Exercise Caution Before Making Any Assumptions About Cloud Data Protection Products
By Jerome Wendt, president, DCIG
This is a Press Release edited by StorageNewsletter.com on August 7, 2017 at 2:11 pm This article was written by Jerome M. Wendt, president and lead analyst of DCIG, Inc. on July 24, 2017.
This article was written by Jerome M. Wendt, president and lead analyst of DCIG, Inc. on July 24, 2017.
Exercise Caution Before Making Any Assumptions about Cloud Data Protection Products
There are two assumptions that IT professionals need to exercise caution before making when evaluating cloud data protection products. One is to assume all products share some feature or features in common. The other is to assume that one product possesses some feature or characteristic that no other product on the market offers. As DCIG reviews its recent research into the cloud data protection products, one cannot make either one of these assumptions, even on features such as deduplication, encryption, and replication that one might expect to be universally adopted by these products in comparable ways.
The feature that best illustrates this point is deduplication. One would almost surely think that after the emphasis put on deduplication over the past decade, every product would now support deduplication. That conclusion would be true. But how each product implements deduplication can vary greatly.
For example:
- 1 Block-level deduplication is still not universally adopted by all products. A few products still only deduplicate at the file level.
- 2 In-line deduplication is also not universally available on all products. Further, post-process deduplication is becoming more readily available as organizations want to do more with their copies of data after they back it up.
- 3 Only about 2 in 5 products offer the flexibility to recognize data in backup streams and apply the most appropriate deduplication algorithm.
![]()
(Source: DCIG, 175 products)
Deduplication is not the only feature that differs between these products. As organizations look to centralize data protection in their infrastructure and then keep a copy of data offsite with cloud providers, features such as encryption and replication have taken on greater importance in these products and more readily available than ever before. However, here again one cannot assume that all cloud data protection products support each of these features.
On the replication side, DCIG found that this feature to be universally supported across the products it evaluated. Further, these products all implement the option where organizations can schedule replication to occur at certain times (every five minutes, on the hour, etc.).
However, when organizations get beyond this baseline level of replication, differences again immediate appear. For instance, just over 75% of the products perform continuous data replication (replicate data immediately after the write occurs at the primary site) while less than 20% support synchronous replication.
Organizations all need to pay attention to the fan-in and fan-out options that these products provide. While all support 1:1 replication configurations, only 75% of the products support fan-in replication (N:1) and only 71% support fan-out replication (1:N). The number of products that support replication across multiple hops drops even further – down to less than 40%.
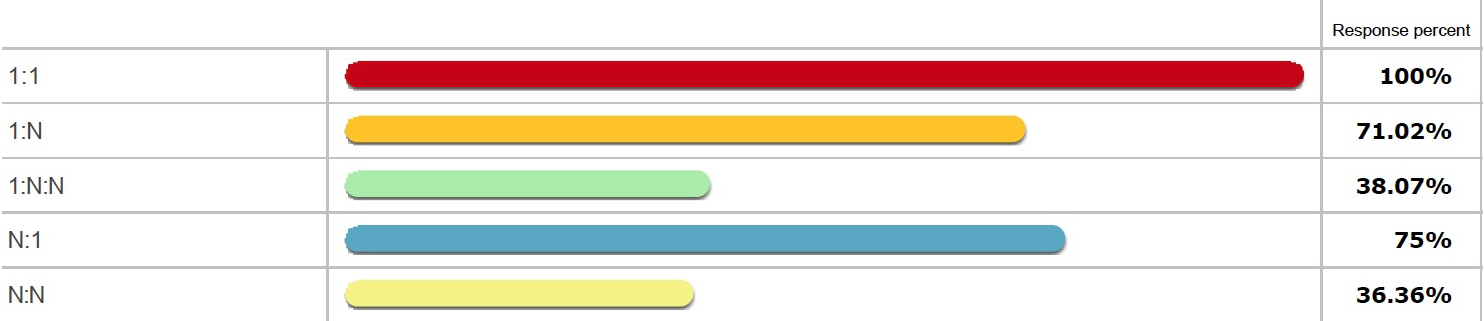
(Source: DCIG, 175 products)
Encryption is another feature that has become widely used in recent years as organizations have sought to centralize backup storage in their data centers as well as store data with cloud providers. In support of these initiatives, over 95% of the products support AES-256 bit encryption for data at-rest while nearly 80% of them support this level of encryption for data in-flight.
Deduplication, encryption, and replication are features that organizations of almost any size almost universally expect to find on any cloud data protection product that they are considering for their environment. Further, as DCIG’s research into these products reveals, they nearly all support these features in some capacity. However, they certainly do not give organizations the same number of options to deploy and leverage them and it is these differences in the breadth of feature functionality that each product offers that organizations need to be keenly aware of as they make their buying decisions.












 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter
