Cloud Technologies Develops Backup/DR Solution to Counter CryptoLocker Virus
Captures all applications data every 15 minutes
This is a Press Release edited by StorageNewsletter.com on February 21, 2014 at 2:47 pmCloud Technologies, Inc. has developed a backup and DR server that negates the impact of the CryptoLocker virus and other malware.
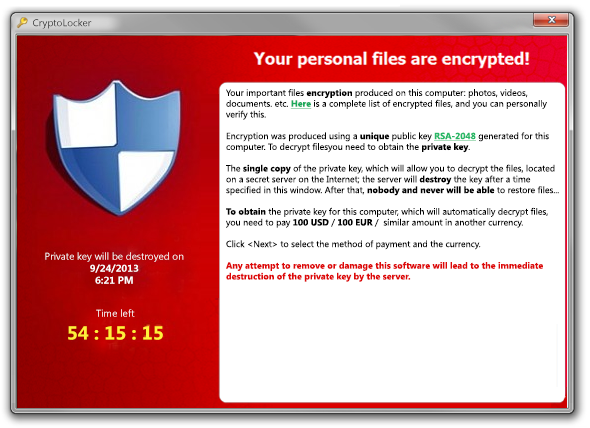
This virus is a variant of ransomware that encrypts computer files including any files on company servers to which the computer is connected. It then demands victims provide payment within a 96-hour period in order to decrypt and recover files. Failure to pay the ransom results in complete loss of all encrypted files. After seeing two of its customers attacked by CryptoLocker, the company developed a solution to enable its business clients to better protect themselves.
The server sits to the side of production servers and workstations taking and storing a snapshot copy of the HDD every fifteen minutes. This backup is replicated offsite daily, providing a second level of protection. If a business computer or server is attacked by CryptoLocker, it can restore data from the BDR from a period prior to infection, or can have a virtualized backup server available within minutes.
“Any business that has data worth retaining needs to utilize a BDR server to protect themselves, particularly if their work is time sensitive,” said Jeff Freeman, VP of IT, Cloud Technologies.
The server captures all aspects of a business’ servers, including systems, applications, configuration settings, services, and data. It backups SQL Server, Exchange, and SharePoint servers, as well as other application servers. In the event a business suffers a system failure, it facilitates a data restore and can restore a system to the same or to different hardware, or to a virtual environment.
Additionally, it is helping businesses to resume normal operations more expediently because users can connect to any of the backup images available and search to recover a single file or folder. Or, they can restore an entire data volume from a backup image file.
“For now the payment of ransom to the attackers and the resulting decryption key appear to be working to unlock the hostage data, but who knows how long that will work or what techniques these criminals will advance to next,” said Freeman. “It is important for businesses to stay educated and take proactive measures to protect data,” he said.














 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter

