CyberYozh: Panic Button Software Emergency Erasure of Digital Data on Windows
To protect confidential information from unauthorized access or forensic analysis
This is a Press Release edited by StorageNewsletter.com on December 21, 2018 at 2:05 pmCyberYozh security group announces the Panic Button, a solution for emergency erasure of digital data on Windows computers.
Any unauthorized attempt to penetrate a user’s computer (be that a colleague who has secretly gained access to it, or law enforcement officers using data extraction tools) will trigger immediate and permanent data erasure.
Panic Button is designed to protect their confidential information from unauthorized access or forensic analysis. This includes journalists, businessmen, officials and politicians, as well as common users who wish to protect themselves against cybercriminals.
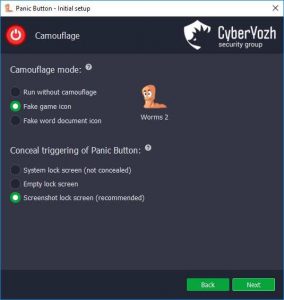
Click to enlarge
The data erasure application can be activated either by user (by clicking on a shortcut or pressing a user-defined key combination) or automatically, as a logic bomb.
During the program’s setup the user specifies a certain action that must be performed to prevent data erasure. Failing to perform this action will trigger the logic bomb and permanently erase the confidential information. The logic bomb will therefore go off at the attempt of stealthy penetration or forced data access.
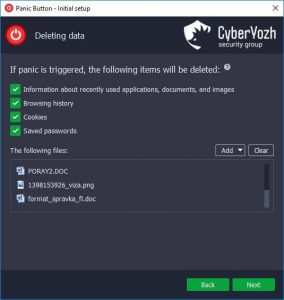
Panic Button erases user activity data in the system: the information about recently viewed documents or images and recently launched programs. It also erases Internet activity logs: web browser’s history, cookies, cache, bookmarks, and saved passwords. It supports browser Chrome, Mozilla, Opera, and Edge.
Click to enlarge
Panic Button permanently deletes any files a user specifies in their program’s settings. The user can also set up email notifications about activation of Panic Button (an optional feature).
Panic Button at a glance:
-
Permanently deletes all information about user activity in the system and on the Internet;
-
Erases all files chosen in the program’s settings;
-
Automatically goes off at the attempt of unauthorized access
-
Activates at the attempt of stealthy penetration














 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter

