSO is more transparent, removing the need to remember an additional password.
TPM provides secure tamper-proof storage of encryption keys, particularly for when computers require rebooting. This allows for unattended restart for update rollout and maintenance. In addition to remotely enabling the use of TPM, BestCrypt administrators can set the exact time interval and number of times an unattended reboot is allowed for selected workstations or a group of computers.
Using a web browser, administrators can also enforce password strength settings to ensure all computers in an assigned group are protected with encryption passwords according to organizational standards. Admins can then require end users to change their passwords according to a set validity period.
For more customization, boot-time password prompt themes can be modified from the admin’s own central management console for any remote computers protected with BestCrypt Volume Encryption. For example, a custom theme can make the pre-boot password prompt look like a system error message to hide the presence of encryption on the computer. Or set all encrypted computers at boot time to display company helpdesk contact information.
Michael Waksman adds: “When you need encryption in a hurry, the encryption policies in BestCrypt now offer the option to encrypt only used space.”
Admins can encrypt computers in less time by skipping the free unused areas on the HDD.
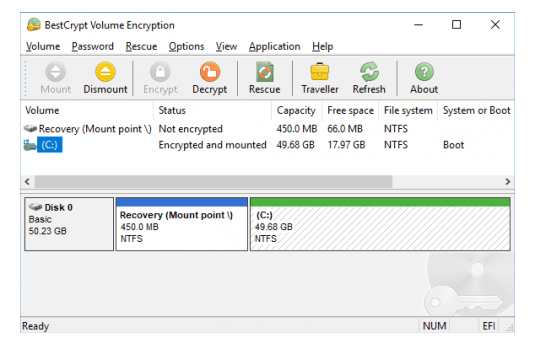
For over twenty years, the company serves enterprise customers with BestCrypt data encryption software, a reliable alternative to native OS encryption. On both fixed and removable storage, data on lost computer hardware is safe with BestCrypt.












 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter
