Immutable Storage for Microsoft Azure Storage Blobs in Public Preview
Available in all Azure public regions
This is a Press Release edited by StorageNewsletter.com on June 26, 2018 at 2:27 pm![]() This article was posted June 19, 2018 on a blog of Microsoft Corp., written by Mitra Sinha, principal PM, Azure Storage.
This article was posted June 19, 2018 on a blog of Microsoft Corp., written by Mitra Sinha, principal PM, Azure Storage.
Immutable storage for Azure Storage Blobs now in public preview
Financial Services organizations regulated by SEC, CFTC, FINRA, IIROC, FCA, etc. are required to retain business-related communication in a WORM or immutable state that makes it non-erasable and non-modifiable for a certain retention interval.
The immutable storage requirement is not limited to financial organizations, but also applies to industries such as healthcare, insurance, media, public safety, and legal services.
Today, we are excited to announce the public preview of immutable storage for Azure Storage Blobs to address this requirement. The feature is available in all Azure public regions. Through configurable policies, users can keep Azure Blob storage data in an immutable state where Blobs can be created and read, but not modified or deleted.
Typical applications include:
• Regulatory compliance: Immutable storage for Azure Blobs is designed to help financial institutions and related industries address SEC 17a-4(f), CFTC 1.31©-(d), FINRA etc. A technical whitepaper with details on how the feature addresses these regulatory requirements will be available soon. The Azure Trust Center contains detailed information about our compliance certifications.
• Secure document retention: Users receive maximum data protection as the immutable storage feature for Azure Blobs service ensures that data cannot be modified or deleted by any user including those with account administrative privileges.
• Legal hold: Immutable storage for Azure Storage Blobs enables users to store sensitive information critical to a litigation, criminal investigation, and more in a tamper-proof state for the desired duration.
Immutable storage for Azure Storage Blobs enables:
• Time-based retention policy support: Users set policies to store data immutably for a specified interval of time.
• Legal hold policy support: When the retention interval is not known, users can set legal holds to store data immutably until the legal hold is cleared.
• Support for all Blob tiers: WORM policies are independent of the Azure Blob Storage tier and will apply to all the tiers, hot, cool and archive. This allows customers to store the data in the most cost optimized tier for their workloads while maintaining the data immutability.
• Blob Container level configuration: immutable storage for Azure Storage Blobs allows users to configure time-based retention policies and legal hold tags at the container level. Users can create time-based retention policies, lock policies, extend retention intervals, set legal holds, clear legal holds etc. through simple container level settings. The policies apply to all the Blobs in the container, both existing and new Blobs.
Immutable data is priced in the same way as mutable data and there is no additional charge for using this feature. Please refer to the Azure Storage Pricing page for the related pricing details.
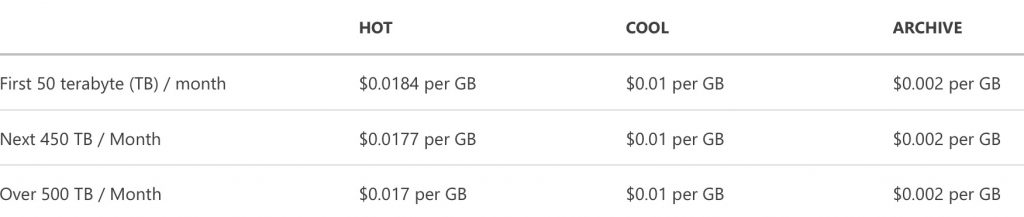
Data storage prices
All prices per gigabyte per month
Click to enlarge
How to get started
To use this feature, you must create a GPv2 account through the Azure Resource Manager. For more details on how to enable this feature, please refer to the immutable storage for Azure Storage Blobs documentation.
Immutable Storage for Azure Storage Blobs is supported on the most recent releases of Azure Portal, CLI 2.0, PowerShell (version 4.4.0-preview), .net Client Library (version 7.2.0-preview), node.js Client Library (version 4.0.0), and Python Client Library (version 2.0.0 Release Candidate 2).
You can also directly use the Storage Services REST API. This feature is supported on Blob Service REST API version 2017-11-09 and greater and on Azure Storage Resource Provider REST API version 2018-02-01 and greater. In general, we always recommend using the latest versions regardless of whether you are using the feature or not.













 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter

