Bloombase StoreSafe Got Ready for Security Intelligence Validation From IBM
To bolster key management capabilities
This is a Press Release edited by StorageNewsletter.com on April 12, 2017 at 2:35 pmBloombase StoreSafe‘s data-at-rest encryption solution is interoperable with the IBM Security Key Lifecycle Manager (SKLM) and is validated Ready for IBM Security Intelligence.
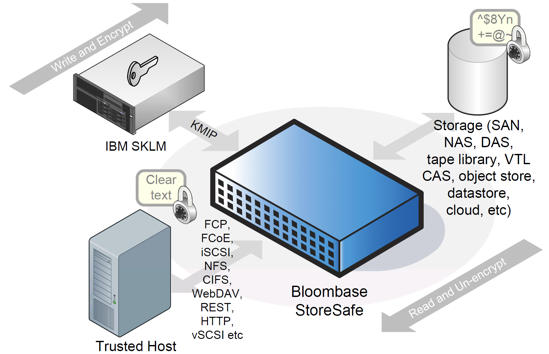
IBM SKLM Bloombase StoreSafe Integration
StoreSafe works across the full spectrum of storage systems from network and disk to virtual and cloud systems, whether it might be structured or unstructured data.
This combination ushers in enhanced convenience for enterprises looking for a powerful storage encryption solution that also offers convenient, centralized key management features. These features simplify the process of meeting of regulatory compliance.
Demand for off-premises and cloud-based storage continues unabated and remains a challenge for enterprises who need to manage the unceasing amount of business and mission-critical data being generated daily. This in turn places ever greater pressure on ensuring the protection and confidentiality of data, while remaining compliant with regulatory requirements.
StoreSafe data-at-rest encryption technology and Security Key Lifecycle Manager offers a potent combination of a turnkey, non-disruptive and application transparent stored data encryption solution with a powerful, centralized and automated key management system.
To the network, StoreSafe appears like a proxy and operates like a standards-based LUN, network share, backup target or RESTful service endpoint. When an application makes a storage request, StoreSafe automatically and transparently encrypts the plain-text payload with an encryption security key before it is persisted as a ciphertext on the physical storage medium. Similarly, this ciphertext is automatically decrypted on-the-fly as data is requested from the persistent storage medium. Applications are never aware that the persisted data is encrypted and therefore existing applications work as-is, without modification or adaptation. Furthermore, any unauthorized extraction of data yields only the encrypted ciphertext.
“The issue of protecting sensitive data is only going to get progressively more complicated as the amount of data and number of storage strategies increases. Bloombase StoreSafe works across the full spectrum of storage systems from network and disk to virtual and cloud systems, whether it might be structured or unstructured data,” said Sean Xiang, Bloombase CEO. “Combining this critical capability with an OASIS KMIP standards-based encryption key management system like the IBM Security Key Lifecycle Manager, gives enterprises unparalleled control over their security compliance processes.“
The management of the encryption and decryption security keys is automatically handled through Security Key Lifecycle Manager. It provides a centralized interface through which to administer the creation, importation, distribution, backup, archiving as well as management of key life-cycles. This implemented segregation of data encryption and security key management duties makes meeting regulatory standards that mandate protection and control of encryption keys such as the Payment Card Industry Data Security Standard (PCI DSS), Sarbanes-Oxley Act (SOX) and the Health Insurance Portability and Accountability Act (HIPAA) more convenient and cost effective.
Both StoreSafe and the SKLM are built upon FIPS 140-2 certified cryptographic modules and together, this combination allowsthe two companies to better address the needs of large-scale enterprises, particularly those in the banking, financial services, insurance and public sectors. These go-to-market solutions represent a straightforward means to enable organization-wide storage threat mitigation and regulatory compliance.
Bloombase showcased the StoreSafe data-at-rest encryption solution with SKLM at IBM InterConnect on March 19-23, 2017.
More information:
https://www-304.ibm.com/partnerworld/gsd/solutiondetails.do?solution=27715
https://www.bloombase.com/go/ibm.












 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter
