HubStor Enhanced Cloud Security and DR
Security feature protects data in cloud from malicious attacks at account level.
This is a Press Release edited by StorageNewsletter.com on March 10, 2017 at 2:34 pmHubStor Inc. announced a security feature that offers protection against malicious tampering at the account or subscription level.
Clients have the option of shadowing their data to a secondary account as a backup in the case the storage accounts in the primary account are deleted resulting in data loss.
When data is written to block blob storage in public cloud providers such as Microsoft Azure, at least three copies of the information are synchronously written. Additional levels of storage redundancy replicate the data to a secondary datacenter. However, if a hacker or malicious insider were to delete the storage account, then no amount of storage redundancy matters.
With firm’s shadow copy option, malicious users are unaware that a shadow copy exists. The solution transparently maintains replicas in a secondary account during the synchronization and archiving process. In the solution, data is preserved in a way that supports complete recovery – files, original metadata, folder structures, and permissions – from the blob storage alone. Thus, blob storage which is compressed with deduplication is the only cost factor in the secondary account; compute aspects of the tenant are necessary only in the primary account or in a recovery scenario.
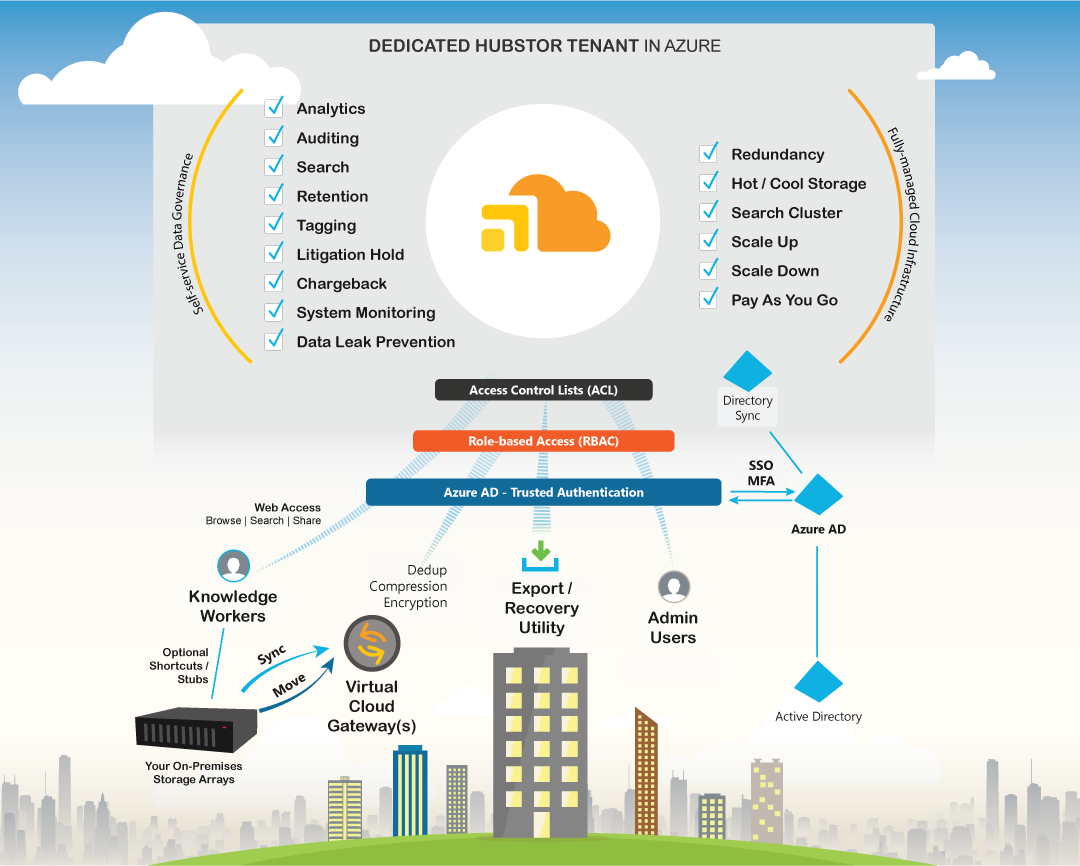
Click to enlarge
“The analysts at Storage Switzerland raised our awareness of data loss potential resulting from account tampering,” said Geoff Bourgeois, CEO, HubStor. “Approximately 60% of our clients run HubStor in their Azure account, so it helps that we offer added safeguards. Our goal is to provide the most in-depth security and data protection in the market.“
“I love this idea of a copy that has extra security around it,” said W. Curtis Preston, senior analyst, Storage Switzerland, LLC. “This protects against malicious and accidental deletion or encryption of the cloud copy, which is something we’re very concerned about.“
The company recommends that clients use the Azure Cool Storage for the shadow copy with the minimum redundancy configuration to contain cloud consumption costs.












 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter
