ExtraHop Empowers Enterprises to Recover Ransomware-Encrypted Files Without Backup
Ransomware offering combining security analytics with Precision Packet Capture to automatically detect and restore files
This is a Press Release edited by StorageNewsletter.com on November 11, 2016 at 2:44 pmExtraHop Networks, Inc. introduced a version of its ransomware mitigation offering that allows enterprises to recover ransomware-encrypted files without a backup.
The ransomware offering incorporates the company’s platform’s proprietary Precision Packet Capture capability, allowing companies to detect ransomware attacks in-progress and recover lost files in minutes, creating an end-to-end solution that puts control back in the hands of the enterprise. View a demo of how to use packet-capture to recover ransomware-encrypted files.
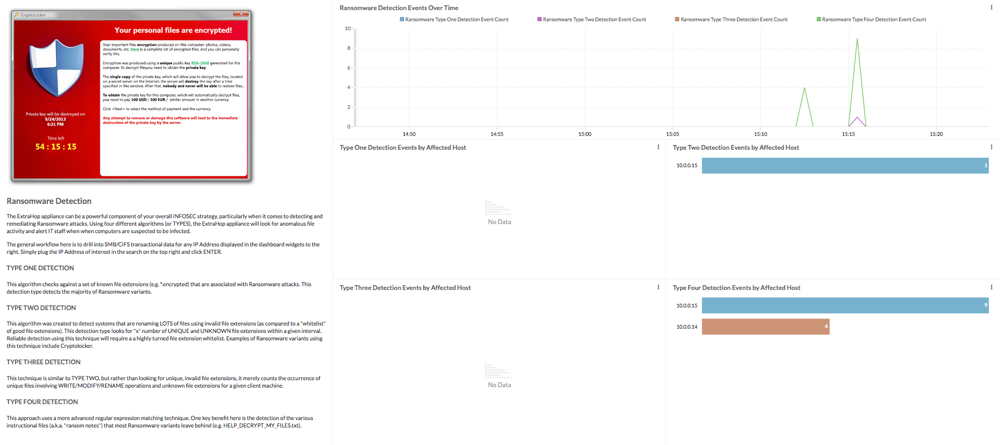
Click to enlarge
In a June 2016 report titled Use These Five Backup and Recovery Best Practices to Protect Against Ransomware, Robert Rhame and Roberta J. Witty, analysts, Gartner, warn: “Users are only a click away from a drive-by download of malware from a compromised web page, or a postlunch launch of a trojan attachment from a ransomware spam campaign. The rapid-release nature of the malware underground means that antivirus vendors are playing a game of catch-up.“
This ransomware solution from the company solves a vexing problem that large companies face on a daily basis. Ransomware attacks are one of the fastest-growing threats facing companies today-as more than 4,000 ransomware attacks are occurring daily in 2016, representing a 300% increase over the previous year. In the first quarter of 2016, ransomware netted cyber criminals hundreds of millions of dollars. Enterprises face the direct monetary ransom and loss of sensitive data and intellectual property These attacks can hinder business operations, productivity, and customer trust.
As evidenced by the growing number and severity of ransomware attacks, traditional security measures have fallen short against this threat. With the firm’s solution, customers can use packets to reconstruct files as they existed immediately before encryption, safely recovering critical data without paying ransom. This solution works even if customers do not have a recent backup of the affected files.
“The ‘human vector’ has become a reality for today’s security teams. Just as the common cold will infect at least one person in an office and make its way to others, you can be assured that at least one person in your organization will open an email attachment containing ransomware,” said John Smith, architect, principal solutions, security, ExtraHop. “We’ve already worked with customers around the globe to detect ransomware before it can do significant damage. By incorporating Precision Packet Capture into our ransomware solution, ExtraHop now truly puts IT security back in control, helping them detect and short-circuit attacks and rapidly restore impacted files.“
Click to enlarge
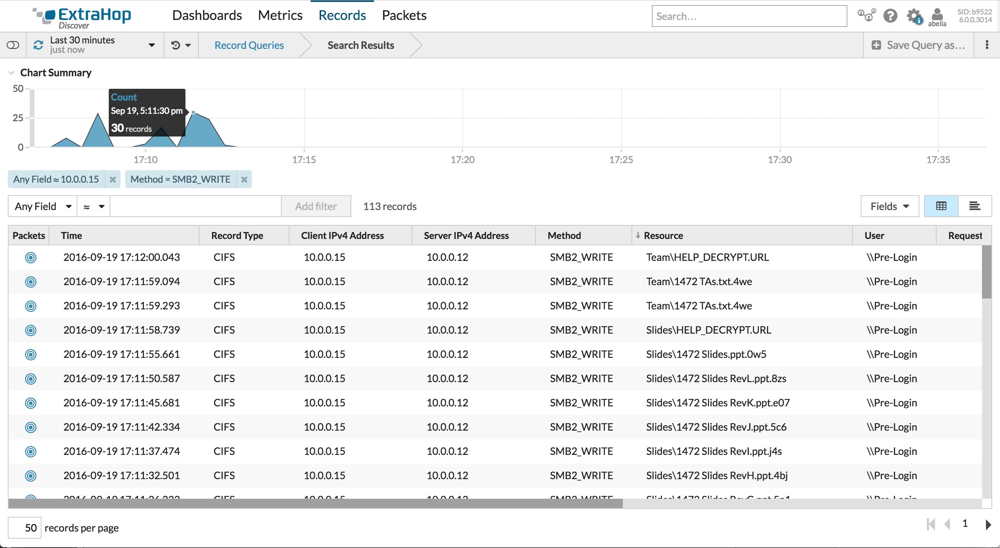
Ransomware offering provides layers of defense that work together, including:
-
Detection in flight: the solution provides a trigger that can help detect ransomware attacks in real-time. This functionality is based upon analyzing traffic from the SMB/CIFS network protocol.
-
Orchestrated mitigation: Through its REST API, the ExtraHop platform can kick off orchestrated mitigation actions in other security tools. For example, the IT team can use the firm’s detection to automatically block malicious IP addresses with their firewall appliance or quarantine infected clients with their network access control device.
-
Packet-based restoration: Precision Packet Capture capability can be leveraged to mitigate the damage caused by ransomware attacks. Packet capture starts automatically as soon as ransomware is detected, capturing the packets from which encrypted files can easily be restored.
Resources:
Ransomware detection bundle
Demo of how to use packet capture to recover ransomware-encrypted files.
Whitepaper: Detect and Stop Ransomware With a New Mitigation Approach (registration required)












 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter
